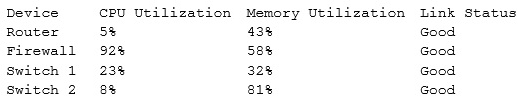Notice
This is the non-interactive basic mode of COMP TIA Network+ N10-007 questions database for printing or use in case of SQL database failure on main site. All the questions and answers are identical except the order of questions and answers.Please use the interactive version for more up to date materials.
COMPTIA N10-007
1. All of the following protocols are used to secure virtual private network (VPN) connections except _____________. (ID-NTIA-125)
A. L2TP
B. PPTP
C. FTPS
D. IPsec
2. Which of the following WAN technologies swaps the header on a packet when internally switching from one provider router to another? (ID-NTIA-481)
A. PPP
B. MPLS
C. ATM
D. Frame relay
Question 2 Explanation: Multiprotocol Label Switching (MPLS)
3. MIMO technology in the 802.11n standard provides for which of the following benefits? (ID-NTIA-500)
A. Gigabit wireless bandwidth
B. Channel bonding
C. Multipath support
D. Channel expansion
4. A technician is installing two new servers that collect logs. After installing the servers, the technician reviews the logical output from various commands. Which of the following should be included in a logical network diagram? (ID-NTIA-379)
A. Media type
B. Rack location
C. Hostname
D. Room number
5. An end-user device requires a specific IP address every time it connects to the corporate network, however, the corporate policy does not allow the use of static IP addresses. Which of the following will allow the request to be fulfilled without breaking the corporate policy? (ID-NTIA-157)
A. DHCP reservation
B. DHCP restriction
C. DHCP relay
D. DHCP option
E. DHCP exclusion
6. To increase speed and availability, a high-traffic web application was split into three servers recently and moved behind a load balancer. Which of the following should be configured on the load balancer to allow for a single destination? (ID-NTIA-188)
A. VIP
B. SIP
C. NAT
D. PAT
Question 6 Explanation: Virtual IP (VIP)
7. You have been tasked with testing a CAT5 cable. A summary of the test results can be found on the following table. Which tool was used to create the cable test results? (ID-NTIA-509)
| Cable | Test | Result |
|---|---|---|
| 1.2 | Open | 7ft |
| 3.6 | Short | 7ft |
| 4.5 | Open | 7ft |
| 7.8 | Open | 7ft |
A. Protocol Analyzer
B. Toner Probe
C. OTDR
D. Crimper
E. Multimeter
F. Punch Down Tool
G. Cable Certifier
Question 7 Explanation: The test results indicate incorrectly crimped cable.
8. The DOCSIS (specification) is used by which for the following Internet connection types? (ID-NTIA-169)
A. ISDN
B. Cable broadband
C. Dial-up modem
D. DSL
Question 8 Explanation: Data Over Cable Service Interface Specification (DOCSIS)
9. A new monitoring device is installed in the network that uses ping to determine whether critical network Internet routers are up. After three missing pings, the alarm reports the device is down. The device is now constantly reporting alarms, yet there are no reported Internet problems from users. Which of the following is the MOST likely cause? (ID-NTIA-530)
A. Incorrect VLAN assignment on the router
B. A missing route on the network routers
C. A missing route on the alarm device
D. Incorrect speed/duplex setting on the alarm device
10. A workstation on the network is configured as follows. A user reports that they are unable to print to a device located on a different subnet. Which of the following is the most likely problem? (ID-NTIA-470)
IP address: 172.16.204.12
Subnet Mask: 255.255.0.0
Default Gateway: 172.15.204.254
DNS address: 172.16.204.1
Broadcast address: 172.16.255.255
A. Default gateway
B. Broadcast address
C. Subnet mask
D. DNS address
E. IP address
11. A network technician has been asked to create secure private networks between a company’s headquarters and several branch locations. The company has provided the on-premises equipment, but each branch has a different ISP. Which of the following technologies should the technician consider using to accomplish this? (ID-NTIA-270)
A. Client-to-site
B. Point-to-multipoint
C. Site-to-site
D. Point-to-point
12. A network technician is installing and configuring a new router for the sales department. Once the task is complete, which of the following needs to be done to record the change the technician is masking to the company network? (ID-NTIA-303)
A. Network diagrams
B. Change management
C. Labeling report
D. Inventory report
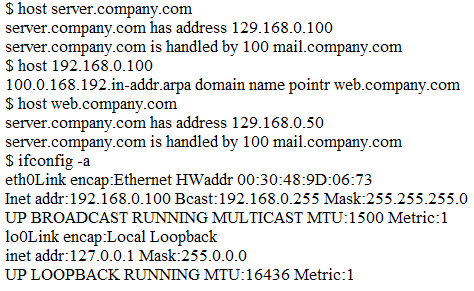
13. A network technician is configuring a firewall access list to secure incoming connections to an email server. The internal address of this email server is 192.168.1.143. The firewall should allow external email servers to send email to the email server. The email server also supports client access via a web browser. Only secure protocols should be used, and only the necessary ports should be open. Which of the following ACL rules should be configured in the firewall’s WAN port? Choose all the correct answers. (ID-NTIA-153)
A. Permit 192.168.1.143 port 587
B. Permit 192.168.1.143 port 110
C. Permit 192.168.1.143 port 443
D. Permit 192.168.1.143 port 80
E. Permit 192.168.1.143 port 25
F. Permit 192.168.1.143 port 143
Question 13 Explanation: SMTPS (mail) port is 587 or 465 and HTTPS (web access) is 443.
14. To replace a defective UPS, the network administrator must take the switch offline. The administrator wants to be able to perform maintenance UPS in the future without affecting the availability of the attached switch. Which of the following would best allow this to happen? (ID-NTIA-358)
A. Implement stacking on the switches in the rack
B. Install a power converter for the switch
C. Add a redundant power supply to the switch
D. Add a second UPS into the rack
15. A network technician wants to address PCs on a subnet with IPv6 in addition to IPv4. The subnet currently uses a DHCP server that only supports IPv4. Which of the following should the technician use to assign IPv6 addresses automatically without DHCP? (ID-NTIA-476)
A. APIPA
B. IPsec
C. IPv4 to IPv6 tunnel
D. MAC reservations
E. EUI-64
Question 15 Explanation: 64-Bit Extended Unique Identifier (EUI-64)
16. A network technician of an Internet Service Provider(ISP) was told that one of their customers cannot access the Internet. Upon investigation, the technician realized the customer has added a router, a day before, behind their ISP provided modem/router combo unit in order to increase the number of LAN ports. Which of the following has the user most likely introduced to the network? (ID-NTIA-154)
A. Packet intrusion
B. Evil twin
C. VLAN mismatch
D.Rogue DHCP server
E. Honey pot
Question 16 Explanation: If the customer wants to use their own router, the modem/router combo unit must be set to bridge mode (sometimes call passthrough mode).
