← Exams and Quizzes | Professional Exams →
Notice
If you get a question wrong, you can still click on the other answers. This will open up hints and explanations (if available), which will provide additional information. Exam should be 1 minute per question and please time accordingly.The two cores of A+ exams are very smiliar and the knowlagebase is linked across both exams. I highly recommend that you go through the questions for both core 1 and core 2 compeltely at least once before talking either exam. Then you can you back and study the questions intricately for one of the two cores before taking that specific section exam.
Go to: 220-1001 – Core 1
CompTIA 220-1002 - Core 2
Congratulations - you have completed CompTIA 220-1002 - Core 2.
You scored %%SCORE%% out of %%TOTAL%%. With incorrect multiple attempts, your score is %%PERCENTAGE%%. Your performance has been rated as %%RATING%%
Question 1 |
A | This account is designed to have the ability to set permissions for other users on the system. Users of this account have the capability to perform any operation or task on the system. |
B | This account is designed for users who require specific administrator rights or permissions. Users of this account are restricted from installing software but can change time zones. |
C | This account is designed for users who require temporary access to a computer and do not need to store user-specific settings. Users of this account have very limited permissions. |
D | This account is designed to provide basic permissions for completing common daily tasks. Users of this account are restricted from performing things like installing new software. |
Question 2 |
A | Secure the workstation in a limited access
facility. |
B | Reprimand the user and apply a content filter
to the user’s profile. |
C | Delete the bit torrent application and contact the affected copyright holders. |
D | Document the incident and purge all policy-violating materials. |
E | Immediately delete all unauthorized materials. |
Question 3 |
A | User Accounts |
B | Folder Options |
C | Sync Center |
D | Display Settings |
Question 4 |
A | Run Windows Update |
B | Disable all non-administrator accounts. |
C | Disable network cards |
D | Disable System Restore |
E | Run the CHKDSK /R command |
Question 5 |
A | Processor scheduling |
B | Page-file size |
C | Data execution prevention |
D | Visual effects |
Question 6 |
A | Ghost |
B | Robocopy |
C | Sysprep |
D | Image Copy |
E | Image Clone |
Question 7 |
A | Microsoft OneDrive |
B | Google Cloud Platform |
C | iCloud |
D | Local NAS |
Question 8 |
A | Compatibility mode |
B | Windows Firewall |
C | OneDrive |
D | PowerShell |
Question 9 |
A | Memory |
B | Hard drive/SSD |
C | CD-ROM |
D | Driver |
Question 10 |
A | Using msconfig Services tab. |
B | Using msconfig Tools tab. |
C | Using msconfig General tab. |
D | Using msconfig Boot tab. |
Question 11 |
A | Computer Management |
B | Disk Cleanup utility |
C | Format command |
D | Disk Management |
Question 12 |
A | DxDiag |
B | perfmon.msc |
C | gettingstarted |
D | Regedit |
E | Ipconfig |
Question 13 |
A | RD |
B | MD |
C | CD |
D | SD |
E | dir |
Question 14 |
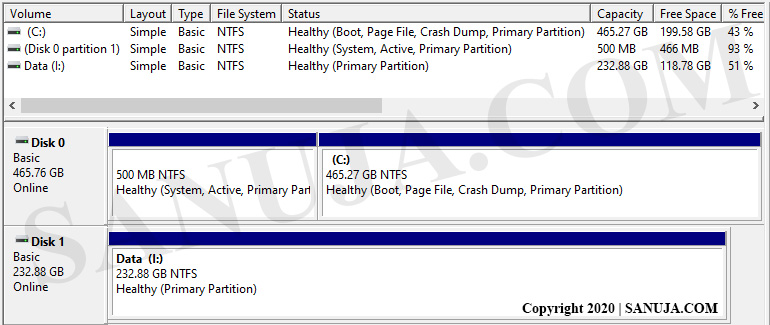
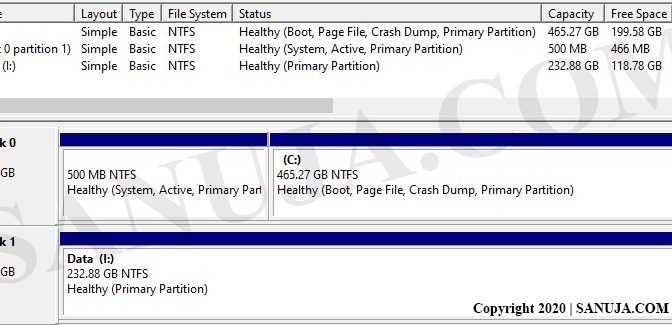
A | FAT32 partition |
B | Primary partition |
C | Healthy partition |
D | Disk 0 |
E | Disk 1 |
Question 15 |
A | defrag |
B | chkdsk |
C | cleanmgr |
D | diskpart |
Question 16 |
A | HKEY_USERS |
B | HKEY_CLASSES_ROOT |
C | HKEY_LOCAL_MACHINE |
D | HKEY_CURRENT_CONFIG |
Question 17 |
A | WWF |
B | CompTIA |
