← Exams and Quizzes | Professional Exams →
Notice
If you get a question wrong, you can still click on the other answers. This will open up hints and explanations (if available), which will provide additional information. Exam should be 1 minute per question and please time accordingly.It is not required to have CompTIA A+ certification prior to obtaining CompTIA Network+ certification. It is recommended to have CompTIA A+ certification or the knowledge of the subject matter that is covered under A+ certification exam before taking Network+ certification exam. It is also recommended, but not required, that you have about 12 months of IT networking work experience.
Go to: Set I | Set II
CompTIA Network+ N10-007 - Set III
Congratulations - you have completed CompTIA Network+ N10-007 - Set III.
You scored %%SCORE%% out of %%TOTAL%%. With incorrect multiple attempts, your score is %%PERCENTAGE%%. Your performance has been rated as %%RATING%%
Question 1 |
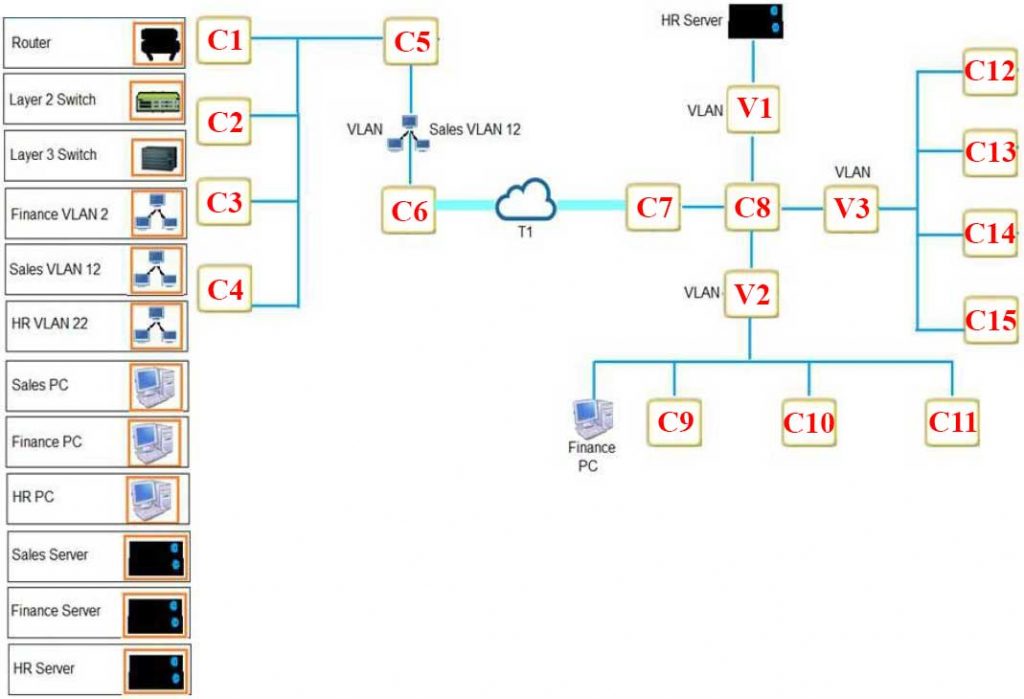
Requirements:
– The remote Sales Team must be able to connect to the corporate network.
– Each department must have ONLY two PCs and a server.
– Eqach department must be segmented from each other.
– The following VLANs have been designed:
— VLAN 2 Finance
— VLAN 12 Sales
— VLAN 22 Human Resources (HR)
– Routing for VLAN 12 is implemented on the router. Routing for VLAN 2 and VLAN 22 is on the switch.
According to the following network diagram for Company A, where would you place the Layer 2 and Layer 3 switches? Click on the image to enlarge.