17. A network technician is setting up the wireless network for a company’s new branch office. After doing a site survey, the technician discovers there is a lot of interference from 2.4GHz devices at the location on channel 11. Which of the following would be the BEST channel on which to set up the WAPs? (ID-NTIA-284)
A. Channel 9
B. Channel 6
C. Channel 10
D. Channel 7
18. Which of the following connector types was typically associated with a T-connector attached to the computer? (ID-NTIA-09)
A. MTRJ
B. F-type
C. RJ45
D. BNC
E. 8P8C
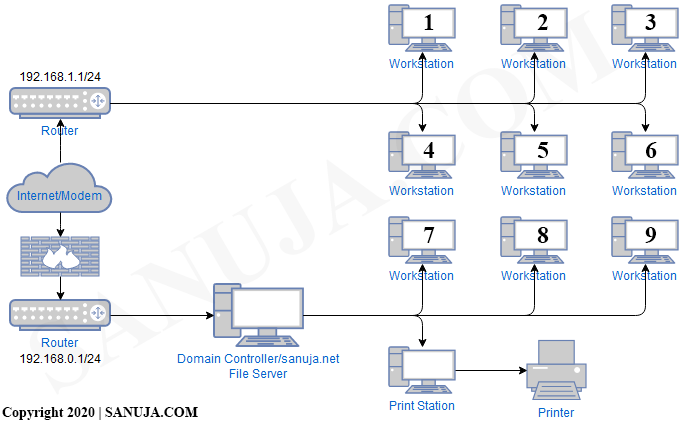
19. Answer the following question based on the network diagram below. You were hired as an IT consultant and told to improve the following network. What might be something that you would recommend? Click on the image if it is hard to read. (ID-NTIA-37)
A. Add a firewall between the domain controller and the router.
B. Remove one of the routers and if requires use VLANs to create separate subnets with specific firewall rules.
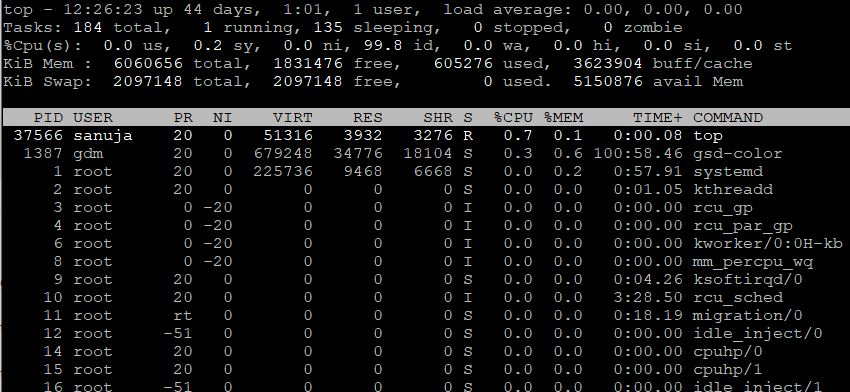
C. Add additional printers across both NATs.
D. Remove the firewall between the Internet/modem and the router.
20. Management is concerned there is excessive traffic on the network. A network technician wants to run a quick port scan to see any systems that have open ports. Which of the following tools should be used to do this? (ID-NTIA-197)
A. tcpdump
B. dig
C. nmap
D. netstat
21. A corporate manager says wireless phones do not work properly inside the main building. After a troubleshooting process, the network administrator detects that the voice packets are arriving on the wireless phones with different delay times. Which of the following performance issues is the company facing? (ID-NTIA-308)
A. Latency
B. Attenuation
C. Frequency mismatch
D. Jitter
22. A technician replaced a malfunctioning network switch with an identical new switch from the same vendor. The model and hardware version of the new switch matched the broken unit. The technician extracts the config files from the old unit and installs it on the new unit. After installation, the new switch boot up and shuts down itself. Considering that the hardware is identical, which of the following is the most likely cause of the failure? (ID-NTIA-161)
A. Double NAT issue
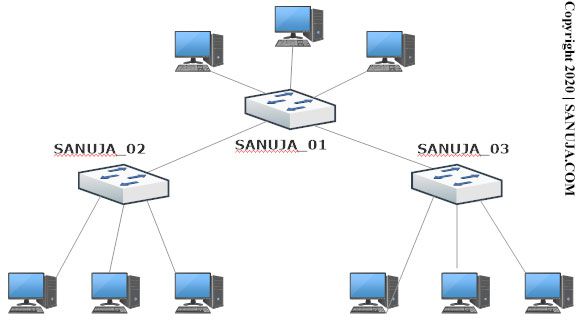
B. Damaged or malfunctioning LAN port
C. VLAN mismatch
D. Damaged or malfunctioning fiber port
E. Corrupted config files or operating system
Question 22 Explanation: In my experience, you always take a risk when you migrate a firmware config files from one unit to another even when hardware versions match. If you have the time, it is sometimes better to reconfigure firmware of network equipment rather than loading from a backup on new equipment. The backups are useful when you need to reload the firmware to the same hardware.
23. Which of the following authentication methods is most secure? (ID-NTIA-517)
A. Kerberos
B. NTLM
C. MS-CHAP
D. CHAP
24. Which of the cabling types listed below is the most susceptible to EMI/RFI? (ID-NTIA-239)
A. Fiber-optic cabling
B. UTP cabling
C. STP cabling
D. Coaxial cabling
25. In the following diagram, what is the type of optical fiber connector illustrated by II? (ID-NTIA-446)
A. SC
B. MT-RJ
C. LC
D. ST
26. A few weeks after starting a new position, Joe, a junior network administrator, receives a call from an internal number asking for his username and password to update some records. Joe realizes this may be a type of attack on the network since he has full access to network resources. Which of the following attacks is described? (ID-NTIA-325)
A. Social engineering
B. rojan horse
C. Session hijacking
D. Insider threat
E. Logic bomb
27. A wireless client is having issues staying connected to the wireless network even though the client is less than 20ft (6m) from the access point. Which if the following is most likely the cause? (ID-NTIA-534)
A. Latency
B. Absorption
C. Distance limitations
D. Security type mismatch
28. Which of the following bridging types has never been used on Ethernet local area networks (LANs)? (ID-NTIA-87)
A. Multiport
B. Source route
C. Store and forward
D. Transparent
29. A bookstore uses a Faraday cage to comply with credit card regulations. Customers report that their cellular phones have no signal when they are in the bookstore. Which of the following is the most likely cause? (ID-NTIA-251)
A. The Faraday cage prevents access by redirecting signals.
B. The Faraday cage is creating interference within the bookstore.
C. The Faraday cage is creating latency on the cellular network.
D. The Faraday cage is creating attenuation of the cellular network.
30. Which of the following wide-area networking (WAN) services provides the fastest transfer rate? (ID-NTIA-168)
A. E-1
B. OC-1
C.T-1
D. T-3
31. A network technician has purchased a 10GBase-T switch and wishes to connect it to 30 computers with 10GB network cards. The computers are 225ft (69m) away, and all need to establish a 10 Gbps connection to meet business requirements. To minimize costs while still meeting these requirements, which of the following cable types should the technician choose? (ID-NTIA-264)
A. Cat 5e
B. Cat 6
C. Cat 6a
D. Cat 7
32. Which of the following protocols is used by Active Directory for authentication? (ID-NTIA-289)
A. LDAP
B. SSH
C. SFTP
D. TLS
33. A Chief Information Officer (CIO) is concentrated about an attacker gaining administrative access to the company’s network devices. Which of the following is the most secure way to prevent this? (ID-NTIA-411)
A. ACL allowing only Telnet
B. Out-of-band modem
C. ACL allowing only HTTP
D. Out-of-band console router
34. A Chief Information Security Officer (CISO) has decided to implement a secure and user-friendly way to connect to the corporate wireless network. Each workstation will be authenticated individually using a unique certificate that will be deployed to the workstation by the organization’s certificate authority. Which of the following authentication methods would meet this requirement? (ID-NTIA-252)
A. EAP-TLS
B. Captive portal
C.WP2-PSK
D. PEAP
Question 34 Explanation: Extensible Authentication Protocol-Transport Layer Security (EAP-TLS)
35. Which of the answers listed below refers to a possible symptom of exhausted DHCP scope? (ID-NTIA-231)
A. Loopback address
B. APIPA address
C. Duplicate MAC addresses
D. Duplicate IP addresses
Question 35 Explanation: APIPA (Automatic Private IP Addressing) is issued when DHCP IP addresses being used and the new network device cannot obtain an IP.
36. An 801.11g wireless access point was configured as follows: (ID-NTIA-465)
– AP encryption forced to WPA2-AES mode only
– MAC address filtering enabled with the following MAC address in the allow list: 00-ab-29-da-c3-40
Which is true about the above configuration?
A. An 802.11a compatible client can connect to the wireless network only if its MAC address is 00- ab-29-da-c3-40 and the encryption key is known by the client.
B. An 802.11n compatible client can connect to the wireless network only if its MAC address is 00- ab-29-da-c3-40 and the encryption key is known by the client.