C | IBM |
D | Apple |
E | Microsoft |
Question 18 |
A | The 64-bit architecture has an upper RAM limit of 128 GB. |
B | The 32-bit CPUs can only address a maximum of 4 GB of RAM, but 64-bit CPUs can address many TBs of RAM. |
C | The 64-bit version is also known as x86. |
D | The 32-bit architecture has an upper RAM limit of 64 GB. |
E | Windows 10 only comes in 64-bit version. |
Question 19 |
A | perfmon |
B | msconfig |
C | regd |
D | dxdiag |
E | taskmgr |
Question 20 |
A | Restart the tablet |
B | Calibrate the touchscreen sensor |
C | Disconnect and then reconnect the stylus |
D | Disable and then reenable Bluetooth |
Question 21 |
A | Remediate infected systems. |
B | Enable System Restore. |
C | Schedule scans and run updates. |
D | Quarantine infected systems. |
E | Disable System Restore. |
F | Identify malware symptoms. |
Question 22 |
A | /B |
B | /sub-1 |
C | /D |
D | /DCOPY:T |
E | /S |
F | /E |
Question 23 |
A | Document the changes and perform the work. |
B | Submit the changes to the change board for approval. |
C | Obtain end-user acceptance for the proposed changes and submit a change plan for additional work. |
D | Escalate to stakeholders and obtain override approval for out-of-scope changes. |
E | Notify the change team of the changes needed and perform the changes. |
Question 24 |
A | Msconfig |
B | Task Manager |
C | Disk Management |
D | Administrative Tools |
Question 25 |
A | tokens |
B | passwords |
C | root CA |
D | keys |
Question 26 |
A | Volume license |
B | Open license |
C | Corporate license |
D | Personal license |
E | Enterprise license |
Question 27 |
A | diskmgmt.msc |
B | setuperr.log |
C | setupact.log |
D | unattend.xml |
Question 28 |
A | Msconfig |
B | Task Manager |
C | Chkdsk |
D | System Information |
Question 29 |
A | Move the folder to another location on the server, and notify the local authorities |
B | Ask the owner to move the files from the server to a local computer |
C | Promptly notify the administrator's immediate supervisor |
D | Rename the folder on the server, and notify the information security officer |
Question 30 |
A | RDP |
B | SSH |
C | Telnet |
D | VNC |
Question 31 |
A | chkdsk C: /I |
B | chkdsk C: /F |
C | chkdsk C: /R |
D | chkdsk C: /C |
E | chkdsk /sec |
Question 32 |
A | Power cycle the network appliances. |
B | Reconfigure the gaming consoles' network interfaces. |
C | Replace the router with an upgraded unit. |
D | Factory reset the gaming consoles. |
E | Replace the IP camera system with a new one. |
F | Configure router QoS engine with service priority for gaming applications. |
Question 33 |
A | Check the temperature at which the solder should be applied. |
B | Call the building supervisor to make sure there is enough solder for others. |
C | Consult the MSDS for the solder spool. |
D | Do not attempt to repair a motherboard. It is better to buy a new one. |
Question 34 |
A | MMC |
B | Task Manager |
C | Control Panel |
D | Command Prompt |
Question 35 |
A | Apply a screen lock after x minutes of non-use and set login time restrictions for after hours. |
B | Run a screensaver after one minute of nonuse and a fingerprint lock for after hours. |
C | Display a message on lock screen advising users how importnat to lock their computer. |
D | Set a strong password that requires a renewal every 30 days. |
E | Create a group policy to set minimum password standards. |
Question 36 |
A | Computer Management |
B | Task Manager |
C | Tasklist |
D | Control Panel |
E | Force quit |
Question 37 |
A | Secondary partition |
B | Extended partition |
