← Exams and Quizzes | Professional Exams →
Notice
If you get a question wrong, you can still click on the other answers. This will open up hints and explanations (if available), which will provide additional information. Exam should be 1 minute per question and please time accordingly.It is not required to have CompTIA A+ certification prior to obtaining CompTIA Network+ certification. It is recommended to have CompTIA A+ certification or the knowledge of the subject matter that is covered under A+ certification exam before taking Network+ certification exam. It is also recommended, but not required, that you have about 12 months of IT networking work experience.
Go to: Set II | Set III
CompTIA Network+ N10-007 - Set I
Congratulations - you have completed CompTIA Network+ N10-007 - Set I.
You scored %%SCORE%% out of %%TOTAL%%. With incorrect multiple attempts, your score is %%PERCENTAGE%%. Your performance has been rated as %%RATING%%
Question 1 |
A | Session |
B | Data Link |
C | Physical |
D | Transport |
E | Network |
F | Application |
G | Presentation |
Question 2 |
A | RJ45 |
B | MTRJ |
C | BNC |
D | 8P8C |
E | F-type |
Question 3 |
A | Feature change |
B | Operating system update |
C | Driver update |
D | Vulnerability patch |
E | BOIS firmware patch |
Question 4 |
A | netstat |
B | ping |
C | pathping |
D | route |
Question 5 |
A | Setup |
B | System |
C | Security |
D | Application |
Question 6 |
A | Create a secondary NAT and connect the kiosks on it hence limit kiosks' ability to access the main network. |
B | Install honeypots on the network to detect and analyze potential kiosk attacks before they occur. |
C | Create a new network segment with ACLs, limiting kiosks’ traffic with the internal network. |
D | Install an IDS to monitor all traffic to and from the kiosks. |
E | Enable switchport security on the ports to which the kiosks are connected to prevent network-level attacks. |
Question 7 |
A | Name resolution |
B | IP address resolution |
C | Network switching |
D | Password protection |
Question 8 |
A | Split pairs |
B | Short circuits |
C | Transposed wires |
D | Open circuits |
Question 9 |
A | netstat |
B | nmap |
C | dig |
D | tcpdump |
Question 10 |
Image Credit: https://www.tequipment.net/ FlukeNetworks52801009.html
A | By touching the end of the tool to a copper cable, you can detect and measure the electrical current flowing through it. |
B | By connecting the clips to pins in a punchdown block, you can access telephone circuits in order to test them or place telephone calls. |
C | When you place the tool at one end of a wire, it generates a tone that can be detected at the other end. |
D | To attach a bulk cable end to an RJ45 connector, you use the tool to squeeze the connector closed, forcing the wire ends to contact the connector’s pins. |
Question 11 |
A | Wardriving |
B | Evil twin |
C | Logic bomb |
D | Social engineering |
Question 12 |
A | DMZ |
B | RIP |
C | QoS |
D | DDoS |
E | NAT |
Question 13 |
A | Tracert |
B | Netstat |
C | Ping |
D | Nslookup |
E | Route |
Question 14 |
A | Bandwidth |
B | Ping time |
C | Hop count |
D | Speed |
E | Distance |
Question 15 |
A | Microwave |
B | Fiber optic |
C | Electrical |
D | Infrared |
Question 16 |
A | Source route |
B | Store and forward |