A | Layer 2 at C7 and Layer 3 at C6 |
B | Layer 2 at C6 and Layer 3 at C6 |
C | Layer 2 at C8 and Layer 3 at C6 |
D | Layer 2 at C5 and Layer 3 at C6 |
E | Layer 2 at C10 and Layer 3 at C12 |
Question 2 |
A | VoIP endpoint |
B | Access point |
C | Router |
D | Range extender |
Question 3 |
A | Cold site |
B | Hot site |
C | Full backup |
D | Differential backup |
E | Incremental backup |
F | Warm site |
Question 4 |
A | Bad fiber switch |
B | Bend radius exceeded |
C | Fiber cable mismatch |
D | Fiber type mismatch |
Question 5 |
A | The WAP antenna is damaged |
B | The terminal emulation software is misconfigured |
C | The WAP transmitter light is dim |
D | The LWAPP image is installed on the WAP |
Question 6 |
A | Time |
B | Token |
C | Ticket |
D | Certificate |
Question 7 |
A | PC to switch |
B | PC to PC |
C | Router to modem |
D | Router to switch |
E | Switch to AP |
Question 8 |
A | L2TP |
B | SSH |
C | SNMP |
D | QoS |
Question 9 |
A | Overcapacity |
B | Channel overlapping |
C | DHCP exhaustion |
D | Interference |
Question 10 |
A | Transport |
B | Network |
C | Session |
D | Physical |
E | Data link |
Question 11 |
A | 2FFE::/16 |
B | FE80::/10 |
C | FEEF:/12 |
D | FF00::/8 |
Question 12 |
A | Baseline report |
B | Business continuity plan |
C | Rollback plan |
D | Vulnerability report |
Question 13 |
A | Switches packets between same subnets based on IP addresses |
B | Switches packets between different subnets based on IP addresses |
C | Switches packets within the same subnet based on MAC addresses |
D | Switches packets between different subnets based on MAC addresses |
Question 14 |
A | Hybrid |
B | Static |
C | Link state |
D | Distance vector |
Question 15 |
A | BGP |
B | RIP |
C | OSPF |
D | EIGRP |
Question 16 |
A | STP convergence |
B | Excessive bandwidth usage |
C | Power failure |
D | Broadcast storm |
Question 17 |
A | Wireless access point |
B | Wireless hub |
C | Wireless firewall |
D | Wireless bridge |
Question 18 |
Department-VLAN#-Subnet used
Marketing-20-192.168.20.0/28
Customer Service-25-192.168.20.64/28
Finance-30-192.168.30.0/28
WHSE-35-192.168.30.16/28
Sales-40-192.168.3.16/28
The users experiencing this issue need to be added to which of the following VLANs?
A | 25 |
B | 30 |
C | 40 |
D | 35 |
Question 19 |
A | Turn off SSID broadcasting for the executive’s access point |
B | Change the channel on the access point to channel 11 |
C | Turn off as many lights in the executive’s office as possible to reduce interference |
D | Replace the 802.11n access point in the office with an 802.11a access point |
Question 20 |
A | Honeypots |
B | Behavior-based IPS |
C | Signature-based IPS |
D | DMZ |
E | WPA2 |
Question 21 |
A | Star |
B | Bus |
C | Ring |
D | Mesh |
Question 22 |
A | Impersonation |
B | Privilege escalation |
C | Whaling |
D | Spear phishing |
Question 23 |
A | F-type |
B | BNC |
C | GBIC |
D | MT-RJ |
Question 24 |
A | DLP policy |
B | BYOD policy |
C | Remote access policy |
D | Incident response policy |
Question 25 |
A | CSU/DSU |
B | IDF |
C | MDF |
D | Switch |
Question 26 |
A | White/Orange, Orange, White/Green, Blue, White/Blue, Green, White/Brown, Brown |
B | White/Blue, Orange, White/Green, Blue, White/Orange, Green, White/Brown, Brown |
C | White/Green, Green, White/Blue, Blue, White/Orange, Orange, White/Brown. Brown |
D | White/Green, Green, White/Orange, Blue, White/Blue, Orange, White/Brown. Brown |
E | White/Orange, Orange, White/Brown, Blue, White/Blue, Green, White/Green, Brown |
Question 27 |
A | Username + password |
B | Key fob + ID card |
C | Smart card + PIN |
D | Fingerprint + retina scan |
Question 28 |
A | Utilize an SSH connection to the corporate server |