C. Any 802.11g compatible client can connect to the wireless network if the encryption key is known by the client.
D. Any 802.11b/g compatible client can connect to the wireless network if they support TKIP, the MAC address is 00-ab-29-da-c3-40, and the encryption key is known by the client.
37. A network administrator is concerned about clients being able to access the local Internet while connected to the corporate VPN. Which of the following should be disabled on the client to prevent this? (ID-NTIA-475)
A. Split tunneling
B. TLS
C. HTTPS
D. Remote file access
38. A network engineer at a government agency is restricting Internet browsing on the corporate WAN to only government-related external websites. Which of the following is the best solution to achieve this goal while avoiding the need to configure this restriction on each PC? (ID-NTIA-185)
A. Web application firewall
B. Content filter
C. IPS
D. VLAN restrictions
E. VPN concentrator
39. A project lead is reviewing the statement of work for an upcoming project that is focused on identifying potential weaknesses in the organization’s internal and external network infrastructure. As part of the project, a team of external contractors will attempt to employ various attacks against the organization. The statement of work specifically addresses the utilization of an automated tool to probe network resources in an attempt to develop logical diagrams indication weaknesses in the infrastructure. The scope of activity as described in the statement of work is an example of ____________. (ID-NTIA-147)
A. session hijacking
B. friendly DoS
C. penetration testing
D. vulnerability scanning
E. social engineering
40. A shop owner wants to ensure that only a specified group of devices can access the wireless network. Which of the following methodologies will best ensure unauthorized devices cannot consume the shop owner’s limited Internet bandwidth? (ID-NTIA-268)
A. Activate MAC address filtering.
B. Disable the SSID broadcast.
C. Implement WEP authentication.
D. Change the WiFi password.
41. A network technician notices the site-to-site VPN and Internet connection have not come back up at a branch office after a recent power outage. Which of the following is an out-of-band method the technician would most likely utilize to check the branch office’s router status? (ID-NTIA-155)
A. Use a modem to console into the router
B. Travel to the branch office
C. Walk a user through troubleshooting the connection
D. Hire a third-party contractor to go on-site
42. What connector would you use with RS-232? (ID-NTIA-118)
A. USB 2.0
B. RJ45
C. USB 3.0
D. RC5
E. DB9
Explanation: DB9 and DB15 style connectors are also used in VGA monitors.
43. Which of the following solution sets properly addresses all of the identified requirements below? (ID-NTIA-221)
-WLAN architecture supporting speeds in excess of 150 Mbps
-Client less remote network access
-Port-based network access control
A. 802.11ac, MPLS, 802.3.
B. 802.11g, MS-CHAP, 802.16
C. 802.11n, SSL-VPN, 802.1x
D. 802.11a, IPSec VPN, 802.1x
E. 802.11b, PPTP,802.1x
44. A network support specialist is setting up wireless networks for several small companies that are leasing adjacent spaces in an office building. The network support specialist has already configured an access point for each office with WPA2-AES encryption and minimized any overlap of the wireless channels. Several of the companies have expressed concerns about performance and security issues due to the high volume of wireless networks being installed in close proximity. Which of the following actions will best mitigate the companies’ concerns? (ID-NTIA-242)
A. Disable the SSID broadcast on each access point.
B. Enable MAC address filtering on each access point.
C. Reduce the TX power on each access point.
D. Enable AP isolation on each access point.
45. A university has a lecture hall containing 100 students. Currently, the lecture hall has two 802.11ac wireless access points, which can accommodate up to 50 devices each. Several students report they are unable to connect devices to the wireless network. Which of the following is most likely the issue? (ID-NTIA-315)
A. One of the wireless access points is on the wrong frequency
B. The students are attempting to connect 802.11g devices
C. Distance limitations are preventing the students from connecting
D. The students are using more than one wireless device port seat
46. An NGFW alerts that a web server in the DMZ is sending suspicious traffic. A network administrator finds that port 25 is open, and the traffic is originating from this port. The only purpose of this server is to deliver website traffic. Which of the following should the network administrator recommend to the systems administrator? (ID-NTIA-392)
A. Disable Telnet service on the server
B. Disable the SMTP service on the server
C. Disable DHCP service on the server
D. Disable FTP service on the server
47. A network administrator wants to ensure all traffic is inspected and abides by the AUP, and that malicious traffic is stopped. Which of the following features should be enabled on a firewall to meet this requirement? (ID-NTIA-265)
A. Proxy service
B. Dynamic DNS
C. Intrusion detection
D. Content filtering
48. Which of the following technique can be used to scan multiple computers on a network for an open TCP or UDP port? (ID-NTIA-104)
A. War driving
B. Brute-force
C. Port scanning
D. Bluejacking
E. Port sweeping
49. A request is made to open an additional port on a firewall. The request is approved, and the port is opened. Which of the following BEST describes this process? (ID-NTIA-183)
A. Change management
B. Project management
C. Standard operating procedure
D. Process management
50. During a weekend event, several people reported they were unable to get onto the wireless network. On Monday, the technician could not find a problem. Which of the following is the most likely cause? (ID-NTIA-194)
A. Channel overlap
B. Cross talk
C. Wrong passphrase
D. Overcapacity
51. An assistant systems analyst reports the following findings of an investigation of slow Internet connections in a remote office to the senior systems analyst: (ID-NTIA-369)
Which of the following devices is causing the issue?
A. Switch 1
B. Router
C. Firewall
D. Switch 2
52. A network administrator needs to transmit traffic to geographically diverse sites to improve performance. Which of the following devices would BEST direct traffic to the remote sites? (ID-NTIA-370)
A. Router
B. Hub
C. Switch
D. Bridge
53. A technician needs to add ten additional Ethernet ports to a small office network. A new basic function switch is added. Hosts connected to the new switch are unable to see any computers on the network other than those connected to the new switch. Which of the following should the technician perform to ensure the hosts on the new switch can communicate with the existing network? (ID-NTIA-297)
A. Connect the switches with a cable that has a TIA/EIA 586A wired connector end and a TIA/EIA 586B wired end.
B. Add a second cable connecting the switches for redundancy and disabling STP on both switches.
C. Move the straight-through Ethernet cable connecting the switches to the first port on both switches.
D. Replace the new switch with a hub to ensure Layer1 connectivity on the new network segment.
54. Which of the following operate only within the UDP protocol? (ID-NTIA-322)
A. Packets
B. Frames
C. Segments
D. Datagrams
55. Which of the following network topologies typically has all devices on a network directly connected to every other network device? (ID-NTIA-206)
A. Mesh
B. Ad hoc
C. Ring
D. Star
56. A building is equipped with light sensors that turn off the fluorescent lights when natural light is above a certain brightness. Users report experiencing network connection issues only during certain hours. The west side of the building experiences connectivity issues in the morning hours and the east side near the end of the day. At night the connectivity issues affect the entire building. Which of the following could be the cause of the connectivity issues? (ID-NTIA-144)
A. Network wiring is run perpendicular to electrical conduit
B. Temperature changes are causing attenuation in copper cabling
C. Light sensors are interfering with the network
D. EMI from the lights is interfering with the network cables
Question 56 Explanation:This question is extracted word-to-word from a real N10-007 exam from CompTIA. Some argue the answer should be EMI from the lights is interfering with the network cables. If the wires come in contact with one another it will cause interference, in this case, they are running one over the other instead of side by side which would eliminate the interference..