C | Multiport |
D | Transparent |
Question 17 |
A | http://sanuja.com:123456 |
B | https://sanuja.com/123456 |
C | None of the answers are correct because you cannot assign random port numbers. |
D | https://sanuja.com:123456 |
E | http://sanuja.com/123456 |
Question 18 |
A | FIN |
B | SYN |
C | URG |
D | END |
E | PSH |
Question 19 |
A | Bus |
B | Ring or circular |
C | Point-to-point |
D | Star |
E | Mesh |
Question 20 |
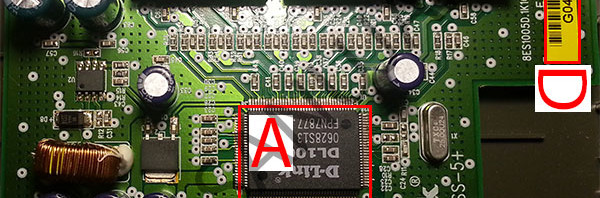
A | 192.168.1.1 |
B | 255 255 255.0 |
C | 192.168.0.55 |
D | 255 255 255.0 |
E | 192.168.1.0 |
Question 21 |
A | Verify the firmware file hash |
B | Apply patches and updates |
C | Change the default credentials |
D | Disable unused switchports |
Question 22 |
A | CARP |
B | Voice over IP |
C | Quality of service |
D | Round-robin DNS |
Question 23 |
A | ADSL |
B | Bridge mode |
C | DOCSIS |
D | Jumbo frame |
E | Double NAT |
Question 24 |
A | Public |
B | Private |
C | Preshared |
D | Privileged |
E | Secured |
Question 25 |
A | NAC |
B | ACL |
C | Sticky MAC |
D | NAT |
E | 802.1x |
Question 26 |
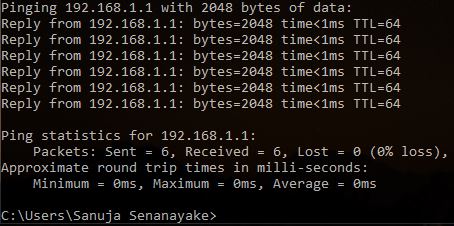
A | ping 192.168.1.1 -l 2048 -t 6 |
B | ping 192.168.1.1 -l 2048 -n 6 |
C | ping 192.168.1.1 -l 2048 -t |
D | ping 192.168.1.1 -n 2048 |
E | ping 192.168.1.1 -t |
Number of messages: -n parameter = 6
Question 27 |
A | POP |
B | SMTP |
C | IMAP |
D | LDAP |
Question 28 |
A | Tamper detection |
B | Geofencing |
C | Biometric |
D | Social engineering |
E | Asset tracking |
Question 29 |
A | 0 |
B | 4 |
C | 2 |
D | 7 |
E | 6 |
Question 30 |
A | Port security |
B | MAC filtering |
C | Captive portal |
D | NAC |
E | WAP |
Question 31 |
A | arp -c * |
B | arp -d * |
C | arp -s |
D | arp -a |
Question 32 |
A | TXT |
B | NS |
C | A |
D | AAAA |
E | MX |
Question 33 |
A | RC4 |
B | TKIP |
C | Kerberos |
D | 802.1X |
E | AES |
Question 34 |
A | WEP |
B | WPA |
C | PEAP |
D | WPA2 |
Question 35 |
A | VoIP gateway |
B | VPN concentrator |
C | UTM appliance |
D | Proxy server |
Question 36 |
A | A router with default credentials |
B | A privilege escalation script |
C | An open mail relay server |
D | An SNMPv1 private community |
Question 37 |
A | Authorization |
B | Authentication |
C | Accounting |
D | Auditing |
Question 38 |
A | Source route |
B | Destination switch |
C | Store-and-forward |
D | Cut-through |
Question 39 |
A | Allow the firewall to accept inbound traffic to ports 25, 67,179, and 3389 |
B | Allow the firewall to accept inbound traffic to ports 80,110,143, and 443 |
C | Set the firewall to operate in transparent mode |
D | Allow the firewall to accept inbound traffic to ports 21, 53, 69, and 123 |
Question 40 |
A | Enterprise firewall |
B | IDS |
C | Proxy server |
D | Load balancer |
E | Wireless controller |
Question 41 |
A | SFP |
B | BiDi |
C | GBIC |
D | QSFP |
Question 42 |
A | LACP |
B | BGP |
C | SIP |
D | LLDP |
Question 43 |
A | Port security |
B | Data security |
C | Asset tracking |
D | Physical security |
Question 44 |
A | Fibre Channel |
B | InfiniBand |
C | iSCSI |
D | CIFS |
Question 45 |
A | 143 , 993 |
B | 5060 , 3389 |
C | 5060 , 5061 |
D | 161 , 162 |
E | 80 , 443 |
Question 46 |
A | Authorization |
B | Accounting |
C | TGS |
D | Auditing |
E | Authentication |
Question 47 |
A | PAT |
B | VIP |
C | NAT |
D | SIP |
