The plain HTML based websites are no longer popular on the net. This is because the PHP based Content Management Systems (CMS) offer wide range of flexible solutions. From development stand point CMS programs allow easy integration of different tools such as jQuery, JavaScipt, PHP scripts and many more. From end-user point of view, it is much easier to manage a CMS based site like a WordPress or a Drupal site than to carefully edit each HTML page.
Problem
The problem is when a CMS program like WordPress become a popular tool (even used by US Government agencies and large corporations), the platform become a hotbed for hackers. The hackers not only target governments and large organizations, but also go after the little guys like SANUJA.COM. So, why do you care? Well, you should care because even with very good backup files, it takes time and resources to fix infiltrated servers. Even if you restore from a backup or reinstall your CMS, the hackers can leave behind secret files with damaging codes that may not be easy to detect. Therefore prevention is a much better option compared to solving the issues arise from a successful hack.
Why do they do it?
Severs can be classified as distribution points on a network. There are hundreds of thousands of servers on the Internet. In order for someone to send or receive data, the sender and the receiver get connected to several servers. Usually when good guys do this, the access points and servers can be identified by their IP (Internet Protocol) or domain addresses. However, hackers use scripts to hijack servers so the actual sender cannot be identified (or difficult to identify). Once hijacked, they can use the servers for illegal activities such as routing stolen credit card data/transactions and distribution of child pornography or for unethical activities such as sending spam emails. These illegal activities on your web servers will result in over use of your bandwidth and other resources. In extreme cases, hacking can result in complete loss of all data including the backup files.
The hackers usually leaves plenty of evidence for the hack itself. But under most Terms of Use agreements between the web hosting provider and the developer or site owner (“site owner”), it is the site owners’ responsibility to protect the account from hackers. A web hosting provider may add a surcharge to your account or even terminate it on the grounds of infiltrated servers.
Prevention of access
There are simple solutions and there are more advanced solutions. If your website is popular or getting popular (like SANUJA.COM), then I recommend the advanced options. But if it is a simple blog site, you may get away with just simple restrictions.
Easy simple solutions
1. Accounts: Always use long and complicated passwords. Never ever use your name or your site’s name in your password. Replace the accounts with common usernames such as “admin” or “user” with different ones. For example the administration account username should never be “admin” but may be “clearcut” or “clear-cut”. Additionally change usernames and passwords occasionally.
2. Malware: Make sure that the computer you use to access your sever or website is free of malware.
3. Captcha: Use graphical authentication like reCaptcha to prevent brute-force attacks on login pages. Set the captcha security to the highest setting possible (more characters, more designs, etc).
4. Security Plugins/Modules: Both WordPress and Drupal have several free security plugins and modules. Some of them are really good. For example, Login LockDown or Wordfence. There are also paid Pro versions of these plugins. If you own a poplar website, consider paying for the pro version because they worth every penny.
5. SSL HTTPS: If you are running a business, consider using HTTPS secure certificate for either admin side of your site or for the entire site. The cost of HTTPS certificate fees are insignificant compared to the data protection you get with SSL (Secure Sockets Layer). Even if you do not want to use SSL, it is very important to use it on any pages that accept direct payments or collect sensitive personal data. Most SSL certificates also comes with liability insurance to protect the site owner in case of a data breach.
Advanced solutions
Sometimes you can achieve the same or comparable amount of security as the professional plugins by manipulating the server side scripts and files. But this will take a bit of knowledge and you may have to take a risk of editing critical files. If you make a mistake, the site may go offline or loaded with errors. Do not try to do this if you think you are not capable of handing errors and issues.
1. 401 Access restriction solution
You can secure the wp-admin area of your WordPress install by two factor authentication using .htaccess file on cPanel. Here is how you do it.
I. Login to your cPanel then select Password Protect Directories
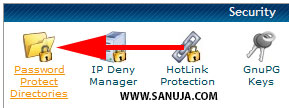
II. Find the wp-admin folder and select it.
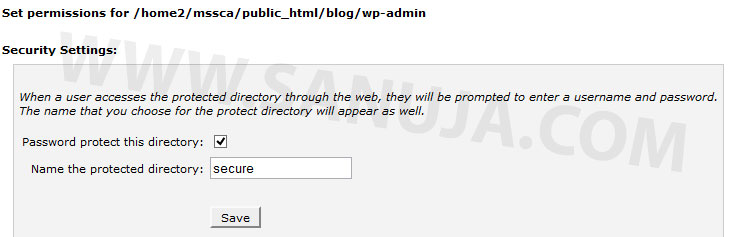
III. Under Security Settings, select (check mark) Password protect this directory. Then give a name like “secure” or whatever you like. The name given will not effect the security of the folder. Then press Save.