B | Allow RDP through an external firewall |
C | Connect utilizing client-to-site VPN |
D | Use TFTP to transfer files to corporate resources |
Question 29 |
A | IPsec |
B | 802.1x |
C | MIMO |
D | WPA |
E | FIFO |
Question 30 |
| Cable | Test | Result |
|---|---|---|
| 1.2 | Open | 7ft |
| 3.6 | Short | 7ft |
| 4.5 | Open | 7ft |
| 7.8 | Open | 7ft |
A | Cable Certifier |
B | OTDR |
C | Protocol Analyzer |
D | Punch Down Tool |
E | Crimper |
F | Toner Probe |
G | Multimeter |
Question 31 |
A | MIMO |
B | Channel bonding |
C | Increase the signal |
D | Disable SSID |
Question 32 |
A | DoS attacks |
B | Man-in-the-middle attacks |
C | Phishing |
D | Rogue access points |
Question 33 |
A | LC |
B | MT-RJ |
C | ST |
D | SC |
Question 34 |
A | Z-Wave |
B | 802.11n |
C | 802.11b |
D | 802.11ac |
E | 802.11g |
Question 35 |
A | Latency |
B | Security type mismatch |
C | Absorption |
D | Distance limitations |
Question 36 |
A | The web server is placed in bridge mode, the router is placed behind the web server, and the modem is placed behind the router |
B | The switch is placed in bridge mode, the modem is placed behind the router, and the router is placed behind the modem |
C | The router is placed in bridge mode, the modem is placed behind the router, and the web server is placed behind the modem |
D | The modem is placed in bridge mode, the router is placed behind the modem, and the web server is placed behind the router |
Question 37 |
A | WLAN |
B | Ring |
C | Star |
D | Bus |
Question 38 |
A | Add a layer 3 switch and create a VLAN. |
B | Add a firewall and implement proper ACL. |
C | Add a bridge between two switches. |
D | Add a router and enable OSPF. |
Question 39 |
A | Plenum Cat 5e |
B | PVC Cat 5 |
C | Plenum Cat 6a |
D | PVC Cat 7 |
Question 40 |
A | Cable tester |
B | OTDR |
C | Environmental monitor |
D | Punch down tool |
Question 41 |
A | SNMP |
B | SCTP |
C | Packet sniffer |
D | Simple Network Management Protocol (SNMP) |
E | DCCP |
Question 42 |
A | NS |
B | MX |
C | PTR |
D | CNAME |
E | SRV |
Question 43 |
A | 162.17.43.22 |
B | 152.119.25.213 |
C | 132.216.14.184 |
D | 172.23.226.34 |
Question 44 |
A | A network built with Logical Topology |
B | A network built with Star Topology |
C | A network built with Bus Topology |
D | A network built with Mesh Topology |
E | A network built with Ring Topology |
Question 45 |
A | Bus |
B | Partial mesh |
C | Hub and spoke |
D | Full mesh |
E | Ring |
Question 46 |
A | 192.168.2.1 |
B | 3ffe:1900:4545:3:200:f8ff:fe21:67cf |
C | 61.23.168.192.in-addr.arpa |
D | 00:f3:82:99:a2:b8 |
Question 47 |
A | Unidirectional |
B | Omnidirectional |
C | Yagi |
D | Parabolic |
Question 48 |
A | The network administrator should install and configure a DMZ server |
B | The network administrator should install and configure a network sniffer |
C | The network administrator should install and configure a traffic analysis server |
D | The network administrator should install and configure a syslog server |
Question 49 |
A | IPv6 |
B | EIGRP |
C | ICMP |
D | UDP |
Question 50 |
A | Refraction |
B | Distance |
C | Attenuation |
D | Reflection |
E | Absorption |
Question 51 |
A | IMAP |
B | POP3 |
C | NTP |
D | LDAP |
E | SMTP |
Question 52 |
A | Peer-to-peer |
B | Hybrid |
C | Point-to-point |
D | Point-to-multipoint |
Question 53 |
A | Layer 7 |
B | Layer 2 |
C | Layer 6 |
D | Layer 3 |
E | Layer 1 |
F | Layer 4 |
G | Layer 5 |
Question 54 |
A | Bridge |
B | Firewall |
C | Router |
D | IDS |
E | Managed switch |
Question 55 |
- AP encryption forced to WPA2-AES mode only
- MAC address filtering enabled with the following MAC address in the allow list: 00-ab-29-da-c3-40
Which is true about the above configuration?