Question 48 |
A | RDP |
B | IDF |
C | MTBF |
D | MDF |
E | PBX |
Question 49 |
A | Single sign-on (SSO) |
B | Hand geometry |
C | Tamper detection |
D | Biometrics |
E | Pattern recognition |
Question 50 |
A | Update the firmware and drivers on spare network equipment regularly. |
B | Keep purchasing new spare equipment. |
C | Store all spare equipment in a sepearete office building for extra protection. |
D | Instead of replacing current units during failures, use parts from the spare units to fix the current unit. |
E | Do nothing and keep the spare nearby for an emergency. |
Question 51 |
A | 19 inches |
B | 12 inches |
C | 24 inches |
D | 16 inches |
Question 52 |
A | Utilize UDP to eliminate packet overhead |
B | Encapsulate the storage traffic in a GRE tunnel |
C | Enable jumbo frames on the NAS and server |
D | Turn off MDIX settings on the NAS and server switchports |
Question 53 |
A | A switch |
B | A gateway |
C | A router |
D | A hub |
Question 54 |
A | CNAME |
B | MD |
C | PTR |
D | A |
E | MX |
Question 55 |
A | Fibre Channel |
B | NAS |
C | InfinitiBand |
D | iSCSI |
Question 56 |
A | DDoS |
B | Session hijacking |
C | Ransomware |
D | Phishing |
E | Spoofing |
Question 57 |
A | DHCP exclusion |
B | DHCP reservation |
C | DHCP relay |
D | DHCP option |
E | DHCP restriction |
Question 58 |
A | Hire a third-party contractor to go on-site |
B | Travel to the branch office |
C | Walk a user through troubleshooting the connection |
D | Use a modem to console into the router |
Question 59 |
A | A virtual IP pointing to the active DB |
B | A static IP pointing to the passive DB |
C | A private IP pointing to the web front end |
D | A private IP pointing to the web proxy |
Question 60 |
A | MS-CHAPv2 |
B | WEP |
C | CHAP |
D | PAP |
E | EAP |
Question 61 |
A | 1999 |
B | 995 |
C | 50134 |
D | 23 |
E | 80 |
F | 1024 |
Question 62 |
A | Session |
B | Presentation |
C | Network |
D | Transport |
E | Physical |
F | Data link |
G | Application |
Question 63 |
A | LDAP |
B | RADIUS |
C | NAC |
D | TKIP-RC4 |
Question 64 |
A | MDF |
B | IDF |
C | TDM |
D | VRF |
Question 65 |
A | Network wiring is run perpendicular to electrical conduit |
B | Temperature changes are causing attenuation in copper cabling |
C | EMI from the lights is interfering with the network cables |
D | Light sensors are interfering with the network |
Question 66 |
A | tcpdump |
B | dig |
C | iptables |
D | nmap |
Question 67 |
A | SSL |
B | HTTP |
C | HTML |
D | FTP |
E | SMTP |
Question 68 |
A | Evil twin |
B | VLAN mismatch |
C | Honey pot |
D | Packet intrusion |
E | Rogue DHCP server |
Question 69 |
A | RADIUS server |
B | Wireless access point |
C | Smartcards |
D | Domain controller |
E | Biometric systems |
Question 70 |
A | Process management |
B | Project management |
C | Standard operating procedure |
D | Change management |
Question 71 |
A | 802.1X |
B | Radius |
C | TKIP |
D | Kerberos |
E | LDAP |
Question 72 |
A | VLAN restrictions |
B | VPN concentrator |
C | Content filter |
D | IPS |
E | Web application firewall |
Question 73 |
A | IMAP |
B | ICMP |
C | IP |
D | IGMP |
Question 74 |
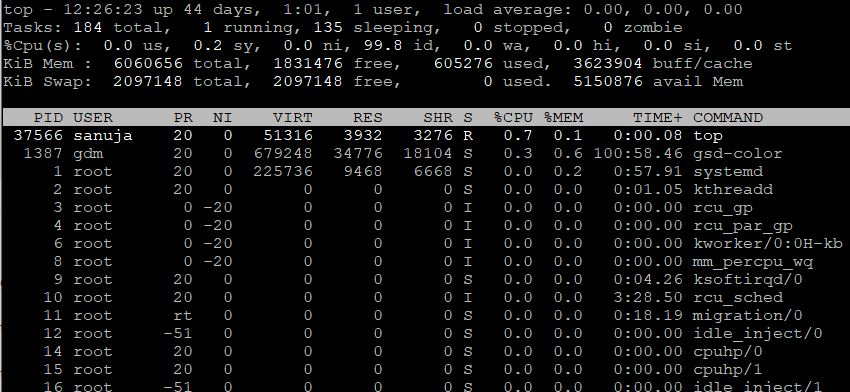
A | monitor |
B | top |
C | cpustat |
D | netstat |
E | ping |
Question 75 |
A | Encryption |
B | Certification |