C | Primary partition |
D | USB drive |
E | Dynamic partition |
Question 38 |
A | Seat license |
B | Open source license |
C | Enterprise license |
D | Commercial license |
Question 39 |
A | Group Policy |
B | Folder Redirection |
C | Home Folder |
D | Security Groups |
Question 40 |
A | SSO |
B | Secure Shell |
C | Propagation |
D | Inheritance |
E | MFA |
Question 41 |
A | Android OS is open source but the iOS is closed source and owned by Apple Inc. |
B | Both Android OS and iOS can run on almost all handheld modern electronic devices. |
C | A consumer can exchange the apps (applications) between Andorid OS and iOS. |
D | Unlike Android OS, Apple OS allow you to customize the user interface using a system called Launcher. |
Question 42 |
The Windows Boot Configuration Data File Is Missing Required Information.
A | bootrec /fixmbr |
B | bootrec /fixboot |
C | boot\bcd |
D | bootrec /restore |
E | bootrec /rebuildbcd |
Question 43 |
A | chkdsk /F |
B | diskpart |
C | robocopy |
D | tracert /w |
Question 44 |
A | Ctrl+Alt+Del |
B | Windows+R |
C | Windows+L |
D | Windows+M |
E | Windows+pause break |
Question 45 |
A | Standard format |
B | Low-level format |
C | Degauss |
D | Drive wipe |
Question 46 |
A | worm |
B | spyware |
C | trojan |
D | spam bot |
Question 47 |

A | This PC must be running Windows 7 because only Windows 7 utilities can generate this snapshot. |
B | This PC Is connected to the LAN via both wired and wireless LAN interfaces. |
C | This PC is running low on memory resources with a very high percentage is committed. |
D | This PC is connected to a domain called SANUJA and NetBIOS device name is ASUS. |
E | This PC has two LAN interface cards; wired and wireless. But only the wired LAN is connected to a network. |
Question 48 |
A | Applets |
B | Snap-ins |
C | Directories |
D | Files |
Question 49 |
A | Systemroot |
B | Program Files (x86) |
C | System32 |
D | Program Files |
Question 50 |
A | Logon times |
B | UEFI boot mode |
C | User access control |
D | Date and time |
Question 51 |
A | Server and domain |
B | Server and gateway |
C | IP address and domain |
D | IP address and DNS |
Question 52 |
A | boot |
B | Windows |
C | System32 |
D | Users |
E | Program Files |
Question 53 |
A | Msconfig |
B | Task Manager |
C | Safe Mode |
D | ifconfig |
Question 54 |

A | Windows Task Manager |
B | Performance Monitor |
C | Windows Registry |
D | Windows Task Scheduler |
E | Windows Control Panel |
Question 55 |
A | Boot the workstation in safe mode with Command Prompt and enable Driver Verifier with standard settings |
B | Boot the workstation in safe mode with networking and install the latest stable graphics driver |
C | Boot the workstation in safe mode and disable the graphics driver system tray menu |
D | Boot the workstation in safe mode and disable Windows driver signing requirements |
Question 56 |
A | Remove and reinstall the application |
B | Hard reset the cell phone |
C | Close all running applications |
D | Reconnect the wireless network connection |
Question 57 |
A | Within the Start menu |
B | On the taskbar |
C | In the System Properties dialog box |
D | In the System32 folder |
Question 58 |
A | It may result in damage to the device. |
B | It may lead to instability issues. |
C | It may result in random reboots. |
D | It may interfere with other signed drivers installed on the device. |
Question 59 |
A | Rooting |
B | VirusBarrier |
C | Grant superadmin |
D | Jailbreaking |
E | Open shell access |
Question 60 |
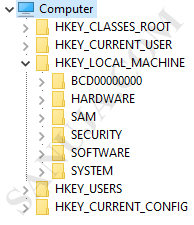
A | Windows Control Panel |