A | An 802.11n compatible client can connect to the wireless network only if its MAC address is 00- ab-29-da-c3-40 and the encryption key is known by the client. |
B | Any 802.11g compatible client can connect to the wireless network if the encryption key is known by the client. |
C | An 802.11a compatible client can connect to the wireless network only if its MAC address is 00- ab-29-da-c3-40 and the encryption key is known by the client. |
D | Any 802.11b/g compatible client can connect to the wireless network if they support TKIP, the MAC address is 00-ab-29-da-c3-40, and the encryption key is known by the client. |
Question 56 |
A | Man-in-the-middle |
B | Social engineering |
C | Insider threat |
D | Logic bomb |
Question 57 |
SSID: SANUJA-WiFi
Signal: 5%
SNR: 2
A | Channel overlap |
B | Latency |
C | Incorrect antenna type |
D | Overcapacity |
Question 58 |
A | SLA |
B | NDA |
C | SOP |
D | AUP |
Question 59 |
A | Connection speeds decrease |
B | Throughput decreases |
C | Attenuation increases |
D | Cell size increases |
Question 60 |
A | Replace SFP with a new one |
B | Transpose the fiber pairs |
C | Fall back to the old switch |
D | Replace multimode with single-mode cable |
Question 61 |
A | Man-in-the-middle |
B | Evil twin |
C | Reflective |
D | DNS poisoning |
E | ARP poisoning |
F | Ransomware |
Question 62 |
A | Install antivirus software and set an ACL on the servers |
B | Create a VLAN for the unused ports and create a honeyspot on the VLAN |
C | Install a BPDU guard on switchports and enable STP |
D | Create a DMZ for public servers and secure a segment for the internal network |
Question 63 |
A | OC3 |
B | DS3 |
C | T3 |
D | E3 |
Question 64 |
A | The technician should connect the machine to its own separate switch. |
B | The technician should add a route in each virtual machine to the default gateway. |
C | The technician should configure a virtual switch. |
D | The technician should set up individual routes between the machines. |
Question 65 |
A | CHAP |
B | MS-CHAP |
C | MAC filtering |
D | Digital signatures |
Question 66 |
A | 1, 6, 11 |
B | 4, 8, 16 |
C | 2, 5, 10 |
D | 3, 13, 23 |
Question 67 |
A | Replace the switch uplink cable |
B | Install a UPS |
C | Install a new electrical circuit |
D | Install a new switch |
E | Install a power conditioner |
Question 68 |
A | MTU size greater than 12000 |
B | Commonly used on SAN |
C | MTU size greater than 1500 |
D | Commonly used on IaaS |
E | MTU size greater than 10000 |
Question 69 |
A | TPM |
B | IDS |
C | WAF |
D | WPA |
E | DLP |
Question 70 |
A | LC |
B | MT-RJ |
C | ST |
D | SC |
Question 71 |
A | Traffic shaping |
B | NTP |
C | NAC |
D | SDN |
E | ACL |
Question 72 |
A | Asset tracking tags |
B | Biometric locks |
C | Motion detection |
D | Smart card reader |
Question 73 |
A | TLS |
B | Split tunneling |
C | HTTPS |
D | Remote file access |
Question 74 |
A | Switch |
B | IPS |
C | Hub |
D | Router |
E | IDS |
F | Network tap |
Question 75 |
A | Hub |
B | Router |
C | Modem |
D | Switch |
Question 76 |
A | UTP |
B | Serial |
C | Multimode |
D | Coaxial |
Question 77 |
A | MPLS |
B | PPP |
C | ATM |
D | Frame relay |
Question 78 |
A | Subnetting |
B | Unicast |
C | Broadcast |
D | Multicast |
Question 79 |
A | Physical diagram |
B | Network baseline |
C | Change management log |
D | Logical diagram |
Question 80 |
A | Allow traffic from the wireless access point |
B | Block traffic from the wireless access point |
C | Packet filtering on the wireless access point |
D | Content filtering on the wireless access point |
Question 81 |
A | Use the 40MHz channels in the 2.4GHz band |
B | Enable access point antenna isolation |
C | Limit the clients to 802.11g compatible laptops |
D | Enable wireless multimedia (WMM) for QoS |
Question 82 |
A | Issue a new self-signed certificate. |
B | Remove unnecessary testing accounts. |
C | Generate new SSH host keys. |
D | Disable the HTTP port in the host firewall. |
E | Upgrade the firmware on the firewall. |