57. Two WAPs are positioned with overlapping coverage, but seamless roaming across them is not working. Which of the following should be checked? (ID-NTIA-529)
A. WAPs are transmitting on same channel
B. WPA should be enabled
C. PKI should be turned off
D. WAP SSIDs are matching
58. A technician is replacing a failed SOHO router for a customer who has an existing switch, cable modem, and static IP address. The user has a web server that faces the Internet so users can visit and leave comments. Which of the following BEST describes the correct configuration for this customer’s requirements? (ID-NTIA-427)
A. The modem is placed in bridge mode, the router is placed behind the modem, and the web server is placed behind the router
B. The switch is placed in bridge mode, the modem is placed behind the router, and the router is placed behind the modem
C. The router is placed in bridge mode, the modem is placed behind the router, and the web server is placed behind the modem
D. The web server is placed in bridge mode, the router is placed behind the web server, and the modem is placed behind the router
59. A network manager is concerned about visitors taking advantage of open cubicles at a company’s facilities. Which of the following would mitigate this issue? (ID-NTIA-246)
A. Create a honeypot to attract attackers.
B. Implement a DMZ for all external services.
C. Create a VLAN for all unused switchports.
D. Implement root guard on all switches.
60. Which of the following should be implemented in a networked environment carrying teleconferencing packets? (ID-NTIA-457)
A. L2TP
B. SNMP
C. QoS
D. SSH
61. When querying a DNS server for an AAAA record, which of the following is an appropriate response? (ID-NTIA-474)
A. 00:f3:82:99:a2:b8
B. 192.168.2.1
C. 61.23.168.192.in-addr.arpa
D. 3ffe:1900:4545:3:200:f8ff:fe21:67cf
62. A government employee breaches privacy by accessing server data without permission and as a result, his employment contract was terminated abruptly. Which of the following IT policies would best describe this situation? (ID-NTIA-203)
A. Incident response
B. DLP
C. AUP
D. Remote access
E. Offboarding
63. A network technician has implemented ACLs to limit access to cloud-based file storage. Which of the following security mechanisms has the technician enforced? (ID-NTIA-416)
A. DLP
B. IDS
C. WPA
D. WAF
E. TPM
64. A network technician has created a network that consists of a router, a firewall, a switch, and several PCs. Which of the following physical network topologies was created? (ID-NTIA-347)
A. Star
B. Mesh
C. Ring
D. Bus
65. A technician is setting up a direct connection between two older PCs so they can communicate but not be on the corporate network. The technician does not have access to a spare switch but does have spare Cat 6 cables, RJ-45 plugs, and a crimping tool. The technician cuts off one end of the cable. Which of the following should the technician do to make a crossover cable before crimping the new plug? (ID-NTIA-336)
A. Reverse the wires leading to pins 1 and 3
B. Reverse the wires leading to pins 1 and 2
C. Reverse the wires leading to pins 2 and 4
D. Reverse the wires leading to pins 2 and 3
66. VLANs create the administrative boundaries on a switched network that are otherwise provided by which of the following devices? (ID-NTIA-33)
A. Hubs
B. Bridges
C. Firewalls
D. Routers
67. Which network topology requires the installation of terminating resistors at two locations? (ID-NTIA-73)
A. Ad hoc
B. Mesh
C. Bus
D. Star
E. Ring
68. A technician is troubleshooting intermittent connectivity on a line-of-sight wireless bridge. Which of the following tools should the technician use to determine the cause of the packet loss? (ID-NTIA-397)
A. Spectrum analyzer
B. OTDR
C. Packet sniffer
D. Multimeter
69. Which of the following is a feature on high availability systems that enables them to automatically detect problems and react to them? (ID-NTIA-27)
A. Backups
B. Snapshots
C. Cold sites
D. Failover
Question 69 Explanation:Failover has been a typical automated feature of high availability systems for a long time. However, backups and cold sites are also features of high avialability syetems, but not automaically reactive.
70. Which of the following is a proprietary routing protocol? (ID-NTIA-489)
A. RIP
B. OSPF
C. BGP
D. EIGRP
Question 70 Explanation: Enhanced Interior Gateway Routing Protocol (EIGRP)
71. Which of the following can be used to prevent unauthorized employees from entering restricted areas? (ID-NTIA-253)
A. Motion sensors
B. Video cameras
C. Sign-in sheets
D. Swipe badges
72. A customer wants to set up a guest wireless network for visitors. The customer prefers to not have a password on the network. Which of the following should a technician set up to force guests to provide information before using the network? (ID-NTIA-291)
A. TACACS+
B. Single sign-on
C. RADIUS
D. Captive portal
73. The backups server connects to a NAS device using block-level storage over Ethernet. The performance is very slow, however, and the network technician suspects the performance issues are network-related Which of the following should the technician do to improve performance? (ID-NTIA-165)
A. Enable jumbo frames on the NAS and server
B. Utilize UDP to eliminate packet overhead
C. Turn off MDIX settings on the NAS and server switchports
D. Encapsulate the storage traffic in a GRE tunnel
74. Ann, a network technician, has just installed a fiber switch in a datacenter. To run the fiber cabling, Ann plans the cable route over the top of the rack using the cable trays, down to the switch, coiling up any excess cable. As Ann configures the switch, she notices several messages in the logging buffer stating the receive signal of the SFP is too weak. Which of the following is MOST likely the cause of the errors in the logging buffer? (ID-NTIA-491)
A. Fiber cable mismatch
B. Bad fiber switch
C. Fiber type mismatch
D. Bend radius exceeded
75. A technician is diagnosing an issue with a new T1 connection. The router is configured, the cable is connected, but the T1 is down. To verify the configuration of the router, which of the following tools should the technician use? (ID-NTIA-164)
A. Multimeter
B. Cable tester
C. Tone generator
D. Loopback adapter
76. A technician has a remote site that often has congestion issues. When this happens, the remote router cannot be managed using SSH because the session drops. Which of the following is a possible solution to the issue? (ID-NTIA-480)
A. Client-to-site VPN
B. HTTPS management URL
C. Out-of-band management
D. Router ACL
77. The phone company has provided a channelized T1 line. Which of the following should this line be connected to? (ID-NTIA-493)
A. MDF
B. IDF
C. CSU/DSU
D. Switch
78. Which of the following is the best option for controlling and limiting users from accessing resources on the Internet using your companies network? (ID-NTIA-215)
A. Load balancer
B. VPN concentrator
C. IPS
D. Proxy server
E. IDS
79. Which of the following is associated with the technique for prioritizing traffic by tagging packets based on their content? (ID-NTIA-90)
A. SSL
B. QoS
C. IPv6
D. VoIP
E. CARP
80. Which of the following BEST describes the Border Gateway Protocol (BGP) routing protocol? (ID-NTIA-401)
A. Distance vector
B. Static
C. Link state
D. Hybrid
81. Due to the COVID-19 pandemic, the IT department received a shipment of 100 laptops and docking stations. The first action the IT department took is to affix stickers with scannable barcodes to each device. Then the barcode information is linked with specific user biodata. before deploying them to the end-users. This procedure can be best described as ______________. (ID-NTIA-59)
A. asset tracking
B. device hardening
C. tamper detection
D. biometrics
E. hardware security
82. Which of the following is the most secure type of remote administration? (ID-NTIA-295)
A. RDP over SSLv2 HTTPS terminal services gateway
B. HTTP over WPA2-TKIP WiFi
C. SSH over IPsec client-to-site VPN
D. Telnet over PSTN
83. A system administrator receives reports from users of odd behavior in regard to a recently installed server. While reviewing the server network configuration, the system administrator does both a forward and a reverse DNS lookup on the host, along with the network adapter configuration. Which of the following is the problem identified in the output below? (ID-NTIA-374)
A. The reverse DNS entry is pointing to a different host
B. The DNS lookup entry is incorrectly configured
C. There is no reverse DNS entry for this host
D. The server IP address is incorrectly configured
84. Which of the following can a network administrator use to access a network switch using standard AAA configurations? (ID-NTIA-192)
A. Single sign-on
B. TACACS+
C. Local authentication
D. LDAP
85. Which of the following command-line utilities can only run on Unix and Linux systems? (ID-NTIA-20)<
A. ifconfig
B. netstat
C. ping
D. ipconfig
E. tracert
86. Which of the following uses types and codes rather than ports? (ID-NTIA-473)
A. IPv6
B. UDP
C. ICMP
D. EIGRP
Question 86 Explanation:Internet Control Message Protocol (ICMP)
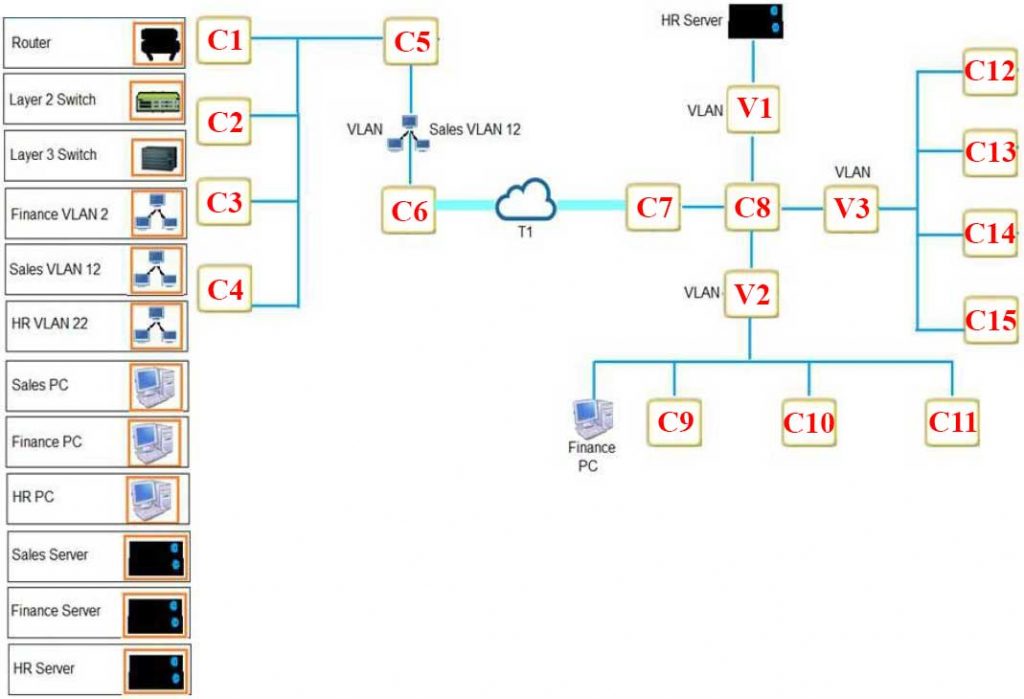
87. You are tasked with creating a network that will accomplish the following requirements for company A. (ID-NTIA-507)
Requirements:
– The remote Sales Team must be able to connect to the corporate network.