C | Enrollment |
D | Authorization |
E | Authentication |
Question 76 |
A | Clustering |
B | UPS |
C | SNMP |
D | RAID 1 |
Question 77 |
A | Verify file version |
B | Verify file date |
C | Verify file size |
D | Verify file type |
E | Verify file hash |
Question 78 |
A | Perform frequent IT audits. |
B | Install and maintain advanced enterprise firewall applications. |
C | Configure advance intrusion detection and firewall rules on the main datacenter. |
D | Physical inspection of each site/workstation. |
E | Perform frequent security and vulnerability updates. |
Question 79 |
A | Performance Monitor |
B | Event Viewer |
C | Syslog |
D | ntop |
E | Network Monitor |
Question 80 |
A | PRI |
B | E1/E3 |
C | BRI |
D | DSL |
Question 81 |
A | Ethernet-over-power adapter |
B | Powerline extender |
C | Power distribution unit |
D | Power-over-Ethernet switch |
E | Ethernet power controller |
Question 82 |
A | -a |
B | -i |
C | -n |
D | -t |
Question 83 |
A | Social engineering |
B | Evil twin |
C | Logic bomb |
D | Wardriving |
Question 84 |
A | NAS |
B | FCoE |
C | iSCSI |
D | FTP |
E | SAN |
Question 85 |
A | Application |
B | Network |
C | Session |
D | Data link |
E | Transport |
F | Physical |
G | Presentation |
Question 86 |
A | LC to SC |
B | LC to ST |
C | SC to ST |
D | ST to ST |
E | SC to SC |
Question 87 |
A | 1 through 1024 |
B | 49152 through 65535 |
C | 1024 to 49151 |
D | 1023 through 65534 |
Question 88 |
A | Data Link |
B | Transport |
C | Application |
D | Network |
E | Session |
Question 89 |
A | Hex |
B | Binary |
C | CIDR |
D | Octal |
Question 90 |
A | Administration |
B | Authorization |
C | Accounting |
D | Authentication |
Question 91 |
A | Transport |
B | Network |
C | Presentation |
D | Physical |
E | Application |
F | Data link |
G | Session |
Question 92 |
A | Cross talk |
B | Overcapacity |
C | Wrong passphrase |
D | Channel overlap |
Question 93 |
A | Failover |
B | Snapshots |
C | Backups |
D | Cold sites |
Question 94 |
A | Class D |
B | Class B |
C | Class A |
D | None of the classes |
E | Class C |
Question 95 |
A | It is impossible to have a collision domain in a wired (LAN) network infrastructure. |
B | It is impossible to have a collision domain in a wireless network infrastructure. |
C | Collision domains occur in layer 1 while broadcast domains occur in layer 2. |
D | Broadcast domains occur in layer 1 while collision domains occur in layer 2. |
E | Both broadcast and collision domains occur at layer 2. |
Question 96 |
A | 15 |
B | 8 |
C | 17 |
D | 16 |
Question 97 |
A | Wiring schematic |
B | Physical network diagram |
C | Logical network diagram |
D | MSConfig file |
E | Asset management files |
Question 98 |
A | Directory traversal |
B | Wardriving |
C | SQL injection |
D | XSS |
E | Packet sniffing |
Question 99 |
A | social engineering |
B | friendly DoS |
C | penetration testing |
D | vulnerability scanning |
E | session hijacking |
Question 100 |
A | DNS server issue |
B | DHCP server issue |
C | VLAN mismatch |
D | Spanning tree blocked ports |
E | Duplex/speed mismatch |
Question 101 |
A | Damaged or malfunctioning LAN port |
B | Double NAT issue |
C | Damaged or malfunctioning fiber port |
D | VLAN mismatch |
E | Corrupted config files or operating system |
Question 102 |
A | Layer 3 repeater |
