← Exams and Quizzes | Professional Exams →
Notice
If you get a question wrong, you can still click on the other answers. This will open up hints and explanations (if available), which will provide additional information. Exam should be 1 minute per question and please time accordingly.It is not required to have CompTIA A+ certification prior to obtaining CompTIA Network+ certification. It is recommended to have CompTIA A+ certification or the knowledge of the subject matter that is covered under A+ certification exam before taking Network+ certification exam. It is also recommended, but not required, that you have about 12 months of IT networking work experience.
Go to: Set I | Set III
CompTIA Network+ N10-007 - Set II
Congratulations - you have completed CompTIA Network+ N10-007 - Set II.
You scored %%SCORE%% out of %%TOTAL%%. With incorrect multiple attempts, your score is %%PERCENTAGE%%. Your performance has been rated as %%RATING%%
Question 1 |
A | Point-to-point |
B | Client-to-site |
C | Point-to-multipoint |
D | Site-to-site |
Question 2 |
A | Incident response |
B | AUP |
C | DLP |
D | Offboarding |
E | Remote access |
Question 3 |
A | Reviewing a vulnerability scan |
B | Reviewing application logs |
C | Reviewing SLA requirements |
D | Reviewing a baseline report |
Question 4 |
A | Disable FTP service on the server |
B | Disable the SMTP service on the server |
C | Disable DHCP service on the server |
D | Disable Telnet service on the server |
Question 5 |
A | dig |
B | arp |
C | nslookup |
D | ipconfig |
Question 6 |
A | Session hijacking |
B | Logic bomb |
C | Trojan horse |
D | Social engineering |
E | Insider threat |
Question 7 |
A | Attenuation |
B | EMI |
C | Open/short |
D | TX/RX reverse |
Question 8 |
A | Additional lease time for the laptop computers |
B | IP helper relay system for configuration hops |
C | DHCP reservation for the laptops MACs |
D | CNAME record in the users dynamic DNS accounts |
Question 9 |
A | SSH in tunnel mode |
B | RDP set to console connection |
C | SFTP |
D | EAP-PEAP |
Question 10 |
A | Change the WiFi password. |
B | Implement WEP authentication. |
C | Disable the SSID broadcast. |
D | Activate MAC address filtering. |
Question 11 |
A | AAAA |
B | CNAME |
C | SRV |
D | MX |
Question 12 |
A | Inventory report |
B | Network diagrams |
C | Labeling report |
D | Change management |
Question 13 |
A | SFTP |
B | TFTP |
C | Telnet |
D | FTPS |
E | SSL |
Question 14 |
A | ipconfig /flushdns |
B | ipconfig /renew |
C | ipconfig /all |
D | ipconfig /release |
Question 15 |
A | Transport |
B | Physical |
C | Network |
D | Application |
Question 16 |

Which of the following ones should the technician use to place the webserver and which of the following firewall rules should the technician configure?
A | Place the web server in the DMZ with an inbound rule from eth1 interface to eth0 to accept traffic over port 80 designated to the webserver |
B | Place the web server in the private zone with an inbound rule from eth2 interface to eth1 to accept traffic over port 80 designated to the webserver |
C | Place the web server in the DMZ with an inbound rule from eth0 interface to eth1 to accept traffic over port 80 designated to the webserver |
D | Place the web server in the public zone with an inbound rule from eth0 interface to accept traffic over port 80 designated to the webserver |
Question 17 |
A | Proximity reader |
B | Biometric device |
C | Identification card |
D | Video camera |
Question 18 |
A | 10Base2 |
B | 10GBaseT |
C | 10Base5 |
D | 1000BaseSX |