B | Windows Task Scheduler |
C | Windows Registry |
D | Windows Task Manager |
E | MS-DOS Control Panel |
Question 61 |
A | Ls |
B | Passwd |
C | Chown |
D | Chmod |
E | dirc |
Question 62 |
A | SSO |
B | Secure Shell |
C | Inheritance |
D | MFA |
E | Propagation |
Question 63 |
A | Refer your panicking Supervisor and co-workers to professional counseling services. |
B | Quit your job because of this work environment is toxic. |
C | Stay calm and do your job to best of your ability. |
D | Take everyone out to lunch get their mind off of the problem. |
E | Request that you need to speak to a senior Supervisor. |
Question 64 |
A | Enterprise license |
B | Open source license |
C | Seat license |
D | Commercial license |
Question 65 |
A | Spear phishing |
B | Spoofing |
C | Whaling |
D | Impersonation |
Question 66 |
A | dir /d |
B | dir /? |
C | dir -1 |
D | dir /a |
E | dir /o |
Question 67 |
A | Power users |
B | Standard user |
C | Administrator |
D | Guest |
Question 68 |
A | taskkill |
B | process -k |
C | deltask |
D | delprocess |
E | process -del |
Question 69 |
A | ipconfig /all |
B | ifconfig |
C | ls |
D | ipaddr /all |
E | chown |
Question 70 |
A | Do nothing. |
B | Educate the customer on how to avoid malware. |
C | Replace the hard drive. |
D | Reinstall the antivirous and malware software. |
E | Change the user account permissions to restrict access. |
Question 71 |
A | PXE |
B | Multi-boot |
C | Dynamic |
D | GPT |
Question 72 |
A | Use the local client certificate for server authentication |
B | Disable logon time restrictions |
C | Put the terminal server into the routers DMZ |
D | Block all unused ports on the LAN smart switch |
E | Enforce password complexity |
F | Change the default access port |
Question 73 |
A | Component Services |
B | System Configuration |
C | Local Users and Groups |
D | Security Policy |
Question 74 |
A | Power user |
B | Administrator |
C | Domain Admin |
D | Guest |
Question 75 |
A | FAT32 |
B | GPT |
C | Dynamic drive |
D | MBR |
Question 76 |
A | WLAN |
B | WWAN |
C | 5G LTE |
D | VPN |
E | VLAN |
Question 77 |
A | Event Viewer |
B | Task Manager |
C | Services |
D | Task Scheduler |
Question 78 |
A | CD |
B | MD |
C | SD |
D | dir |
E | RD |
Question 79 |
A | Rollback OS and driver updates. |
B | Disconnect the computer from the office network. |
C | Run a System Restore. |
D | Reboot the computer in order to make sure all other programs are terminated. |
E | Research the virus and how to remove it. |
Question 80 |
A | Google Android version may be the same but the core APKs are different from manufacture to manufacture. |
B | One of the users most likely is not on Android 10 even though he/she thinks they are on Android 10. |
C | The Android Kernel version must be different bvetwen the manufactures. |
D | Each manufacturer has their own custom apps which change the behaviour of the GUI. |
E | Each manufacturer has their own customized Launchers that modify the GUI. |
Question 81 |
A | incident response |
B | Incident Response Life Cycle |
C | MSDS |
D | chain of custody |
E | official documentation |
Question 82 |
A | Reset the PC to its factory conditions. Perform the OS upgrade again |
B | Update the SATA controller driver from the manufacturers website |
C | Perform a full backup and replace the hard drive |
D | Roll back the OS upgrade. Continue using the older version of Windows |
Question 83 |
A | Ask Sara why she has this type of folder on her work computer. |
B | Open the folder to investigate the content, but do not open the images. |