Question 83 |
A | 56:AD:BX:89:55:54 |
B | 44:98:3E:F8:33:23 |
C | AA:CE:58:FD:90:08 |
D | 94:9E:FE:EE:8C:DF |
Question 84 |
A | NAS |
B | iSCSI |
C | InfiniBand |
D | Fibre Channel |
Question 85 |
A | Signal-to-noise ratio |
B | Latency |
C | Packet loss |
D | Interference |
E | Attenuation |
F | Reflection |
Question 86 |
A | Rack diagram |
B | Network performance baseline |
C | IDF/MDF documentation |
D | Logical and physical diagrams |
Question 87 |
A | Blocking |
B | Forwarding |
C | Disabled |
D | Learning |
Question 88 |
A | TCP port 22 |
B | UDP port 53 |
C | UDP port 69 |
D | UDP port 22 |
E | TCP port 25 |
Question 89 |
A | Virtual IP |
B | Loopback IP |
C | Reserved IP |
D | Public IP |
Question 90 |
A | Used to verify functionality after a NIC is installed. |
B | Used to terminate a cable at a 110 block. |
C | Used to correct open short on a cable. |
D | Used to verify known good patch cables. |
E | Used to determine which port a CAT6 cable is connected. |
Question 91 |
A | Spanning tree |
B | BPDU guard |
C | Flood guard |
D | DHCP snooping |
Question 92 |
A | IPv4 to IPv6 tunnel |
B | MAC reservations |
C | IPsec |
D | EUI-64 |
E | APIPA |
Question 93 |
A | SaaS |
B | PaaS |
C | CASB |
D | IaaS |
Question 94 |
A | Ping |
B | Nessus |
C | Baseline analyzer |
D | Protocol analyzer |
Question 95 |
A | BPDU guard |
B | ARP protection |
C | DHCP snooping |
D | Spanning tree |
Question 96 |
A | LC |
B | ST |
C | MT-RJ |
D | SC |
Question 97 |
A | Key rotation |
B | Strong RC4 encryption |
C | AES encryption |
D | Shared secret keys |
E | MAC filtering |
Question 98 |
A | Log scanning |
B | Packet capturing |
C | Baseline review |
D | Port scanning |
Question 99 |
Requirements:
– The remote Sales Team must be able to connect to the corporate network.
– Each department must have ONLY two PCs and a server.
– Each department must be segmented from each other.
– The following VLANs have been designed:
— VLAN 2 Finance
— VLAN 12 Sales
— VLAN 22 Human Resources (HR)
– Routing for VLAN 12 is implemented on the router. Routing for VLAN 2 and VLAN 22 is on the switch.
According to the following network diagram for Company A, where should the router be palced? Click on the image to enlarge.
A | C5 |
B | C6 |
C | C8 |
D | C7 |
E | C10 |
Question 100 |
A | Change service port 636 to port 389 |
B | Verify the browser is using port 443 |
C | Check port 636 to see if it is being blocked |
D | Restart the web server |
Question 101 |
A | SNMPv3 |
B | CDP |
C | VTP |
D | IPSec |
Question 102 |
A | MITM |
B | Smurf attack |
C | Buffer overflow attack |
D | Social engineering |
E | NMAP |
Question 103 |
A | ACL allowing only HTTP |
B | ACL allowing only Telnet |
C | Out-of-band modem |
D | Out-of-band console router |
Question 104 |
A | Those servers have host-based firewalls |
B | Some of the servers are configured to use different gateways |
C | New servers are being provisioned in the cloud |
D | Part of the subnet is configured to use different VLANs |
Question 105 |
A | WAPs are transmitting on same channel |
B | WPA should be enabled |
C | PKI should be turned off |
D | WAP SSIDs are matching |
Question 106 |
A | lsshell |
B | ls |
C | env |
D | getargs |
E | lsenv |
Question 107 |
A | Network log files |
B | Logical diagrams |
C | Inventory management |
D | Change management records |
Question 108 |
A | Shared secret |
B | HTTPS server |
C | Soft spoken |
D | Private certificate |
Question 109 |
A | STP blocking |
B | IP addresses |
C | MTU mismatch |
D | Switching loop |
Question 110 |
A | The SET function pushes an alert to the MIB database |
B | A response message is sent from the agent to the manager |
C | The object identifier is modified and reported during the next monitoring cycle |
D | A trap message is sent via UDP to the monitoring workstation |
Question 111 |
A | Baseline review |
B | Log scanning |
C | Packet capturing |
D | Port scanning |
Question 112 |
A | nmap |
B | nslookup |
C | route |
D | pathping |
Question 113 |