E | 1000BaseLX |
F | 1000BaseT |
Question 19 |
A | DHCP snooping |
B | Spanning tree |
C | BPDU guard |
D | Flood guard |
Question 20 |
A | The ports replied with a SYN/ACK response |
B | The ports are associated with deprecated services |
C | The ports belong to an active system and are denying requests |
D | The ports do not belong to a live system |
Question 21 |
A | SNMP |
B | SSL |
C | FTP |
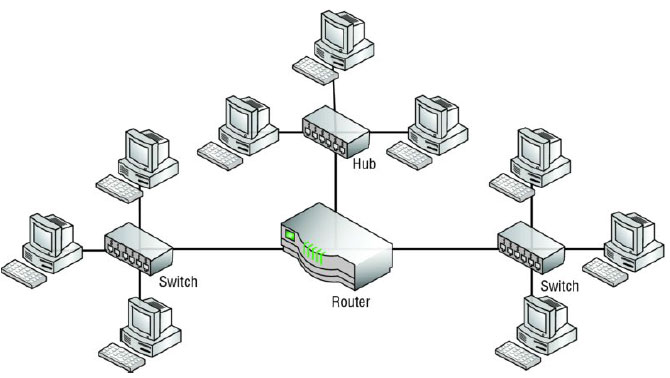
D | CHAP |
E | SSH |
Question 22 |
A | There are 12 collision domains, one for each switch connection. |
B | There are 3 collision domains, one for each switch-to-switch connection. |
C | There are 9 collision domains, one for each half-duplex connection. |
D | There is one collision domain for this network. |
Question 23 |
A | Document the findings and outcomes |
B | Escalate the ticket to a senior technician |
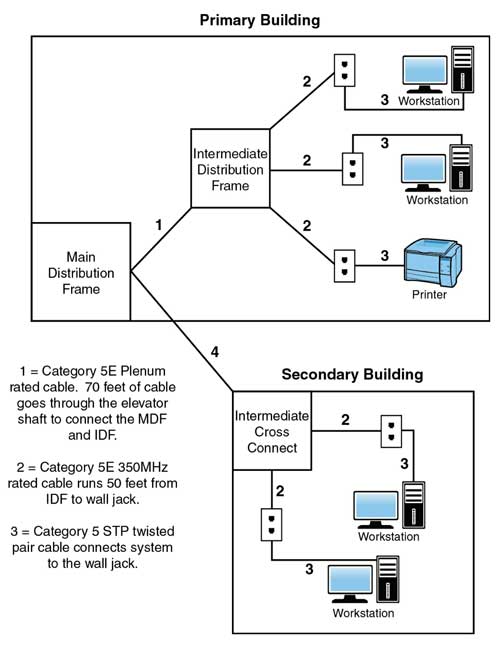
C | Implement the solution |
D | Do nothing |
E | Establish a theory of probable cause |
Question 24 |
A | Port 123 |
B | Port 69 |
C | Port 161 |
D | Port 25 |
Question 25 |
A | Review and modify the firewall rules |
B | Upgrade to the latest firmware |
C | Verify the default passwords have been changed |
D | Generate new SSH keys |
Question 26 |
A | IP |
B | Ethernet |
C | None of the answers are correct. |
D | TCP |
E | UDP |
Question 27 |
A | TTL |
B | MTU |
C | Duplex |
D | Speed |
Question 28 |
A | Mesh |
B | Ring |
C | Bus |
D | Star |
Question 29 |
A | Layer 1 – Physical |
B | Layer 6 - Presentation |
C | Layer 3 – Network |
D | Layer 4 – Transport |
E | Layer 7 – Application |
Question 30 |
A | TX/RX reverse |
B | VLAN mismatch |
C | Duplicate IP address |
D | Duplex/Speed mismatch |
Question 31 |
A | MPLS |
B | Broadband cable |
C | Frame relay |
D | ISDN |
E | PRI |
Question 32 |
A | SC |
B | SFTP |
C | DB-9 |
D | LC |
E | RJ45 |
F | GBIC |
Question 33 |
A | Duplicate IP addresses |
B | Loopback address |
C | APIPA address |
D | Duplicate MAC addresses |
Question 34 |
A | PPP |
B | Fibre Channel |
C | iSCSI |
D | RDMA |
Question 35 |
A | One of the wireless access points is on the wrong frequency |
B | The students are using more than one wireless device port seat |
C | Distance limitations are preventing the students from connecting |
D | The students are attempting to connect 802.11g devices |
Question 36 |
A | DNS |
B | DHCP |
C | SQL |
D | TCP/IP |
Question 37 |
A | DHCP |
B | ICMP |
C | DNS |
D | HTTP |
E | NetBIOS |
Question 38 |
A | IDF/MDF documentation |
B | Change management |
C | Performance baseline |
D | Physical diagram |
Question 39 |
A | Incremental |
B | Differential |
C | Snapshots |
D | Replica |
Question 40 |
A | Replace the NIC |
B | Modify the speed and duplex |
C | Plug in to another port |
D | Change the switch |
Question 41 |
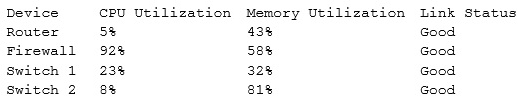
Which of the following devices is causing the issue?
A | Router |
B | Switch 1 |
C | Firewall |
D | Switch 2 |
Question 42 |
A | 172.16.0.0/22 |
B | 192.168.25.0/24 |
C | 10.5.4.0/22 |
D | 172.18.0.0/23 |
E | 10.233.2.0/23 |
Question 43 |
A | 10.8.0.0/20 |
B | 10.8.0.0/16 |
C | 10.8.0.0/19 |
D | 10.0.0.0/24 |
Question 44 |
A | Cat 5e |
B | Cat 6a |
C | Cat 7 |
D | Cat 6 |
Question 45 |
“The Security certificate presented by this website was not trusted by trusted certificate authority.”
Sanuja has cleared his cache and cookies, rebooted his machine, and attempted to browse to the website from a coworker’s desktop, but it still presented with this error. Which of the following is the MOST likely cause of this error?