C | Open the folder and enjoy the images. |
D | Contact the Manager of the company immediately. |
E | Install the software and ignore the folder. |
Question 84 |
A | devmgmt.msc |
B | perfmon.exe |
C | systempropertiesadvanced.exe |
D | eventvwr.msc |
E | wintask |
Question 85 |
A | .apk |
B | .exe |
C | .ipa |
D | .sdk |
E | api |
Question 86 |
A | Business processes |
B | End-user acceptance |
C | Backout plan |
D | Request for proposal |
E | Risk analysis |
F | Plan for change |
Question 87 |
A | exFAT |
B | FAT32 |
C | ext4 |
D | NTFS |
Question 88 |
A | cp and rm |
B | pad and chmod |
C | sudo and vi |
D | ps and kill |
E | ls and chown |
Question 89 |
A | MBR can create multiple partitions without any issues but GPT has a limit of four partitions per drive. |
B | GPT is an older method of partitioning a disk that no longer in used and replaced by MBR. |
C | MBR is only used by Microsoft products while GPT is only used by Linux and MacOS. |
D | MBR drive format does not support drives over 4TB while GPT would be able to partition larger drives over 4TB. |
Question 90 |
A | Implement a fire suppression system. |
B | Plug and check if the equipment is working. |
C | Increase the closet's airflow. |
D | Set up dehumidifiers. |
E | Install grounding bars. |
Question 91 |
A | Support for single large files over 4GB. |
B | Compatibility across different OS providers such as Windows, Linux and Mac. |
C | Low drive failure rates. |
D | Better driver encryption and support for cryptology. |
E | Lower power consumption. |
Question 92 |
A | hives |
B | winreg |
C | registry |
D | reg |
E | regedit |
Question 93 |
A | setupact.log |
B | diskmgmt.msc |
C | setuperr.log |
D | unattend.xml |
Question 94 |
A | Rooting |
B | VirusBarrier |
C | Grant superadmin |
D | Jailbreaking |
E | Open shell access |
Question 95 |
A | ping |
B | ipconfig |
C | ipconfig /all |
D | netstat |
E | ipconfig /renew |
Question 96 |

A | Disk Management |
B | DiskPart |
C | Gparted |
D | Event Viewer |
E | System Management |
Question 97 |
A | NTFS supports larger file sizes. |
B | NTFS supports larger volumes. |
C | NTFS supports more file formats. |
D | NTFS supports file encryption. |
Question 98 |
A | Android OS |
B | Windows 10 |
C | macOS |
D | Ubuntu OS |
E | Chrome OS |
Question 99 |
A | Windows 10 |
B | Android |
C | Windows 98 |
D | iOS |
E | macOS |
Question 100 |
A | Dxdiag |
B | Sigverif |
C | Ping |
D | Msconfig |
E | Regedit |
Question 101 |
A | Domain name, location, IP address |
B | Location, RFID |
C | Domain name, location, asset ID |
D | Asset ID, MAC address |
Question 102 |
A | \%systemroot%\Windows |
B | \%systemroot%\Windows\System32\Con
fig |
C | \%systemroot%\System32 |
D | \%systemroot%\System32\Config |
Question 103 |
A | Defrag the hard drive. |
B | Convert the file system to NTFS. |
C | Change the location of the system32 |
D | Disable UAC. |
E | Enable TPM in the BIOS/UEFI. |
Question 104 |
A | Session hijacking |
B | Phishing |
C | Brute force |
D | DDoS |
E | Malicious attack |
Question 105 |
A | Mobile Device Management (MDM) policies |
B | Anti-virous and anti-malware software intefrence. |
C | VPN configuration or inactive VPN. |
D | Unsigned drivers or untrusted software. |
Question 106 |
A | Setup log |
B | Security log |
C | Application log |
D | System log |
E | Tasker log |
Question 107 |
A | Run a driver update check for the specified software. |
B | Invoice the customer. |
C | Document your solution. |
D | Move on to the server to a different node or VLAN on the network. |
Question 108 |