– Each department must have ONLY two PCs and a server.
– Eqach department must be segmented from each other.
– The following VLANs have been designed:
— VLAN 2 Finance
— VLAN 12 Sales
— VLAN 22 Human Resources (HR)
– Routing for VLAN 12 is implemented on the router. Routing for VLAN 2 and VLAN 22 is on the switch.
According to the following network diagram for Company A, where would you place the Layer 2 and Layer 3 switches? Click on the image to enlarge.
A. Layer 2 at C8 and Layer 3 at C6
B. Layer 2 at C7 and Layer 3 at C6
C. Layer 2 at C10 and Layer 3 at C12
D. Layer 2 at C5 and Layer 3 at C6
E. Layer 2 at C6 and Layer 3 at C6
88. The security manager reports that individual systems involved in policy or security violations or incidents cannot be located quickly. The security manager notices the hostnames all appear to be randomly generated characters. Which of the following would best assist the security manager in identifying systems involved in security incidents? (ID-NTIA-352)
A. Enforce port security to require system authentication
B. Forward the DHCP logs to the security manager every day
C. Label existing systems with current hostnames
D. Implement a standardized UNC
88 Explanation:Universal Naming Convention (UNC)
89. Users report that they are unable to access the production server with IP address 192.168.30.17. These users need to be provided access without changing any subnet to VLAN information. The VLANs configured on the network are listed below: (ID-NTIA-484)
Department-VLAN#-Subnet used
Marketing-20-192.168.20.0/28
Customer Service-25-192.168.20.64/28
Finance-30-192.168.30.0/28
WHSE-35-192.168.30.16/28
Sales-40-192.168.3.16/28
The users experiencing this issue need to be added to which of the following VLANs?
A. 25
B. 35
C. 30
D. 40
90. In which of the following scenarios should a technician use a cross-over cable to provide connectivity? (ID-NTIA-408)
A. Switch to AP
B. Router to modem
C. Router to switch
D. PC to switch
E. PC to PC
91. A hacker uses a port scanner to penetrate your organization’s IT systems. Vulnerabilities at which layer of the Open Systems Interconnection (OSI) model is used for this exploit? (ID-NTIA-108)
A. Transport
B. Session
C. Application
D. Data Link
E. Network
92. Which of the following can be done to implement network device hardening? Choose all correct answers. (ID-NTIA-128)
A. Enable port mirroring
B. Implement spanning tree
C. Perform VLAN hopping
D. Change default admin password
E. Perform backups
F. Patch and update
93. Which of the following, originally created for the UNIX sendmail program, is now a standard for message logging that enables tools that generate, store, and analyze log information to work together? (ID-NTIA-22)
A. Netstat
B. Syslog
C. Netmon
D. Top
94. A network technician is installing a new SOHO branch office that requires the use of a DOCSIS-compatible modem. The modem needs to be connected to the ISP’s network at the demarc. Which of the following cable types should be used? (ID-NTIA-431)
A. Serial
B. Coaxial
C. UTP
D. Multimode
95. A forensic first responder arrives at the scene where an employee is suspected to have committed a computer-based crime. Which of the following should the first responder do first? (ID-NTIA-359)
A. Document the scene
B. Implement a chain of custody
C. Secure the area
D. Take pictures upon arrival
96. A technician needs to install a new wireless encryption system. They are evaluating the feasibility of implementing WPA. WPA increases protection over WEP by implementing which of the following? (ID-NTIA-495)
A. Shared secret keys
B. Strong RC4 encryption
C. AES encryption
D. MAC filtering
E. Key rotation
97. When connecting two switches together in a LAN, which of the following protocols should you use to increase speed and fault tolerance? (ID-NTIA-141)
A. BGP
B. LLDP
C. SIP
D. LACP
Question 97 Explanation:Link Aggregation Control Protocol (LACP)
98. What topology is used when devices are connected in a LAN via an Ethernet switch? (ID-NTIA-117)
A. Ring or circular
B. Mesh
C. Point-to-point
D. Star
E. Bus
99. Which of the following signal types is carried by copper cable? (ID-NTIA-66)
A. Infrared
B. Microwave
C. Fiber optic
D. Electrical
100. A development team has been testing a web server on a virtual server to create a web application. Once satisfied, the development team clones the entire virtual server into production. The development team needs to use HTTP, HTTPS, and SSH to connect to the new server. Which of the following should the network administrator do to help secure this new production VM? Choose all correct answers. (ID-NTIA-533)
A. Upgrade the firmware on the firewall.
B. Disable the HTTP port in the host firewall.
C. Generate new SSH host keys.
D. Remove unnecessary testing accounts.
E. Issue a new self-signed certificate.
101. A company is expanding and building a new remote branch office. Marketing will need 78 IP addresses, finance will need 150 IP addresses, legal will need 39 IP addresses, and R&D will need 12 IP addresses. The network administrator gives the technician a network of 172.16.48.0/23 and wants the technician to use VLSM for the design. Which of the following are possible solutions? Choose three answers. (ID-NTIA-211)