A | Incorrect speed/duplex setting on the alarm device |
B | A missing route on the network routers |
C | Incorrect VLAN assignment on the router |
D | A missing route on the alarm device |
Question 114 |
A | ST |
B | SC |
C | LC |
D | MT-RJ |
Question 115 |
A | The SSIDs are incompatible and should be renamed. |
B | The channels are overlapping with other wireless networks and should be changed. |
C | The default idle period for logoff is too short and should be changed to a longer limit. |
D | The users have incompatible wireless network cards and should upgrade. |
Question 116 |
A | NTLM |
B | MS-CHAP |
C | CHAP |
D | Kerberos |
Question 117 |
A | Packet sniffer |
B | IDS |
C | Port scan |
D | IPS |
Question 118 |
A | Allow TCP port 3389 inbound |
B | Allow UDP port 3389 inbound |
C | Allow TCP port 3389 outbound |
D | Allow UDP port 3389 outbound |
Question 119 |
IP address: 172.16.204.12
Subnet Mask: 255.255.0.0
Default Gateway: 172.15.204.254
DNS address: 172.16.204.1
Broadcast address: 172.16.255.255
A | Default gateway |
B | IP address |
C | DNS address |
D | Broadcast address |
E | Subnet mask |
Question 120 |
A | 192.170.10.0/24 |
B | 172.16.20.0/30 |
C | 192.1.0.124/30 |
D | 10.10.50.0/30 |
E | 192.168.0.192/24 |
Question 121 |
A | 128 bits |
B | 32 bits |
C | 256 bits |
D | 64 bits |
Question 122 |
A | CARP |
B | ISAKMP |
C | PPTP |
D | FTP |
E | L2TP |
Question 123 |
A | ping |
B | nslookup |
C | route |
D | tracert |
E | pathping |
F | netstat |
G | tcpdump |
Question 124 |
A | Firewall |
B | Router |
C | Multiplayer switch |
D | Bridge |
Question 125 |
A | Fiber |
B | CAT3 |
C | CAT6a |
D | CAT5e |
Question 126 |
A | Increases port speed |
B | Allows another connection to the router |
C | Decreases bandwidth on a network |
D | Segments broadcast traffic |
Question 127 |
A | RIP |
B | EIGRP |
C | OSPF |
D | BGP |
Question 128 |
A | Syslog |
B | Environmental monitor |
C | Network map |
D | Placement map |
Question 129 |
A | Out-of-band management |
B | Client-to-site VPN |
C | HTTPS management URL |
D | Router ACL |
Question 130 |
A | WEP uses plain text |
B | WEP’s IV is too small |
C | WEP is not well supported |
D | WEP uses RC4 which is easily accessible and not secure |
Question 131 |
A | MPLS |
B | OSPF |
C | CSMA/CA |
D | CSMA/CD |
Question 132 |
A | Reflection |
B | Absorption |
C | Frequency mismatch |
D | Channel overlap |
Question 133 |
A | Datagram Transport Layer Security (DTLS) |
B | DNS |
C | DTLS |
D | TFTP |
E | SNMP |
Question 134 |
A | Multipath support |
B | Channel bonding |
C | Channel expansion |
D | Gigabit wireless bandwidth |
Question 135 |
A | HTTP |
B | RDP |
C | SMTP |
D | NTP |
← |
List |
→ |
| 1 | 2 | 3 | 4 | 5 |
| 6 | 7 | 8 | 9 | 10 |
| 11 | 12 | 13 | 14 | 15 |
| 16 | 17 | 18 | 19 | 20 |
| 21 | 22 | 23 | 24 | 25 |
| 26 | 27 | 28 | 29 | 30 |
| 31 | 32 | 33 | 34 | 35 |
| 36 | 37 | 38 | 39 | 40 |
| 41 | 42 | 43 | 44 | 45 |
| 46 | 47 | 48 | 49 | 50 |
| 51 | 52 | 53 | 54 | 55 |
| 56 | 57 | 58 | 59 | 60 |
| 61 | 62 | 63 | 64 | 65 |
| 66 | 67 | 68 | 69 | 70 |
| 71 | 72 | 73 | 74 | 75 |
| 76 | 77 | 78 | 79 | 80 |
| 81 | 82 | 83 | 84 | 85 |
| 86 | 87 | 88 | 89 | 90 |
| 91 | 92 | 93 | 94 | 95 |
| 96 | 97 | 98 | 99 | 100 |
| 101 | 102 | 103 | 104 | 105 |
| 106 | 107 | 108 | 109 | 110 |
| 111 | 112 | 113 | 114 | 115 |
| 116 | 117 | 118 | 119 | 120 |
| 121 | 122 | 123 | 124 | 125 |
| 126 | 127 | 128 | 129 | 130 |
| 131 | 132 | 133 | 134 | 135 |
| End |
Based on general knowledge and CompTIA guidelines published in 2020.
FAQ | Report an Error
Study outline at: CompTIA Exams Guide
Disclaimer: While every reasonable effort is made to ensure that the information provided is accurate, no guarantees for the currency or accuracy of information are made. It takes several proof readings and rewrites to bring the quiz to an exceptional level. If you find an error, please contact me as soon as possible. Please indicate the question ID-Number or description because server may randomize the questions and answers.