B | Multiport bridge |
C | Layer 2 router |
D | Ethernet hub |
Question 103 |
A | Smart jack |
B | SONET |
C | Media converter |
D | AAA server |
E | SIP trunk |
Question 104 |
A | Wireless endpoint |
B | Demarcation point |
C | Network firewall |
D | Wireless controller |
E | Demarcation point |
Question 105 |
A | PPTP |
B | FTPS |
C | L2TP |
D | IPsec |
Question 106 |
A | netstat |
B | ifconfig |
C | traceroute |
D | dig |
E | route |
Question 107 |
A | The password needs to be re-entered |
B | There is a frequency mismatch |
C | There is a security type mismatch. |
D | The channel has changed |
E | There is insufficient antenna power |
Question 108 |
A | NAS |
B | SAN |
C | FTP |
D | Jumbo frames |
E | Fiber channel |
Question 109 |
A | Private |
B | PaaS |
C | SaaS |
D | Public |
E | IaaS |
F | Hybrid |
Question 110 |
A | Mesh |
B | Bus |
C | Point-to-multipoint |
D | Ring |
E | Point-to-point |
F | Peer-peer |
Question 111 |
A | Application server |
B | Client terminal |
C | KDC |
D | RDP |
Question 112 |
A | Kerberos |
B | RADIUS |
C | WPA2 |
D | EAP-TLS |
Question 113 |
A | traceroute |
B | netstat |
C | ping |
D | ifconfig |
Question 114 |
A | 3 unit |
B | 1 unit |
C | 4 unit |
D | 2 unit |
Question 115 |
A | Twisted pair cabling |
B | Coaxial cabling |
C | Enterrpise APs |
D | Fiber-optic cabling |
Question 116 |
A | RJ11 |
B | F-type |
C | ST |
D | MTRJ |
E | RJ45 |
Question 117 |
A | 10.0.0.0 to 10.0.255.255 |
B | 169.254.0.0 to 169.254.255.255 |
C | 192.168.0.0 to 192.168.0.255 |
D | 224.0.0.0 to 224.0.255.255 |
Question 118 |
A | 175.255.255.255 |
B | 169.254.54.5 |
C | 192.168.1.1 |
D | 175.168.0.255 |
E | 192.168.0.1 |
Question 119 |
A | Data Link |
B | Application |
C | Session |
D | Presentation |
E | Physical |
F | Network |
G | Transport |
Question 120 |
A | Power looping |
B | Redundant circuits |
C | Dual power supplies |
D | Power redundancy |
E | Uninterruptible Power Supply (UPS) |
Question 121 |
A | Geofencing |
B | Tamper detection |
C | Face geometry |
D | Pattern recognition |
E | Biometrics |
Question 122 |
A | NGFW |
B | IDS |
C | NAS |
D | RADIUS |
Question 123 |
A | Protocol analyzer |
B | Web proxy |
C | Layer 3 switch |
D | NAT |
E | Layer 7 firewall |
Question 124 |
A | UDP |
B | ICMP |
C | TCP |
D | IGMP |
Question 125 |
A | Power redundancy |
B | UPS capability |
C | Airflow and cooling |
D | Circuit labeling |
Question 126 |
A | A shared resource problem |
B | A system-wide problem |
C | A wide area newtwork problem |
D | A network-wide problem |
E | A user application problem |
Question 127 |
A | Mesh |
B | Star |
C | Bus |
D | Ad hoc |
E | Ring |
Question 128 |
A | Control the latency of traffic across the network links |
B | Control the jitter of the affected traffic across the network links |
C | Control the attenuation of the non-voice traffic across the network links |
D | Control the EMI of the multimedia traffic across the network links |
Question 129 |
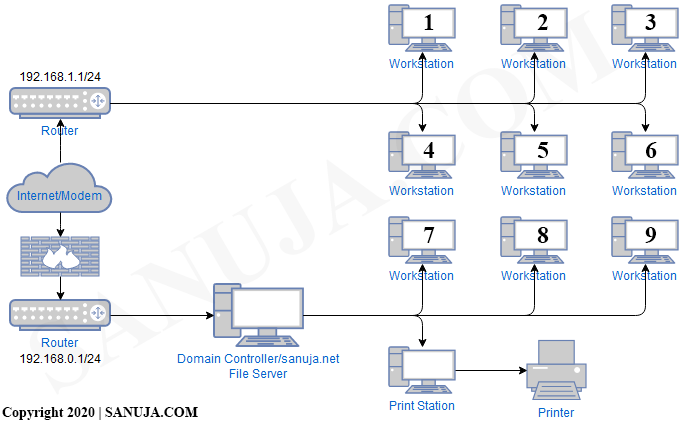
A | 192.168.0.1 |
B | 10.1.0.255 |
C | 192.168.0.55 |
D | 10.1.1.255 |
E | 192.168.1.109 |
Question 130 |
A | Coaxial |
B | Single-mode fiber optic |
C | Unshielded twisted pair |
D | Multimode fiber optic |
E | Shielded twisted pair |
Question 131 |
A | SYN, SYN/ACK, ACK |