A. The R&D department should have 172.16.49.207 as a broadcast address.
B. The R&D department should have a last usable IP address of 172.16.49.190.
C. The legal department should have usable IPs ranging from 172.16.49.129 to 172.16.49.190.
D. The finance department should have 172.16.49.127 as a broadcast address.
E. The marketing department should have usable IPs ranging from 172.16.49.129 to 172.16.49.190.
F. The marketing department should receive a /25 network.
G. The legal department should have a first usable IP address of 172.16.49.190.
H. The R&D department should receive a /27 network.
102. A network technician is designing a network cable upgrade in a newly acquired office space. The IT manager wants to install a standardized twisted pair cable solution that supports speeds up to 1 Gbps and terminates with a standard RJ45 connector. Which of the following cable types should the technician suggest? (ID-NTIA-204)
A. RG-6
B. Cat 3
C. SMF
D. Cat 5
E. Cat 6
103. A VoIP system will require 23 concurrent voice channels and one signaling channel. Which of the following types of WAN service would provide the best connectivity to the PSTN? (ID-NTIA-134)
A. BRI
B. E1/E3
C. PRI
D. DSL
Question 103 Explanation:PRI (Primary Rate Interface)
104. Which of the following switch types immediately forwards frames after looking at only the destination address? (ID-NTIA-43)
A. Cut-through
B. Destination switch
C. Store-and-forward
D. Source route
105. Which of the following is not one of the functions provided by TACACS+? (ID-NTIA-76)
A. Authentication
B. Administration
C. Accounting
D. Authorization
Question 105 Explanation:Terminal Access Controller Access Control System Plus (TACACS+)
106. Which of the following storage network technologies has the HIGHEST throughput? (ID-NTIA-275)
A. OC3
B. FCoE
C. InfiniBand
D. iSCSI
Question 107. What is the function of the tool shown in the following figure? (ID-NTIA-505)
Image Credit: https://www.amazon.ca/
A. Used to terminate a cable at a 110 block.
B. Used to verify functionality after a NIC is installed.
C. Used to determine which port a CAT6 cable is connected.
D. Used to correct open short on a cable.
E. Used to verify known good patch cables.
Question 107 Explanation:Network Cable Tester
Question 108. What type of network application would you expect to find the following connector? Click on image to enlarge. (ID-NTIA-443)
A. A network built with Mesh Topology
B. A network built with Logical Topology
C. A network built with Ring Topology
D. A network built with Star Topology
E. A network built with Bus Topology
109. A technician notices clients are receiving a 169.254.x.x IP address following the upgrade of a server. Which of the following ports should the technician check on the local server firewall? (ID-NTIA-371)
A. Ports 80 and 443
B. Ports 56 and 57
C. Ports 20 and 21
D. Ports 67 and 68
E. Port 123 and 8080
Question 109 Explanation:Ports 67 and 68 are used by DHCP and 169.254.x.x IP addresses are APIPAs.
110. When a service fails to start on a Windows server, an entry is typically created in which of the following event logs? (ID-NTIA-65)
A. System
B. Security
C. Setup
D. Application
111. What field in the Transmission Control Protocol (TCP) Option subheader specifies the size of the largest segment a system can receive? (ID-NTIA-101)
A. MSS
B. MMS
C. WinMS
D. Window
112. A network engineer is designing a new network for a remote site. The remote site consists of ten desktop computers, ten VoIP phones, and two network printers. In addition, two of the desktop computers at the remote site will be used by managers who should be on a separate network from the other eight computers. Which of the following represents the BEST configuration for the remote site? (ID-NTIA-334)
A. One router connected to one 24-port switch configured with three VLANS: one for the manager’s computers and printer, one for the other computers and printer, and one for the VoIP phones
B. One router connected to one 12-port switch configured for the manager’s computers, phones, and printer, and one 12-port switch configured for the other computers, VoIP phones, and printer
C. Two routers with each router connected to a 12-port switch, with a firewall connected to the switch connected to the manager’s desktop computers, VoIP phones, and printer
D. One router connected to one 24-port switch configured with two VLANS: one for the manager’s computers, VoIP phones, and printer, and one for the other computers, VoIP phones, and printer
113. In the Open Systems Interconnection (OSI) model, where would the sublayer Media Access Control (MAC) fall under? (ID-NTIA-75)
A. Session
B. Network
C. Transport
D. Presentation
E. Application
F. Physical
G.Data Link
114. A network technician needs to set up an access method for Ann, a manager, to work from home. Ann needs to locally mapped corporate resources such as network drives to perform her job. Which of the following would provide secure access to corporate resources? (ID-NTIA-405)
A. Allow RDP through an external firewall
B. Utilize an SSH connection to the corporate server
C. Connect utilizing client-to-site VPN
D. Use TFTP to transfer files to corporate resources
115. Which of the following is not one of the typical heights for devices mounted in IT equipment racks? (ID-NTIA-13)
A. 4 unit
B. 3 unit
C. 1 unit
D. 2 unit
Question 115 Explanation:Typically rack-mountable network equipments have a height of 1U, 2U or 4U. But you may rarely come across unusual units with odd values (other than 1U) such as 3U or 5Us server cases.
116. Most enterprise servers have dual power supplies. Which of the following mode provides power fault tolerance? (ID-NTIA-53)
A. Individual mode
B. Hot backup mode
C. Combined mode
D. Redundant mode
E. High-efficiency mode
Question 116 Explanation:In combined mode, if one PSU fails or one power circuit fails, the entire system will lose power. Please note that different hardware manufactures may use their own terminology to describe redundant mode (for example backup mode). But the correct technical term is the redundant mode.
117. A network technician notices that most of the nodes in the 10.10.74.0/23 address space return either 1 or 2 node hop after running a tracert, however, some of the new servers are showing a hop count larger than 10. Which of the following is the most likely reason for this? (ID-NTIA-479)
A. New servers are being provisioned in the cloud
B. Some of the servers are configured to use different gateways
C. Part of the subnet is configured to use different VLANs
D. Those servers have host-based firewalls
118. A user believes a work email account has been compromised. A technician discovers that an email seeming to be from the user’s bank shares the same origin IP address as the last login to the email account. Which of the following types of attack is described in this scenario? (ID-NTIA-292)
A. Ransomware
B. Spam
C. Man-in-the-middle>D. Phishing
119. What is the most likely reason that User A cannot communicate with User B based on the following network configuration? (ID-NTIA-376)
User A
IP address: 192.168.1.121
Subnet mask: 255.255.255.0
Default gateway: 192.168.1.1
User B
IP address: 192.168.1.125
Subnet mask: 255.255.248.0
Default gateway: 192.168.1.1
A. The default gateway should have different values
B. There is no problem identifiable by the values given.
C. User B’s IP address is not a loopback address.
D. The subnet values should be the same.
120. An IT technician at a university was told to block all students from accessing the wireless network in the examination building. Which of the following would be the best method to prevent students from accessing the wireless network while in the examination building? (ID-NTIA-208)
A. Use MAC filtering for authorization to the wireless network
B. Require a pre-shared key for authentication to the wireless network
C. Require PEAP for authentication to the wireless network
D. Implement a Faraday cage within the building premises
121. Which of the following Windows applications would you most likely use to create a baseline of system or network performance? (ID-NTIA-38)
A. Syslog
B. Network Monitor
C. ntop
D. Event Viewer
E. Performance Monitor
122. At which of the following Open Systems Interconnection (OSI) model layers would a router operate? (ID-NTIA-418)
A. ession
B. Physical
C. Transport
D. Data link
E. Network
123. Manuja, an administrator, has set up an 802.11n wireless network. Users with 802.11n laptops have reported that speeds are slow. After testing, he determines that users max out at 802.11g speeds. Which of the following would most likely fix this issue? (ID-NTIA-461)
A. Use the 40MHz channels in the 2.4GHz band
B. Enable wireless multimedia (WMM) for QoS
C. Limit the clients to 802.11g compatible laptops
D. Enable access point antenna isolation
124. What performance monitoring tool is shown here (click on figure to enlarge) that enables a system administrator to monitor information about processes that are currently running on a Unix/Linux server? (ID-NTIA-28)