A | It would be nearly impossible to recover the user data since the primary drive conating the OS is required to access the seconday drive. |
B | It would be fairly easy as long as the secondary hard drive is not encrpyted. |
C | You can go to BIOS and make the secondary drive as the primary boot drive to download the data. |
D | It would be very difficualt and will require specialized laborotory to recover the data. |
Question 109 |
A | Check for and apply software updates |
B | Perform repair installation on the application |
C | Rebuild the users mail profile |
D | Add the user to the local administrators group |
Question 110 |
A | Timeset |
B | Net time |
C | Time |
D | Net timer |
E | Net time set |
Question 111 |
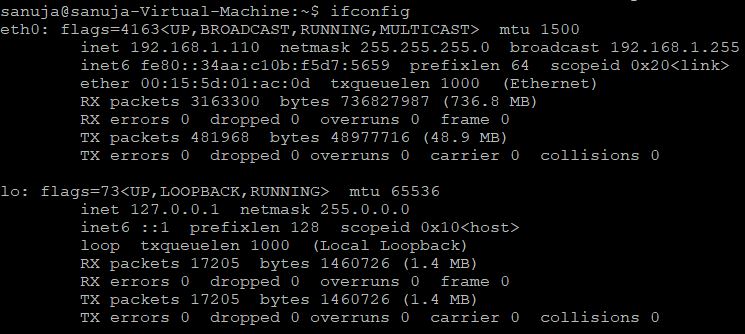
A | Ubuntu |
B | iOS |
C | Windows 10 |
D | Mac OS |
E | Android |
Question 112 |

A | Disk 0 - 500 MB NTFS |
B | Disk 1 |
C | Disk 0 - 465.27 MB NTFS |
D | None of the partitions can be dismounted without crashing the system. |
Question 113 |
A | Boot into the Safe Mode. |
B | Run Chkdsk. |
C | Run Msconfig. |
D | Check the System log. |
E | Remove the network card. |
Question 114 |
A | Trusted Mobile Platform (TMP) |
B | App Store |
C | iTunes |
D | Google Play |
E | Spotlight |
Question 115 |
A | man ipconfig |
B | ipconfig help |
C | ipconfig /? |
D | ipconfig man |
Question 116 |
A | BitLocker |
B | Windows administrator user account |
C | Windows user account |
D | BitDefender |
E | BIOS password |
Question 117 |
A | Look for program features and the minimum hardware requirements. |
B | Verify that the install is allowed under the company’s licensing agreements. |
C | Read the manual on how HR is going to use the software. |
D | Update the Windows drivers on the computer. |
Question 118 |
A | Pro |
B | Standard |
C | Home |
D | Enterprise |
Question 119 |
A | Organization security and content policies are not part of the majority of government organizations. |
B | Organization security and content policy typically do not apply to executive staff. |
C | Organization security and content policy supersede all other legal policies of the country which the company operates. |
D | Organization security and content policy must include explicit punishment guidelines for employees who do not follow the guidelines. |
E | Organization security and content policy must follow the legal policies of the country which the company operates. |
Question 120 |
A | NTFS |
B | exFAT |
C | FAT16 |
D | FAT32 |
Question 121 |
A | .py1 |
B | .ps1 |
C | .py |
D | .ps |
E | .vbs |
Question 122 |
A | CONVERT |
B | CHKNTFS |
C | NETDOM |
D | IPCONFIG |
Question 123 |
A | First left |
B | First right |
C | None of the answers are correct |
D | Center |
Question 124 |
A | Install an intrusion detection system (IDS). |
B | Disable the SSID broadcast. |
C | Install an antivirus on the main server. |
D | Install a firewall and enforce rules. |
E | Disconnect the Internet connection to the LAN. |
Question 125 |
A | Windows 10 Home |
B | Windows 10 Pro |
C | Windows 10 Enterprise |
D | Windows 10 Education |
Question 126 |
A | Power plans |
B | Display properties |
C | Task Manager |
D | Device Manager |
E | TRIM |
Question 127 |
A | Windows Registry |
B | System Restore |
C | Reset Your PC |
D | File History |
E | Startup Repair |
Question 128 |
A | Install to a secondary internal HDD |
B | Install to a DVD-RW |
C | Install to a USB drive |
D | Install to a network drive |
Question 129 |
A | mtg |
B | secpol.msc |
C | devmgmt.msc |
D | MMC |
E | CMD |
Question 130 |
A | startup.exe |
B | system32.exe |