A | The website is missing an HTTPS certificate. |
B | The SSL certificate has expired. |
C | TLS is not enabled in the browser. |
D | The web server is missing an intermediate certificate. |
Question 46 |
A | ACL misconfiguration |
B | Bad port |
C | Duplex/speed mismatch |
D | Crosstalk |
Question 47 |
A | MDI-X |
B | ASIC |
C | GBIC |
D | SFP |
E | SPF |
Question 48 |
A | permit tcp any any eq 110 |
B | permit udp any any eq 68 |
C | permit tcp any any eq 8080 |
D | permit udp any any eq 25 |
E | permit udp any any eq 53 |
F | permit tcp any any eq 20 |
Question 49 |
A | 802.11b |
B | 802.11n |
C | 802.11a |
D | 802.11ac |
Question 50 |
A | Cat 5 |
B | Cat 3 |
C | Cat 6 |
D | RG-6 |
E | SMF |
Question 51 |
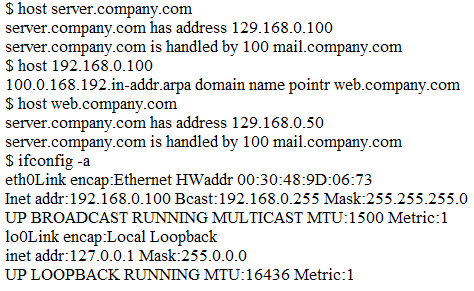
A | The server IP address is incorrectly configured |
B | There is no reverse DNS entry for this host |
C | The DNS lookup entry is incorrectly configured |
D | The reverse DNS entry is pointing to a different host |
Question 52 |
A | gdm |
B | systemd |
C | top |
D | root |
E | sanuja |
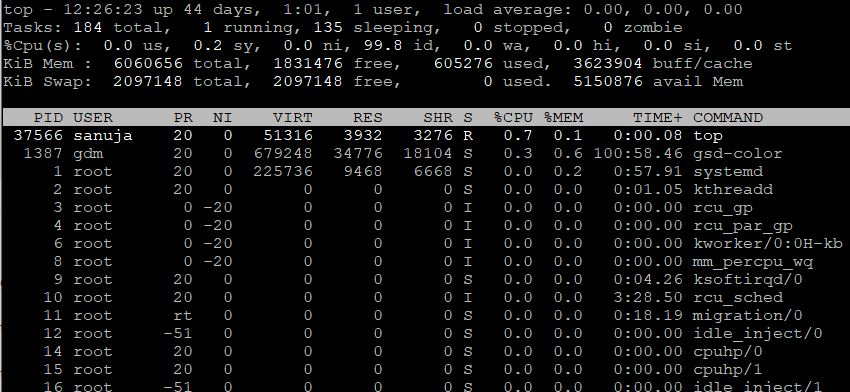
Question 53 |
A | 5 collision domains, 48 segments |
B | 48 networks, 5 segments |
C | 240 private networks |
D | 48 collision domains, 5 broadcast domains |
E | 240 usable IP addresses |
Question 54 |
A | Forward the DHCP logs to the security manager every day |
B | Label existing systems with current hostnames |
C | Enforce port security to require system authentication |
D | Implement a standardized UNC |
Question 55 |
A | Swipe badges |
B | Video cameras |
C | Motion sensors |
D | Sign-in sheets |
Question 56 |
A | Datagrams |
B | Packets |
C | Frames |
D | Segments |
Question 57 |
A | DDoS |
B | DDoS |
C | IDS firewall |
D | MITM |
E | DNS sinkhole |
Question 58 |
A | Rogue DHCP server |
B | Expired IP address |
C | Exhausted dynamic scope |
D | Misconfigured VLSM |
Question 59 |
A | WPA-PSK |
B | WEP-TKIP |
C | AES-CCMP |
D | EAP-TLS |
Question 60 |
A | Disabling unnecessary services from the server and management software |
B | Changing the management software's default credentials |
C | Changing the management software's default port |
D | Replacing the management software's self-signed certificate with a valid certificate |
Question 61 |
A | Use an HTTP server to share the file. |
B | Use a TFTP server and UDP protocol. |
C | Use a modem and dial-up connection. |
D | Use an FTP server and provide the file hash. |
Question 62 |
A | Multimeter |
B | Packet sniffer |
C | Spectrum analyzer |
D | OTDR |
Question 63 |
A | MOU |
B | AUP |
C | NDA |
D | BYOD |
Question 64 |
A | Cat 7 |
B | Plenum |
C | Single-mode |
D | PVC |
Question 65 |
A | Using a secure SSH connection over the WAN link to connect to a server. |
B | Accessing a DSL router via the console port. |
C | Telnet into the router over a secure VPN. |
D | Implementing a modem on the AUX port to access a network device. |
Question 66 |
A | Baseband |
B | Analog modem |
C | Broadband |
D | CSMA |
Question 67 |
A | Digital signatures |
B | SSL certificate |
C | 3DES encryption |
D | Digital signatures |
Question 68 |
A | TACACS+ |
B | Captive portal |
C | RADIUS |
D | Single sign-on |
Question 69 |
Image Credits: https://www.homedepot.com/p/ Ideal-Punchdown-Tool- with-110-and-66- Blades-35-485/ 203761571
A | Butt set |
B | Crimper |
C | Tone generator and locator |
D | Punchdown tool |
Question 70 |
A | STP cabling |
B | Fiber-optic cabling |
C | Coaxial cabling |
D | UTP cabling |
Question 71 |
A | 2 |
B | 0 |
C | 1 |
D | 12 |
E | 6 |
Question 72 |
A | IEEE 802.1q |
B | IEEE 802.3x |
C | IEEE 802.1X |
D | IEEE 802.11ac |
Question 73 |
A | Virtual switch |
B | vSAN |
C | Fiber Channel |
D | FCoE |
E | VPC |
Question 74 |
A | Clustering |
B | Load balancer |
C | Jumbo frames |
D | Round robin |
E | TCP offloading |
Question 75 |
A | Upgrade the firmware. |
B | Reset the two-factor token. |
C | Disable virtual ports. |
D | Disable unused ports. |
Question 76 |
A | Question users |
B | Document findings |
C | Duplicate the problem |
D | Test solutions |
E | Establish a theory of probable cause |
F | Implement preventive measures |
Question 77 |
A | eth_addr |
B | -a |
C | /all |
D | -i address |
Question 78 |
A | IPS |
B | Proxy server |
C | Load balancer |
D | VPN concentrator |
E | IDS |
Question 79 |