A. cpustat
B. ping
C. netstat
D. top
E. monitor
125. Which of the following RAID levels will not provide fault tolerance? (ID-NTIA-106)
A. RAID 1
B. RAID 0
C. RAID 10
D. RAID 5
126. Which of the following best describes the characteristics of a differential backup solution? (ID-NTIA-282)
A. Backs up files with a date earlier than today’s date with a clear archive bit.
B. Backs up files with the archive bit set but does not clear the bit.
C. Backs up all files and sets the archive bit.
D. Backs up files with the creation or modified date as the current date.
127. Jessica, a network technician, wants to locally back up several router and switch configurations. He wants to store them on a server that can be accessed easily for recovery without authentication. Which of the following servers should Jessica use? (ID-NTIA-391)
A. TFTP
B. Samba
C. LDAP
D. Telnet
128. A network administrator currently collects log files from several different servers. Which of the following would allow the network administrator to collect log files on a centralized host? (ID-NTIA-496)
A. The network administrator should install and configure a network sniffer
B. The network administrator should install and configure a DMZ server
C. The network administrator should install and configure a traffic analysis server
D. The network administrator should install and configure a syslog server
129. A network technician arrives at a remote office and is unable to connect a laptop to corporate resources using the wireless network. After checking the IP address, the network technician notices the assigned IP address does not belong to the corporate network IP scheme. Which of the following has the network technician discovered? (ID-NTIA-277)
B. ARP poisoning
B. Session hijacking
C. Social engineering
D. Evil twin
E. DHCP exhaustion
130. A government agency has hundreds of mobile devices for their field agents. In order to secure their IT assets and data, the agency implemented a system where these mobile devices only operate in specific field locations. If an employee tried to log into a mobile device outside of these specific field locations, the hard drive will self encrypt and the device becomes unusable. This is an example of what type of security measures? (ID-NTIA-93)
A. Tamper detection
B. Social engineering
C. Geofencing
D. Biometric
E. Asset tracking
131. A switch has detected duplicate broadcast messages sourced from a second port. The broadcasts continue to be transmitted and duplicated until the amount of traffic causes severe performance issues. Which of the following should be configured to prevent this behavior? (ID-NTIA-412)
A. ARP protection
B. DHCP snooping
C. Spanning tree
D. BPDU guard
132. Which of the following DSL (Digital Subscriber Line) technology can adjust its transmission speed based on line conditions? (ID-NTIA-166)
A. VDSL
B. RADSL
C. IDSL
D. HDSL
Question 132 Explanation:Rate-Adaptive Digital Subscriber Line (RADSL)
133. When configuring a new switch in a packet-switched network, which of the following helps protect against network loops? (ID-NTIA-503)
A. Flood guard
B. DHCP snooping
C. BPDU guard
D. Spanning tree
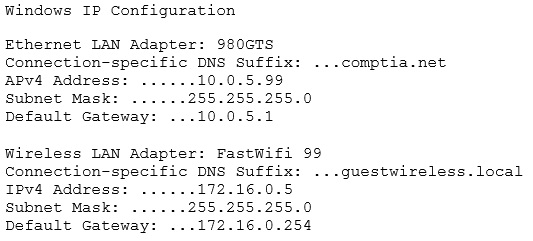
134. An office user cannot access local network drives but has full access to the Internet. A technician troubleshoots the issue and observes the following output of the ipconfig: (ID-NTIA-353)
Which of the following would MOST likely allow the network drives to be accessed?
A. Disable the WLAN adapter
B. Disable the LAN adapter
C. Check the wireless DHCP configuration
D. Update the WLAN adapter driver
135. What is the valid range of numbers for the ephemeral client ports used by the Transmission Control Protocol (TCP) and User Datagram Protocol (UDP)? (ID-NTIA-67)
A. 1024 to 49151
B. 1023 through 65534
C. 1 through 1024
D. 49152 through 65535
Question 135 Explanation:Ephemeral client ports fall in the range of 49152 through 65535 and this range dose not include already registred ports and commonly used standard ports.
136. A technician arrives at a new building to find cabling has been run and terminated, but only the wall ports have been labeled. Which of the following tools should be utilized to best facilitate labeling the patch panel? (ID-NTIA-384)
A. Loopback adapter
B. Multimeter
C. Tone generator
D. Cable tester
137. A network technician is creating a diagram of network termination points in the building. The technician diagrammed the core network room and now needs to diagram the auxiliary network closets. Which of the following is the technician MOST likely going to add to the diagram? (ID-NTIA-198)
A. VRF
B. MDF
C. TDM
D. IDF
Question 137 Explanation:Intermediate Distribution Frame (IDF)
138. Sanuja has been hired by a critical care medical facility (hospital) to build a local area network (LAN) to connect over 150 network devices. The medical facility administrators have advised Sanuja that they have zero tolerance for radio and electromagnetic interference (EMI). Which of the following is the best solution for this facility? (ID-NTIA-86)
A. Enterrpise APs
B. Twisted pair cabling
C. Fiber-optic cabling
D. Coaxial cabling
Question 138 Explanation:Fiber-optic (aka optical fiber) is immune to electromagnetic interference (EMI) and itself does not produce EMI while in operations.
139. A technician needs to limit the amount of broadcast traffic on a network and allow different segments to communicate with each other. Which of the following options would satisfy these requirements? (ID-NTIA-526)
A. Add a layer 3 switch and create a VLAN.
B. Add a firewall and implement proper ACL.
C. Add a bridge between two switches.
D. Add a router and enable OSPF.
140. A customer has submitted a request for a new wireless connection in the main office so visitors can reach the Internet to check their email. The customer is concerned about security and does not want visitors to be able to access the internal finance server. Which of the following BEST describes the correct configuration? (ID-NTIA-301)
A. The LAN and WLAN should be configured in the same zone with dynamic DENY ALL rules.
B. The LAN and WLAN should be configured in the DMZ so traffic is denied automatically.
C. The LAN and WLAN should be marked as trusted during work hours and untrusted during off hours.
D. The LAN and WLAN should be configured in separate zones with a firewall in between.
141. A metric that compares the amount of usable data and the background noise that is being sent over a transmission channel is known as ___________. (ID-NTIA-234)
A. BRI
B. RFI
C. SNR
D. SVC
Question 141 Explanation:Signal-to-noise ratio (SNR)
142. Which of the following DNS record defines a mail exchange server that is associated with a domain name? (ID-NTIA-124)
A. AAAA
B. TXT
C. NS
D. A
E. MX
143. What kind of tool would be used for troubleshooting short/open circuits inside a copper cable? (ID-NTIA-238)
A. Loopback adapter
B. OTDR
C. Spectrum analyzer
D. TDR
Question 143 Explanation:Time-Domain Reflectometer (TDR)
144. Which of the answers listed below refers to a secure replacement for Telnet? (ID-NTIA-226)
A. SSL
C. CHAP
C. SNMP
D. SSH
E. FTP
Question 144 Explanation:SSH (Secure Shell)
145. A network technician has been asked to install an additional switch in an IDF, but all of the single-mode fiber is in use between the IDF and MDF. The technician has deployed new transceivers that allow for the use of a single fiber stand, providing the additional fiber needed for the new switch. Which of the following has the technician deployed? (ID-NTIA-266)
A. Bidirectional SFP
B. Duplex SFP+
C. Duplex GBIC
D. 1000BaseLX SFP
146. Which of the following technologies is used when multiple Ethernet adapters work to increase speed and fault tolerance? (ID-NTIA-382)
A. Redundant circuits
B. Load balancing
C. Clustering
C. Multiple NAT
E. NIC teaming
147. Which of the following is a system of notation that uses base 16 rather than base 10? (ID-NTIA-156)
A. Binary
B. Hex
C. CIDR
D. Octal
148. A technician has been assigned to capture packets on a specific switchport. Which of the following switch feature must be used to accomplish this? (ID-NTIA-323)
A. Spanning tree
B. Trunking
C. Port mirroring
D. Port aggregation
149. When deploying UTP cables in a networking environment, which of the following are acceptable standards? Choose all the correct answers. (ID-NTIA-288)
A. 10Base2
B. 1000BaseLX
C. 10Base5
D. 10GBaseT
E. 1000BaseSX
F. 1000BaseT
150. A network technician does not have access to the GUI of a server and needs to adjust some network properties. Using the following command, what is this the technician attempting to alter? (ID-NTIA-305)