C | winload.exe |
D | setup.exe |
E | shell.adb |
Question 131 |
A | Services console |
B | Device Manager |
C | File Explorer |
D | Windows Registry |
E | Task Manager |
Question 132 |
A | Corporate license |
B | Personal license |
C | Open license |
D | Enterprise license |
E | Volume license |
Question 133 |
A | Active Directory Policy |
B | Site Policy |
C | Local Security Policy |
D | OU Group Policy |
Question 134 |
A | 1 GB |
B | 4 GB |
C | 2 GB |
D | 6 GB |
E | 512 MB |
Question 135 |
A | CD |
B | Dir |
C | MD |
D | Ping |
E | Ver |
Question 136 |
A | DDoS attack |
B | Social engineering |
C | Session hijacking attack |
D | Brute force attack |
E | Phishing attack |
Question 137 |
A | Taskkill |
B | Force quit |
C | Mac Management |
D | Time Machine |
E | Task Manager |
Question 138 |
A | 1 GB |
B | 512 MB |
C | 4 GB |
D | 2 GB |
E | 6 GB |
Question 139 |
A | Reboot the network cameras. |
B | Uninstall firewall applications and disable all firewall rules. |
C | Add the necessary port numbers to the exceptions list of Windows Defender firewall. |
D | Reboot the router. |
E | Revert the computer back to the last stable Windows service pack. |
Question 140 |
A | MS PowerPoint |
B | MS Excel |
C | CMD |
D | Notepad |
E | MS Word |
Question 141 |
A | Pausing printing |
B | Adding ports |
C | Enabling sharing |
D | Modifying spool settings |
Question 142 |
A | .bat |
B | .sh |
C | .js |
D | .vbs |
Question 143 |
A | Performance Monitor |
B | Local Security Policy |
C | Component Services |
D | Device Manager |
Question 144 |
A | Reinstall the CAD program. |
B | Upgrade the video drivers. |
C | Replace the hard drive. |
D | Reinstall the Windows OS. |
E | Check the RAM configuration. |
Question 145 |
A | Windows user account authentication is more secure than BitLocker. |
B | Windows user account authentication can only be used with a Windows Server Domain Controller. |
C | BitLocker can encrypt hard drives and protect user content from unauthorized access. |
D | Unlike Windows user accounts, BitLocker is available on multiple platforms such as Ubuntu, iOS and Android. |
E | Windows user account authentication uses the TPM chipset on the motherboard to encrypt user data. |
Question 146 |
A | Copy system files. |
B | Defragment the drive. |
C | Run chkdsk. |
D | Partition the drive. |
Question 147 |
A | Ask the customer to use a different web browser. |
B | Delete and clear Java Temporary Internet Files. |
C | Ask the customer to find an application that does not use Java. |
D | Reinstall Java on the affected workstation. |
Question 148 |
A | C:\Documents and Settings\%username%\Documents |
B | C:\Users\%root%\Documents |
C | C:\Users\%username%\Documents |
D | C:\Users\System32\Documents |
Question 149 |
A | DOS |
B | PowerShell |
C | Command Prompt |
D | VB Script |
Question 150 |
A | Microsoft |
B | IBM |
C | WWF |
D | CompTIA |
E | Apple |
Question 151 |
A | Completely erase the old drive prior to disposal. |
B | Destroy the old hard drive by physically mutilation and cutting the platters into small pieces. |
C | Open the old hard drive case and use ESD to destory the circuitry. |
D | Format the old hard drive multiple times before deposal. |
Question 152 |
A | Sync Center |
B | Windows Defender |
C | HomeGroup |
D | Windows Domain |
E | Windows Aero |
Question 153 |
-Often the website is responding slowly.
-Often the website is unresponsive.
-Some users have problems accessing the website.
-When the webserver is ping from a computer within the same LAN, the ping timeout or the ping time is usually high.