A | SNMP host |
B | SNMP agent |
C | OUI |
D | OID |
E | OTDR |
Question 80 |
A | TDR |
B | OTDR |
C | Spectrum analyzer |
D | Loopback adapter |
Question 81 |
A | Server IP address |
B | TACAS+ server time |
C | DNS SRV record |
D | Host-based firewall settings |
Question 82 |
A | Pool |
B | IP helper |
C | Lease time |
D | DHCP timer |
E | MAC reservation |
Question 83 |
A | VLAN routing |
B | Patch cable type |
C | Server-based firewall configuration issue |
D | DHCP scope availability |
Question 84 |
A | Evil twin |
B | DHCP exhaustion |
C | ARP poisoning |
D | Session hijacking |
E | Social engineering |
Question 85 |
A | International export controls |
B | Licensing restrictions |
C | Data loss prevention |
D | Remote access policies |
E | Incident response policy |
Question 86 |
A | Ring |
B | Star |
C | Mesh |
D | Ad hoc |
Question 87 |
A | The LAN and WLAN should be configured in the same zone with dynamic DENY ALL rules. |
B | The LAN and WLAN should be configured in separate zones with a firewall in between. |
C | The LAN and WLAN should be configured in the DMZ so traffic is denied automatically. |
D | The LAN and WLAN should be marked as trusted during work hours and untrusted during off hours. |
Question 88 |
A | Tone generator |
B | Punchdown tool |
C | Loopback adapter |
D | Multimeter |
Question 89 |
A | TFTP |
B | Telnet |
C | SCP |
D | FTP |
E | DHCP |
Question 90 |
A | Frequency mismatch |
B | Jitter |
C | Attenuation |
D | Latency |
Question 91 |
A | Port 110 |
B | Port 110 |
C | Port 443 |
D | Port 22 |
E | Port 80 |
Question 92 |
A | RADIUS server |
B | Content filter |
C | Wireless controller |
D | VoIP PBX |
Question 93 |
A | Require a pre-shared key for authentication to the wireless network |
B | Require PEAP for authentication to the wireless network |
C | Implement a Faraday cage within the building premises |
D | Use MAC filtering for authorization to the wireless network |
Question 94 |
A | Server room |
B | Intermediate distribution frame |
C | Equipment closet |
D | Demarcation point |
Question 95 |
A | WP2-PSK |
B | EAP-TLS |
C | Captive portal |
D | PEAP |
Question 96 |
A | SHA |
B | authpriv |
C | Authentication passphrase |
D | MD5 |
Question 97 |
A | DDoS attacks are launched from multiple hosts |
B | Spoofing attacks originate from a single host |
C | Spoofing attacks require physical presence |
D | DDoS attacks target multiple networks |
Question 98 |
A | Content filtering |
B | Intrusion detection |
C | Proxy service |
D | Dynamic DNS |
Question 99 |
A | MAC spoofing |
B | VLAN hopping |
C | Session hijacking |
D | Bluesnarfing |
E | Man-in-the-middle |
Question 100 |
A | DSCP |
B | SIP |
C | STP |
D | VLANs |
Question 101 |
A | MX |
B | PTR |
C | NS |
D | CNAME |
E | A |
Question 102 |
A | Data tier |
B | Demarc |
C | DMZ |
D | IDF |
Question 103 |
A | EAP-TLS |
B | WPA2 |
C | Captive portal |
D | SSL certificate |
E | MAC filtering |
Question 104 |
A | network devices |
B | packet flow |
C | traffic-routing protocols |
D | public/private networks |
Question 105 |
A | Install a repeater to boost the signal to its destination |
B | Upgrade the cable from Cat 5 to Cat 5e or Cat 6 |
C | Replace the UTP cable with plenum cable |
D | Set the AP to half-duplex to compensate for signal loss |
Question 106 |
A | Demarc |
B | DOCSIS modem |
C | DSL modem |
D | Wireless router |
E | Access point |
Question 107 |
Subnet 1: 192.168.1.0/26
Subnet 2: 192.168.1.65/26
Company B uses the following scheme:
Subnet 1: 192.168.1.50/28
A | NAT |
B | DMZ |
C | VLAN |
D | PAT |
Question 108 |
A | Move the fiber cable to a different port on the switch where both strands function |
B | Reverse the fiber strands of the cable and reconnect them to the server |
C | Use a TDR to test both strands of a new replacement cable prior to connecting it to the server |
D | Replace the server's single-mode fiber cable with multimode fiber |
Question 109 |
A | Routing loop |
B | Dynamic routes |
C | DHCP |
D | Route redistribution |
E | Routing table |
Question 110 |
A | Ports 56 and 57 |
B | Port 123 and 8080 |
C | Ports 80 and 443 |
D | Ports 20 and 21 |
E | Ports 67 and 68 |
Question 111 |
A | Monitoring of network-attached devices |
B | Retrieving contents of an Internet page from a web server |