B | SYN, SYN, ACK, ACK |
C | SYN, ACK, SYN, ACK |
D | SYN/ACK, SYN/ACK |
Question 132 |
SANUJA.COM 430 IN mx mx1.SANUJA.COM
SANUJA.COM 5 IN mx mx2.SANUJA.COM
SANUJA.COM 430 IN mx mx10.SANUJA.COM
SANUJA.COM 521 IN NS ns1.SANUJA.COM
SANUJA.COM 521 IN NS ns2.SANUJA.COM
SANUJA.COM 521 IN NS ns3.SANUJA.COM
SANUJA.COM 521 IN NS ns4.SANUJA.COM
A | NMAP –t SANUJA.COM |
B | netstat –a SANUJA.COM |
C | iptables –f SANUJA.COM |
D | dig –t ANY SANUJA.COM |
Question 133 |
A | TCP |
B | UDP |
C | IP |
D | Ethernet |
E | ICMP |
Question 134 |
A | Bridges |
B | Firewalls |
C | Hubs |
D | Routers |
Question 135 |
A | IP address |
B | Default gateway |
C | MAC address |
D | Subnet mask |
Question 136 |
A | Real-time remote monitoring of the phone’s activity and usage |
B | An NDA ensuring work data stored on the personal phone remains confidential |
C | An AUP covering how a personal phone may be used for work matters |
D | A consent to monitoring policy covering company audits of the personal phone |
Question 137 |
A | SSL tunnel |
B | SSL portal |
C | SSL gateway |
D | SSL client |
Question 138 |
A | Rack diagram |
B | Wiring schematic |
C | Building blueprints |
D | Logical diagram |
E | Network map |
Question 139 |
A | Port scanning |
B | Bluejacking |
C | Port sweeping |
D | War driving |
E | Brute-force |
Question 140 |
A | ARP |
B | NAT |
C | STP |
D | SNAT |
E | PAT |
Question 141 |
A | Cable broadband |
B | ISDN |
C | Dial-up modem |
D | DSL |
Question 142 |
A | RAID 10 |
B | RAID 5 |
C | RAID 1 |
D | RAID 0 |
Question 143 |
A | A hub |
B | A switch |
C | A gateway |
D | A router |
Question 144 |
A | PSK |
B | EAP-PEAP |
C | WEP |
D | CCMP-AES |
Question 145 |
A | Logical network diagram |
B | Physical network diagram |
C | Circuit diagrams |
D | Wiring schematic |
E | Asset management files |
Question 146 |
A | Enable port mirroring |
B | Patch and update |
C | Change default admin password |
D | Perform VLAN hopping |
E | Implement spanning tree |
F | Perform backups |
Question 147 |
A | TCP |
B | HTTP |
C | IP |
D | UDP |
Question 148 |
A | 802.1X |
B | WPA2 |
C | WEP |
D | WPA |
Question 149 |
A | ARP |
B | SCP |
C | FTP |
D | SIP |
Question 150 |
A | netstat |
B | ipconfig |
C | tcpdump |
D | traceroute |
E | iptables |
Question 151 |
A | Permit 192.168.1.143 port 110 |
B | Permit 192.168.1.143 port 80 |
C | Permit 192.168.1.143 port 587 |
D | Permit 192.168.1.143 port143 |
E | Permit 192.168.1.143 port 25 |
F | Permit 192.168.1.143 port 443 |
Question 152 |
A | There is less local congestion on the wireless network |
B | The wireless access points were misconfigured |
C | The testing server for the wired network was farther away |
D | The firewall is configured to throttle traffic to specific websites |
Question 153 |
A | 990 |
B | 80 |
C | 25 |
D | 443 |
E | 110 |
Question 154 |
A | A |
B | MX |
C | TXT |
D | NS |
E | AAAA |
Question 155 |
A | Captive portal |
B | Port security |
C | Access control lists |
D | WPA2 |
Question 156 |
A | Network management |
B | Site-to-site VPN |
C | Fault tolerance |
D | Distributed server system |
E | Remote connection |
Question 157 |
A | Multimeter |
B | Cable tester |
C | Loopback adapter |
D | Tone generator |
Question 158 |
A | PaaS |
B | Hosted |
C | IaaS |
D | SaaS |
E | VPN |
Question 159 |