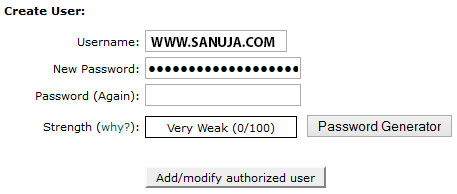
III. Create a Username and a Password under Create User and press “Add/modify authorized user”.
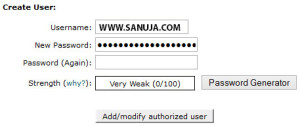
IV. Now you may encounter one or both of the following common problems associated with 401 restrictions. One is that the 401 login request may pop-up on every page of your WP site. The other is the redirection loop problem in which the user will be redirected to the main site over and over even after the correct credentials are entered.
The pop-up message is caused by the plugins and scripts trying to access the admin area for legitimate use. Therefore you should add a bypass for admin-ajax.php file at the top of your .htSo solve this problem, go to your wp-admin folder and add the following to the top of your .htaccess file in your wp-admin folder.
<Files admin-ajax.php> Order allow,deny Allow from all Satisfy any </files>
If you want the 401 and 403 Denied pages to load when the authentication fails, all the following to the very top of the .htaccess file.
ErrorDocument 401 "Denied" ErrorDocument 403 "Denied"
The final .htaccess file within the wp-admin folder will look like the following.
#Error code call ErrorDocument 401 "Denied" ErrorDocument 403 "Denied" # Allow admin-ajax.php <Files admin-ajax.php> Order allow,deny Allow from all Satisfy any </files> # Protected wp-admin folder AuthType Basic AuthName "secure" AuthUserFile "/home/.htpasswds/public_html/wp-admin/passwd" require valid-user
V. Finally add the protection to the wp-login.php file from the main directory by adding the following to .htaccess file in the main folder.
<FilesMatch "wp-login.php"> AuthType Basic AuthName "secure" AuthUserFile "/home/.htpasswds/public_html/wp-admin/passwd" require valid-user </FilesMatch>
You should now get a two factor authentication for administration access. The pop-up longin request is the 401 request we just created. Please beware that if you make an error .htaccess file, you will encounter 500 Internal Server Error message.
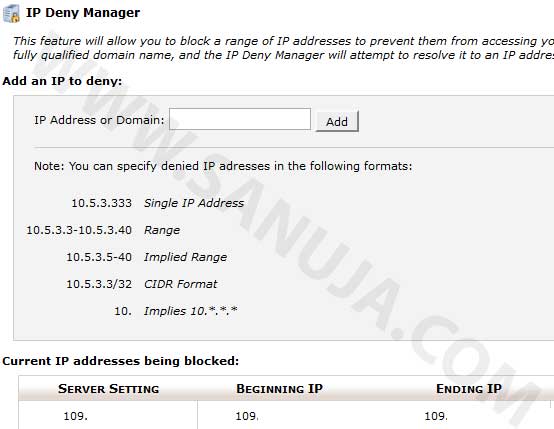
2. IP Banning: This can be done with either using a plugin (WP) or a module (Drupal). But you can also block the access to the entire site from the back-end of your server. You can block either one IP, several IPs or a range of IPs. You can do this on cPanel under IP Deny Manager in Security. The problem with this approach is that ISPs often reassign IPs to their clients. A bad IP or a bad range of IPs during one time period may not be bad the next time. Hence you may block access to legitimate users.
3. PHP scripts: There are PHP parameters (IP address, host, username, password, etc) you can use to block access to sever content. You can either write a script yourself or find one online. However, the level of security you achieved by PHP scripts highly depend on how well the script is written and what PHP version you use. Often PHP scripts are used for simple password protection for basic web pages. To increase security, most password security type pulgins (WP) and modules (Drupal) use a combination of PHP and SQL to protect your site.
Other servers/platforms
You can do everything described above on other types of non-cPanel based servers. For Windows based servers, you edit web.config file as opposed to .htaccess file. The code you use in web.config file is different from what I have posted above. I may post a detailed article on how to do them on some later time. Those who are on other platforms I hope this article (at least) provided you with some information on the options available to system administrators.