C | Synchronization of clocks over a computer network |
D | Allocation of IP addresses |
Question 112 |
A | Pre-shared key |
B | MAC filtering |
C | Open wireless |
D | Geofencing |
Question 113 |
A | The cable is rollover cable |
B | The cable has bent pins |
C | The cable is damaged |
D | The cable is a crossover cable |
E | The cable is a Cat 5 cable |
Question 114 |
A | Channel 7 |
B | Channel 10 |
C | Channel 6 |
D | Channel 9 |
Question 115 |
A | 14 |
B | 12 |
C | 13 |
D | 15 |
E | 3 |
Question 116 |
A | NTP |
B | RTP |
C | H.323 |
D | ICMP |
E | SMB |
F | SIP |
Question 117 |
A | There are three collision domains and three broadcast
domains. |
B | There are seven collision domains and three broadcast
domains. |
C | There are nine collision domains and three broadcast
domains. |
D | There are three collision domains and one broadcast domain. |
E | There is one collision domain and one broadcast domain. |
Question 118 |
A | AUP |
B | SLA |
C | NDA |
D | DLP |
Question 119 |
A | Port mirroring |
B | Trunking |
C | Port aggregation |
D | Spanning tree |
Question 120 |
A | Data link |
B | Session |
C | Presentation |
D | Transport |
Question 121 |
A | HTTP over WPA2-TKIP WiFi |
B | SSH over IPsec client-to-site VPN |
C | Telnet over PSTN |
D | RDP over SSLv2 HTTPS terminal services gateway |
Question 122 |
A | Bridge |
B | Load balancer |
C | Layer 2 switch |
D | Layer 3 switch |
Question 123 |
A | Partial mesh |
B | Bus |
C | Ad hoc |
D | Ring |
Question 124 |
A | 192.168.12.97 to 255.255.255.192 |
B | 192.168.12.97 to 255.255.255.248 |
C | 192.168.12.97 to 255.255.255.240 |
D | 192.168.12.97 to 255.255.255.224 |
Question 125 |
A | Port aggregation |
B | iSCSI |
C | QoS tags |
D | Jumbo frames |
Question 126 |
A | WAP power level controls |
B | Protocol analyzer |
C | Network mapper |
D | Logical network diagram |
Question 127 |
A | Cable 3 should be an STP cable. |
B | Cable 1 does not need to be plenum rated. |
C | Cable 2 should be an STP cable. |
D | None, the network looks good. |
Question 128 |
A | Bridge |
B | Hub |
C | Router |
D | Switch |
Question 129 |
A | SNR |
B | RFI |
C | BRI |
D | SVC |
Question 130 |
A | Network configuration |
B | Rack diagram |
C | Change management |
D | Network diagram |
Question 131 |
A | Enforcing a stronger password policy and using a hand geometry scan |
B | Using a smart card and RSA token |
C | Adding a fingerprint reader and retina scanner |
D | Adding a fingerprint reader to each workstation and providing a RSA authentication token |
Question 132 |
A | Packet filtering utility |
B | MS Windows command-line tool |
C | Linux command-line tool |
D | Packet tracing utility |
E | Packet capturing utility |
Question 133 |
A | Load balancing |
B | Clustering |
C | Redundant circuits |
D | NIC teaming |
E | Multiple NAT |
Question 134 |
A | Adding a router reduces the amount of broadcast traffic on each of the two LANs. |
B | Adding a router diverts traffic to an alternate path through the network. |
C | Adding a router reduces the amount of unicast traffic on each of the two LANs. |
D | Adding a router prevents computers on one LAN from communicating with computers on another LAN. |
Question 135 |
A | The R&D department should receive a /27 network. |
B | The R&D department should have a last usable IP address of 172.16.49.190. |
C | The legal department should have a first usable IP address of 172.16.49.190. |
D | The legal department should have usable IPs ranging from 172.16.49.129 to 172.16.49.190. |
E | The marketing department should receive a /25 network. |
F | The R&D department should have 172.16.49.207 as a broadcast address. |
G | The finance department should have 172.16.49.127 as a broadcast address. |
H | The marketing department should have usable IPs ranging from 172.16.49.129 to 172.16.49.190. |
Question 136 |
A | It provides multiple collision domains on one switchport |
B | It provides multiple broadcast domains within a single collision domain |
C | It provides a faster port to all servers |
D | It segments broadcast domains in the network infrastructure |
Question 137 |
A | One router connected to one 12-port switch configured for the manager's computers, phones, and printer, and one 12-port switch configured for the other computers, VoIP phones, and printer |