A | tracert |
B | ipconfig |
C | netstat |
D | ping |
E | ifconfig |
Question 160 |
A | RJ45 |
B | USB 2.0 |
C | DB9 |
D | RC5 |
E | USB 3.0 |
Question 161 |
A | VLAN hopping is a brute force attack executed to gain additional access. Session hijacking involves physically disrupting a network connection. |
B | VLAN hopping is the act of exploiting poor VLAN tagging. Session hijacking is a web-based attack aimed at privilege escalation. |
C | VLAN hopping involves the unauthorized transition from one VLAN to another to gain additional access. Session hijacking involves overriding a user’s web connection to execute commands. |
D | VLAN hopping involves overriding a user network connection to execute malicious commands. Session hijacking involves compromising a host to elevate privileges. |
Question 162 |
A | hardware security |
B | tamper detection |
C | device hardening |
D | biometrics |
E | asset tracking |
Question 163 |
A | TACACS+ |
B | Single sign-on |
C | LDAP |
D | Local authentication |
Question 164 |
A | T-3 |
B | OC-1 |
C | E-1 |
D | T-1 |
Question 165 |

A | Remove the firewall between the Internet/modem and the router. |
B | Add additional printers across both NATs. |
C | Add a firewall between the domain controller and the router. |
D | Remove one of the routers and if requires use VLANs to create separate subnets with specific firewall rules. |
Question 166 |
A | HDSL |
B | RADSL |
C | VDSL |
D | IDSL |
Question 167 |
A | Telnet |
B | SSH |
C | IPSec |
D | SSL |
Question 168 |
A | Authentication server |
B | HTTPS server |
C | Secure server |
D | VPN gateway |
E | Encryption key |
Question 169 |
A | Asset management files |
B | Circuit diagrams |
C | Physical network diagram |
D | Logical network diagram |
E | Wiring schematic |
Question 170 |
A | Layer 3 |
B | Layer 5 |
C | Layer 6 |
D | Layer 1 |
E | Layer 7 |
F | Layer 4 |
G | Layer 2 |
Question 171 |
A | Layer 4 |
B | Layer 3 |
C | Layer 2 |
D | Layer 1 |
Question 172 |
A | Crosstalk |
B | Latency |
C | EMI |
D | Signal attenuation |
Question 173 |
A | Combined mode |
B | Hot backup mode |
C | Redundant mode |
D | High-efficiency mode |
E | Individual mode |
Question 174 |
A | Install an inline tap |
B | Periodically view the server logs |
C | Configure port aggregation |
D | Use port mirroring |
E | Use SQL injectors |
Question 175 |
A | Millimeters |
B | Number of screw holes |
C | Inches |
D | Centimeters |
E | Units |
Question 176 |
A | Security |
B | Setup |
C | Application |
D | System |
Question 177 |
A | RTO |
B | MIB |
C | RAID |
D | RPO |
E | BCP |
Question 178 |
A | Gateway |
B | Bridge |
C | Switch |
D | Router |
Question 179 |
A | arp -d |
B | arp -s |
C | arp -t |
D | arp -c |
E | arp -a |
Question 180 |
A | 143 |
B | 989 |
C | 25 |
D | 110 |
E | 80 |
Question 181 |
A | DNS round robin |
B | Muti-ISP connections |
C | RAID 1 |
D | NIC teaming |
E | Server clustering |
Question 182 |
A | Branch-to-server |
B | Extranet |
C | Site-to-site |
D | Host-to-site |
E | Host-to-host |
Question 183 |
A | Set up an SSH session to the desktop. |
B | Configure port security on the switch. |
C | Reference the ARP table in the router. |
D | Perform a DNS lookup on the server. |
Question 184 |
A | Loss of full control over data resources |
B | Inconsistent data accessability |