A | DDoS attack |
B | HTTP attack |
C | Brute force attack |
D | Session hijacking attack |
E | Malicious attack |
Question 154 |
A | Enforce password history |
B | Minimum password length |
C | Minimum password age |
D | Complexity requirements |
Question 155 |
A | sbin |
B | ls |
C | bash |
D | cat |
Question 156 |
A | Contact HR immediately and seek advice. |
B | Before you take any actions, contact the CEO secretly and advise him/her that their IT account is being deleted. |
C | Before you take any actions, contact the CEO in writing or by email and advise him/her that their IT account is being deleted. |
D | Contact a lawyer as this breaches the professional conduct policies. |
E | If the IT Manager has the proper authority and documentation, perform the deletion task to the best of your ability. |
Question 157 |
A | Windows Update is running. |
B | Hyper-Threading has been disabled. |
C | Virus infection of the C drive. |
D | Drivers are being downloaded by the Device Manager. |
E | The printing system is running. |
Question 158 |
A | chkdsk C: /C |
B | chkdsk C: /R |
C | chkdsk C: /I |
D | chkdsk /sec |
E | chkdsk C: /F |
Question 159 |
A | Domain-level group policies |
B | Local-level firewall policies |
C | Antivirus domain-level policies |
D | Network-level firewall policies |
E | Local-level user policies |
Question 160 |
A | Recover |
B | Replace |
C | REM |
D | Convert |
E | Rebuild |
Question 161 |
A | /S |
B | /B |
C | /sub-1 |
D | /D |
E | /RCOPY |
F | /DCOPY:T |
Question 162 |
A | Unicode |
B | EBCDIC |
C | PS1 |
D | ASCII |
E | ITU-T |
Question 163 |
A | Initialize the drive. |
B | Visit the website of the SSD manufacturer for firmware updates or contact the manufacturer. |
C | Unplug the power and re-plug it without powering down the workstation. |
D | Run Windows updates. |
E | Format and partition the drive. |
Question 164 |
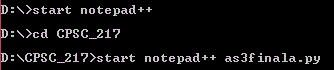
A | Execute the file as3final.py in notepad++ |
B | Change the file name from notepad to as3final.py |
C | Append the file name as3final.py to as3final.py by combing notepad and as3final terms. |
D | Open file as3final.py file using the program notepad++ |
E | Execute the file notepad++ in as3final.py |
Question 165 |
A | loop , run |
B | conditional statement , run |
C | conditional statement , iteration |
D | loop , iteration |
← |
List |
→ |
| 1 | 2 | 3 | 4 | 5 |
| 6 | 7 | 8 | 9 | 10 |
| 11 | 12 | 13 | 14 | 15 |
| 16 | 17 | 18 | 19 | 20 |
| 21 | 22 | 23 | 24 | 25 |
| 26 | 27 | 28 | 29 | 30 |
| 31 | 32 | 33 | 34 | 35 |
| 36 | 37 | 38 | 39 | 40 |
| 41 | 42 | 43 | 44 | 45 |
| 46 | 47 | 48 | 49 | 50 |
| 51 | 52 | 53 | 54 | 55 |
| 56 | 57 | 58 | 59 | 60 |
| 61 | 62 | 63 | 64 | 65 |
| 66 | 67 | 68 | 69 | 70 |
| 71 | 72 | 73 | 74 | 75 |
| 76 | 77 | 78 | 79 | 80 |
| 81 | 82 | 83 | 84 | 85 |
| 86 | 87 | 88 | 89 | 90 |
| 91 | 92 | 93 | 94 | 95 |
| 96 | 97 | 98 | 99 | 100 |
| 101 | 102 | 103 | 104 | 105 |
| 106 | 107 | 108 | 109 | 110 |
| 111 | 112 | 113 | 114 | 115 |
| 116 | 117 | 118 | 119 | 120 |
| 121 | 122 | 123 | 124 | 125 |
| 126 | 127 | 128 | 129 | 130 |
| 131 | 132 | 133 | 134 | 135 |
| 136 | 137 | 138 | 139 | 140 |
| 141 | 142 | 143 | 144 | 145 |
| 146 | 147 | 148 | 149 | 150 |
| 151 | 152 | 153 | 154 | 155 |
| 156 | 157 | 158 | 159 | 160 |
| 161 | 162 | 163 | 164 | 165 |
| End |
Based on general knowledge and CompTIA guidelines published in 2020.
FAQ | Report an Error
Disclaimer: While every reasonable effort is made to ensure that the information provided is accurate, no guarantees for the currency or accuracy of information are made. It takes several proof readings and rewrites to bring the quiz to an exceptional level. If you find an error, please contact me as soon as possible. Please indicate the question ID-Number or description because server may randomize the questions and answers.