B | One router connected to one 24-port switch configured with three VLANS: one for the manager's computers and printer, one for the other computers and printer, and one for the VoIP phones |
C | One router connected to one 24-port switch configured with two VLANS: one for the manager's computers, VoIP phones, and printer, and one for the other computers, VoIP phones, and printer |
D | Two routers with each router connected to a 12-port switch, with a firewall connected to the switch connected to the manager's desktop computers, VoIP phones, and printer |
Question 138 |
A | 900MHz |
B | 5GHz |
C | 56MHz |
D | 2.4 GHz |
Question 139 |
User A
IP address: 192.168.1.121
Subnet mask: 255.255.255.0
Default gateway: 192.168.1.1
User B
IP address: 192.168.1.125
Subnet mask: 255.255.248.0
Default gateway: 192.168.1.1
A | User B's IP address is not a loopback address |
B | The subnet values should be the same |
C | There is no problem identifiable by the values given. |
D | The default gateway should have different values |
Question 140 |
IP: 192.168.1.100
Mask: 255.255.255.0
Router: 192.168.1.1
A | Wrong SSID |
B | Security type mismatch |
C | Interference |
D | Channel overlap |
Question 141 |
A | MITM |
B | DDoS |
C | Phishing |
D | OCSP stapling |
E | Evil twin |
Question 142 |
A | Key escrow |
B | CRL |
C | OCSP |
D | CSR |
Question 143 |
A | Because SCP is not a secure service |
B | Because a secure firewall will protect the device |
C | Because FTP is not a secure service |
D | Because secure protocols would reject malicious packets |
Question 144 |
A | Configure the DNS address in the DHCP scope to a 10.10.5.0/24 address. |
B | Change the IP scope on the DHCP server to a public IP address range. |
C | Verify the host has physical connectivity and is on the correct VLAN. |
D | Perform a traceroute command to identify the router that is not functioning. |
Question 145 |
A | Implement root guard on all switches. |
B | Create a honeypot to attract attackers. |
C | Create a VLAN for all unused switchports. |
D | Implement a DMZ for all external services. |
Question 146 |
A | penetration testing. |
B | risk assessment. |
C | device hardening. |
D | role separation. |
Question 147 |
A | Loopback adapter |
B | Multimeter |
C | Tone generator |
D | Cable tester |
Question 148 |
Gigabit Ethernet 1 Interface: 10.10.0.1/24 Serial 0 Interface: 10.10.0.253/30
A | The router was configured with an incorrect loopback address |
B | The router was configured with an incorrect default gateway |
C | The router was configured with an incorrect IP address |
D | The router was configured with an incorrect subnet mask |
Question 149 |
A | Layer 2 switch |
B | Bridge |
C | Signal repeater |
D | Domain server |
E | Layer 3 switch |
Question 150 |
A | Gather information |
B | Document the findings |
C | Establish a plan of action |
D | Determine the symptoms |
Question 151 |
A | Room number |
B | Rack location |
C | Media type |
D | Hostname |
Question 152 |
A | DHCP |
B | LADP |
C | DNS |
D | HTTP |
E | ICMP |
Question 153 |
A | SMB |
B | RDP |
C | SNMP |
D | NTP |
E | SSL |
Question 154 |
A | Phishing |
B | Spam |
C | Ransomware |
D | Man-in-the-middle |
Question 155 |
A | Bridge |
B | Next-generation firewall |
C | Switch |
D | Multilayer switch |
Question 156 |
-WLAN architecture supporting speeds in excess of 150 Mbps
-Client less remote network access
-Port-based network access control
A | 802.11g, MS-CHAP, 802.16 |
B | 802.11ac, MPLS, 802.3 |
C | 802.11a, IPSec VPN, 802.1x |
D | 802.11b, PPTP,802.1x |
E | 802.11n, SSL-VPN, 802.1x |
Question 157 |
A | The Faraday cage is creating attenuation of the cellular network. |
B | The Faraday cage prevents access by redirecting signals. |
C | The Faraday cage is creating latency on the cellular network. |
D | The Faraday cage is creating interference within the bookstore. |
Question 158 |
A | NDA |
B | SLA |
C | AUP |
D | MOU |
Question 159 |
A | Spectrum analyzer |
B | nslookup |
C | netstat |
D | Packet sniffer |
Question 160 |
A | Generate new keys |
B | Change default credentials |
C | Update firmware |
D | Perform file hashing |
Question 161 |
A | pathping |
B | Nmap |
C | netstat |
D | traceroute |
Question 162 |
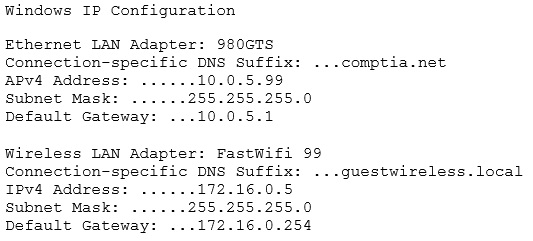
Which of the following would MOST likely allow the network drives to be accessed?