C | Incompatibility with the current network |
D | Increased malware exposure |
E | Decreased performance of the internal network |
Question 185 |
A | RJ-45 |
B | RG-58 |
C | RG-8 |
D | RJ-11 |
Question 186 |
A | RJ45 |
B | LC |
C | F-type |
D | MTRJ |
E | ST |
F | RJ11 |
Question 187 |
A | Data usage limits |
B | Throttling |
C | Session hijacking |
D | Blocking |
E | Bandwidth quotas |
Question 188 |
A | IPv6 |
B | QoS |
C | VoIP |
D | CARP |
E | SSL |
Question 189 |
A | Configure geofencing |
B | Enable WPA and change the SSID |
C | Have the ISP double the bandwidth |
D | Move from WPA2 to WEP |
Question 190 |
A | The public key |
B | The ticket granting key |
C | The secure key |
D | The session key |
E | The private key |
Question 191 |
A | 4 |
B | 0 |
C | 3 |
D | 2 |
E | 1 |
Question 192 |
A | NDA |
B | SLA |
C | BYOD |
D | IRP |
Question 193 |
A | Motion detection |
B | Video surveillance |
C | Smartcards |
D | Biometrics |
Question 194 |
A | 10GBase-LX4 |
B | 10GBase-SR |
C | 10GBase-LR |
D | 10GBase-CX4 |
E | 10GBase-ER |
Question 195 |
A | Syslog |
B | Top |
C | Netmon |
D | Netstat |
Question 196 |
A | RAID 10 |
B | RAID 1 |
C | RAID 0 |
D | RAID 5 |
Question 197 |
A | Somewhere you are |
B | Something you have |
C | Something you know |
D | Something you do |
Question 198 |
A | 110 block |
B | Fiber distribution panel |
C | Patch panel |
D | CMTS |
E | 66 block |
Question 199 |
A | Bridge |
B | Switch |
C | Router |
D | Hub |
Question 200 |
A | Window |
B | WinMS |
C | MMS |
D | MSS |
← |
List |
→ |
| 1 | 2 | 3 | 4 | 5 |
| 6 | 7 | 8 | 9 | 10 |
| 11 | 12 | 13 | 14 | 15 |
| 16 | 17 | 18 | 19 | 20 |
| 21 | 22 | 23 | 24 | 25 |
| 26 | 27 | 28 | 29 | 30 |
| 31 | 32 | 33 | 34 | 35 |
| 36 | 37 | 38 | 39 | 40 |
| 41 | 42 | 43 | 44 | 45 |
| 46 | 47 | 48 | 49 | 50 |
| 51 | 52 | 53 | 54 | 55 |
| 56 | 57 | 58 | 59 | 60 |
| 61 | 62 | 63 | 64 | 65 |
| 66 | 67 | 68 | 69 | 70 |
| 71 | 72 | 73 | 74 | 75 |
| 76 | 77 | 78 | 79 | 80 |
| 81 | 82 | 83 | 84 | 85 |
| 86 | 87 | 88 | 89 | 90 |
| 91 | 92 | 93 | 94 | 95 |
| 96 | 97 | 98 | 99 | 100 |
| 101 | 102 | 103 | 104 | 105 |
| 106 | 107 | 108 | 109 | 110 |
| 111 | 112 | 113 | 114 | 115 |
| 116 | 117 | 118 | 119 | 120 |
| 121 | 122 | 123 | 124 | 125 |
| 126 | 127 | 128 | 129 | 130 |
| 131 | 132 | 133 | 134 | 135 |
| 136 | 137 | 138 | 139 | 140 |
| 141 | 142 | 143 | 144 | 145 |
| 146 | 147 | 148 | 149 | 150 |
| 151 | 152 | 153 | 154 | 155 |
| 156 | 157 | 158 | 159 | 160 |
| 161 | 162 | 163 | 164 | 165 |
| 166 | 167 | 168 | 169 | 170 |
| 171 | 172 | 173 | 174 | 175 |
| 176 | 177 | 178 | 179 | 180 |
| 181 | 182 | 183 | 184 | 185 |
| 186 | 187 | 188 | 189 | 190 |
| 191 | 192 | 193 | 194 | 195 |
| 196 | 197 | 198 | 199 | 200 |
| End |
Based on general knowledge and CompTIA guidelines published in 2020.
FAQ | Report an Error
Study outline at: CompTIA Exams Guide
Disclaimer: While every reasonable effort is made to ensure that the information provided is accurate, no guarantees for the currency or accuracy of information are made. It takes several proof readings and rewrites to bring the quiz to an exceptional level. If you find an error, please contact me as soon as possible. Please indicate the question ID-Number or description because server may randomize the questions and answers.