A | Update the WLAN adapter driver |
B | Disable the LAN adapter |
C | Disable the WLAN adapter |
D | Check the wireless DHCP configuration |
Question 163 |
A | Implement stacking on the switches in the rack |
B | Add a redundant power supply to the switch |
C | Install a power converter for the switch |
D | Add a second UPS into the rack |
Question 164 |
A | Disable the SSID broadcast on each access point. |
B | Enable AP isolation on each access point. |
C | Enable MAC address filtering on each access point. |
D | Reduce the TX power on each access point. |
Question 165 |
A | Create two SSIDs, one to support CCMP-AES encryption and one with TKIP-RC4 encryption. |
B | Configure modern devices under the 5GHz band while dedicating the 2.4GHz band to legacy devices. |
C | Connect the legacy devices with a PSK while the modern devices should use the more secure EAP. |
D | Configure the APs to use LEAP authentication to support WPA rather than WPA2 for full compatibility. |
Question 166 |
A | Telnet |
B | TFTP |
C | Samba |
D | LDAP |
Question 167 |
A | SAN |
B | SaaS |
C | IaaS |
D | NAS |
Question 168 |
A | SSL VPN |
B | IPSec |
C | PPTP |
D | PTP |
Question 169 |
A | Backs up files with the archive bit set but does not clear the bit. |
B | Backs up files with a date earlier than today’s date with a clear archive bit. |
C | Backs up files with the creation or modified date as the current date. |
D | Backs up all files and sets the archive bit. |
Question 170 |
A | FCoE |
B | iSCSI |
C | InfiniBand |
D | OC3 |
Question 171 |
A | Router |
B | Proxy server |
C | Load balancer |
D | Switch |
Question 172 |
A | 802.1q |
B | 802.3af |
C | 802.3at |
D | 802.1X |
E | 802.11ac |
Question 173 |
A | pathping |
B | nslookup |
C | nbtstat |
D | netstat |
Question 174 |
A | Create a network baseline |
B | Create an inventory database |
C | Create a port location diagram |
D | Create a rack diagram |
Question 175 |
A | Motion detectors |
B | Video surveillance |
C | Door locks |
D | Biometric scanners |
Question 176 |
A | Attenuation |
B | Incorrect pin-out |
C | Switch configuration |
D | Damaged cable |
Question 177 |
A | dig |
B | nmap |
C | tcpdump |
D | arp |
Question 178 |
A | Add a second cable connecting the switches for redundancy and disabling STP on both switches. |
B | Replace the new switch with a hub to ensure Layer1 connectivity on the new network segment. |
C | Move the straight-through Ethernet cable connecting the switches to the first port on both switches. |
D | Connect the switches with a cable that has a TIA/EIA 586A wired connector end and a TIA/EIA 586B wired end. |
Question 179 |
A | Tone generator |
B | Protocol analyzer |
C | Multimeter |
D | OTDR |
E | Spectrum analyzer |
Question 180 |
A | Broadcast storms entering from a root port are blocked. |
B | The STP root bridge cannot be changed. |
C | Loop protection is enabled on the root port of a switch. |
D | BPDUs entering the root bridge are ignored. |
Question 181 |
A | 2046 |
B | 512 |
C | 1022 |
D | 2048 |
E | 510 |
F | 1024 |
Question 182 |
A | IP helper |
B | Ping table |
C | DHCP lease time |
D | TTL |
E | DNS record type |
Question 183 |
A | VNC application |
B | Kerberos |
C | Geotagging application |
D | Credentials |
Question 184 |
route add 0.0.0.0 mask 0.0.0.0 192.169.1.222 metric 1
A | The technician is adding a static IP address. |
B | The technician is setting the default gateway. |
C | The technician is clearing the subnet mas setting. |
D | The technician is clearing the route table. |
Question 185 |
A | Jitter |
B | Open/short on the cable |
C | Transceiver mismatch |
D | Crosstalk |
Question 186 |
A | There is additional data being transferred over the wireless network |
B | An IoT device is causing a DoS attack on the wireless network |
C | There is interference with the smart reader |
D | The utility company throttles power during peak hours |
Question 187 |
A | 2001::d58::95:7565:1 |
B | 2001:0:d58::95:7565:1 |
C | 2001:0:d58:0:0:95:7565:1 |
D | 2001:0:0d58::95:7565:1 |
Question 188 |
A | Wardriving |
B | DDoS attack |
C | MITM attack |
D | Session hijacking |
E | Spoofing attack |
Question 189 |
A | The use of autonomous APs with a load balancer |
B | The use of autonomous APs with a wireless controller |
C | The use of lightweight APs with a wireless controller |
D | The use of lightweight APs with a load balancer |
Question 190 |
A | Router |
B | Media converter |
C | Wireless access point |
D | Network switch |
E | Firewall |
Question 191 |
A | It cannot be used on modern Windows computers. |
B | Provides username & password authentication. |
C | Transmits data in an unencrypted form. |
D | Encrypts network connection. |
E | Enables remote login and command execution. |
F | It does not provide authentication. |
Question 192 |
A | The technician should reset all the phones and deprovision information from the provider |
B | The technician should run ping tests on the Internet line to monitor for packet loss and latency |
C | The technician should check the internal diagnostics on all the phones to look for a common thread |
D | The technician should use a packet tracer to see if the traffic is getting out of the network |
Question 193 |
A | Data loss prevention |
B | Acceptable use |
C | Asset disposal |
D | Incident response |
Question 194 |
A | Duplex GBIC |
B | 1000BaseLX SFP |
C | Duplex SFP+ |
D | Bidirectional SFP |
Question 195 |
A | Reverse the wires leading to pins 2 and 3 |
B | Reverse the wires leading to pins 1 and 3 |
C | Reverse the wires leading to pins 2 and 4 |
D | Reverse the wires leading to pins 1 and 2 |
Question 196 |
A | Implement a chain of custody |
B | Secure the area |
C | Document the scene |
D | Take pictures upon arrival |
Question 197 |
A | LDAP |
B | SFTP |
C | TLS |
D | SSH |
Question 198 |
A | Certificate |
B | Kerberos |
C | NAC |
D | SSO |
E | MFA |
F | RADIUS |
Question 199 |
A | SOHO router |
B | Layer 2 switch |
C | Cable modem |
D | DNS server |
Question 200 |
A | Bent pins |
B | Damaged cables |
C | VLAN mismatch |
D | Crosstalk |
E | TX/RX reverse |
F | Duplex mismatch |
← |
List |
→ |
| 1 | 2 | 3 | 4 | 5 |
| 6 | 7 | 8 | 9 | 10 |
| 11 | 12 | 13 | 14 | 15 |
| 16 | 17 | 18 | 19 | 20 |
| 21 | 22 | 23 | 24 | 25 |
| 26 | 27 | 28 | 29 | 30 |
| 31 | 32 | 33 | 34 | 35 |
| 36 | 37 | 38 | 39 | 40 |
| 41 | 42 | 43 | 44 | 45 |
| 46 | 47 | 48 | 49 | 50 |
| 51 | 52 | 53 | 54 | 55 |
| 56 | 57 | 58 | 59 | 60 |
| 61 | 62 | 63 | 64 | 65 |
| 66 | 67 | 68 | 69 | 70 |
| 71 | 72 | 73 | 74 | 75 |
| 76 | 77 | 78 | 79 | 80 |
| 81 | 82 | 83 | 84 | 85 |
| 86 | 87 | 88 | 89 | 90 |
| 91 | 92 | 93 | 94 | 95 |
| 96 | 97 | 98 | 99 | 100 |
| 101 | 102 | 103 | 104 | 105 |
| 106 | 107 | 108 | 109 | 110 |
| 111 | 112 | 113 | 114 | 115 |
| 116 | 117 | 118 | 119 | 120 |
| 121 | 122 | 123 | 124 | 125 |
| 126 | 127 | 128 | 129 | 130 |
| 131 | 132 | 133 | 134 | 135 |
| 136 | 137 | 138 | 139 | 140 |
| 141 | 142 | 143 | 144 | 145 |
| 146 | 147 | 148 | 149 | 150 |
| 151 | 152 | 153 | 154 | 155 |
| 156 | 157 | 158 | 159 | 160 |
| 161 | 162 | 163 | 164 | 165 |
| 166 | 167 | 168 | 169 | 170 |
| 171 | 172 | 173 | 174 | 175 |
| 176 | 177 | 178 | 179 | 180 |
| 181 | 182 | 183 | 184 | 185 |
| 186 | 187 | 188 | 189 | 190 |
| 191 | 192 | 193 | 194 | 195 |
| 196 | 197 | 198 | 199 | 200 |
| End |
Based on general knowledge and CompTIA guidelines published in 2020.
FAQ | Report an Error
Study outline at: CompTIA Exams Guide
Disclaimer: While every reasonable effort is made to ensure that the information provided is accurate, no guarantees for the currency or accuracy of information are made. It takes several proof readings and rewrites to bring the quiz to an exceptional level. If you find an error, please contact me as soon as possible. Please indicate the question ID-Number or description because server may randomize the questions and answers.