route add 0.0.0.0 mask 0.0.0.0 192.169.1.222 metric 1
A. The technician is clearing the route table.
B. The technician is setting the default gateway.
C. The technician is clearing the subnet mas setting.
D. The technician is adding a static IP address.
151. A technician has replaced a customer’s desktop with a known-good model from storage. However, the replacement desktop will not connect to network resources. The technician suspects the desktop has not been kept up to date with security patches. Which of the following is most likely in place? (ID-NTIA-452)
A. NAC
B. NTP
C. Traffic shaping
D. SDN
E. ACL
Question 151 Explanation:Network Access Control (NAC)
152. A network technician needs to address bandwidth issues on the wireless network. There are currently four 802.11n access points. The technician would like to increase the bandwidth. Which of the following would be the best solution? (ID-NTIA-468)
A. Channel bonding
B. MIMO
C. Increase the signal
D. Disable SSID
153. The ______________ technology can maintain an account database that multiple remote access servers can employ to authenticate remote users. (ID-NTIA-41)
A. IDS
B. NGFW
C. NAS
D. RADIUS
Question 153 Explanation:Remote Authentication Dial-In User Service (RADIUS)
154. A technician discovered a company computer had a virus but was unable to remove it. The technician decided to erase the hard drive to eliminate the threat. Which of the following policies did the technician violate? (ID-NTIA-258)
A. Incident response
B. Asset disposal
C. Acceptable use
D. Data loss prevention
155. A WAP has been dropping off the network sporadically and reconnecting shortly thereafter. The Cat5 wire connecting the access point is a long run of 265ft (81m) and goes through the business area and the mechanical room. Which of the following should the technician do to fix the AP connectivity issue? (ID-NTIA-314)
A. Set the AP to half-duplex to compensate for signal loss
B. Install a repeater to boost the signal to its destination
C. Replace the UTP cable with plenum cable
D. Upgrade the cable from Cat 5 to Cat 5e or Cat 6
Question 155 Explanation:Cat 5 max distance is 100 m (328 ft).
156. A network technician is setting up a WiFi network in an apartment complex for seniors. When trying to determine the best channel, which of the following is the best tool to use? (ID-NTIA-209)
A. Spectrum analyzer
B. Tone generator
C. OTDR
D. Multimeter
E. Protocol analyzer
157. Which of the following will listen on the line to ensure there is no traffic transmitting and implement a back-off timer if a collision occurs? (ID-NTIA-423)
A. MPLS
B. OSPF
C. CSMA/CD
D. CSMA/CA
158. A network protocol that allows for secure file transfer over Secure Shell (SSH) is called _________. (ID-NTIA-227)
A. SFTP
B. Telnet
C. FTPS
D. TFTP
E. SSL
Question 158 Explanation:SSH File Transfer Protocol (SFTP)
159. Which of the following BEST describes the functionality of the root guard feature on a switch? (ID-NTIA-261)
A. Loop protection is enabled on the root port of a switch.
B. BPDUs entering the root bridge are ignored.
C. Broadcast storms entering from a root port are blocked.
D. The STP root bridge cannot be changed.
160. Which of the following physical layer transceiver module standards is the oldest and therefore the most obsolete? (ID-NTIA-55)
A. GBIC
B. QSFP
C. BiDi
D. SFP
Question 160 Explanation:Gigabit Interface Converter (GBIC)
161. IT department suspects that a rogue employee is attempting to access a print server located in an unsecured area on the main office floor. Assuming the print server is a Windows-based system, which of the following event logs can record information about both successful and failed access attempts? (ID-NTIA-62)
A. System
B. Application
C. Security
D. Setup
162. Which of the following storage network technologies provides access to data using block-level storage? (ID-NTIA-120)
A. FTP
B. SAN
C. Jumbo frames
D. Fiber channel
E. NAS
Question 162 Explanation:NAS provides File-Level Access, SAN provides Block Level Access. But in the past, CompTIA Network+ exams had NAS as the answer hence confusing a lot of people.
163. Which of the following must be kept synchronized in order for Kerberos to work? (ID-NTIA-490)
A. Token
B. Certificate
C. Ticket
D. Time
164. The help desk is receiving reports of intermittent connections to a server. A help desk technician suspects the server is unable to establish a three-way handshake due to a DoS attack. Which of the following commands should a network administrator use to confirm the help desk technician’s claim? (ID-NTIA-259)
A. tcpdump
B. nmap
C. arp
D. dig
165. Client PCs are unable to receive addressing information from a newly configured interface on a router. Which of the following should be added to allow the clients to connect? (ID-NTIA-338)
A. IP helper
B. DHCP lease time
C. DNS record type
D. TTL
E. Ping table
166. Which Windows tool uses ICMP messages and manipulates IPv4 time-to-live values to illustrate the route packets take through an internetwork? (ID-NTIA-77)
A. Nslookup
B. Ping
C. Tracert
D. Netstat
E. Route
167. After deployment of a second network link to load balance the network traffic, the quality of voice calls degrades. The network administrator discovers the voice packets are arriving at uneven intervals that cannot be handled by the voice application buffer. Which of the following actions will improve the quality of the voice calls? (ID-NTIA-193)
A. Control the latency of traffic across the network links
B. Control the jitter of the affected traffic across the network links
C. Control the EMI of the multimedia traffic across the network links
D. Control the attenuation of the non-voice traffic across the network links
168. A company has decided to allow certain users to work remotely by opening up a VPN connection through the firewall. The security policy has been updated to allow VPN connections only from certain users and to specific areas on the network. Along with configuring the correct policies on the firewall, which of the following also needs to be configured on users’ mobile devices to allow these VPN connections? (ID-NTIA-248)
A. VNC application
B. Geotagging application
C. Kerberos
D. Credentials
169. A technician is setting up VoIP phones on a wireless network. Users report that calls are choppy and sometimes dropped. The technician has measured two characteristics using simple command-line tools that verify the problem. Which of the following characteristics did the technician measure? Choose all correct asnwers. (ID-NTIA-425)
A. Reflection
B. Packet loss
C. Attenuation
D. Interference
E. Signal-to-noise ratio
F. Latency
170.While testing an ACL on the default gateway router to allow only web browsing, ports TCP 80 and TCP 443 were the only ports open. When tested, no websites were accessible via their URLs inside the network. Which of the following configurations should be added to the ACL? (ID-NTIA-388)
A. permit tcp any any eq 8080
B. permit tcp any any eq 20
C. permit udp any any eq 25
D. permit tcp any any eq 110
E. permit udp any any eq 53
F. permit udp any any eq 68
171. A network technician receives a trouble ticket and speaks to the user who is experiencing the issues with the application. Which of the following should the technician perform next? (ID-NTIA-241)
A. Gather information
B. Establish a plan of action
C. Document the findings
D. Determine the symptoms
172. In order to hide the internal IP addresses (LAN) of devices across WAN, which of the following should you configure? (ID-NTIA-158)
A. NAT
B. QoS
C. RIP
D. DMZ
E. DDoS
173. Which of the following commands did a network technician run, if the network technician receives the following command output from a Linux-based machine? (ID-NTIA-196)
SANUJA.COM 430 IN mx mx1.SANUJA.COM
SANUJA.COM 5 IN mx mx2.SANUJA.COM
SANUJA.COM 430 IN mx mx10.SANUJA.COM
SANUJA.COM 521 IN NS ns1.SANUJA.COM
SANUJA.COM 521 IN NS ns2.SANUJA.COM
SANUJA.COM 521 IN NS ns3.SANUJA.COM
SANUJA.COM 521 IN NS ns4.SANUJA.COM
A. dig –t ANY SANUJA.COM
B. NMAP –t SANUJA.COM
C. netstat –a SANUJA.COM
D. iptables –f SANUJA.COM
174. Which of the following protocol is used by web browsers to communicate with web servers? (ID-NTIA-56)
A. HTTP
B. FTP
C. SMTP
D. SSL
E. HTML
175. A network engineer is working on a network connectivity problem between a site in Calgary and a site in New York. The connection went down overnight, and the engineer is unsure where the connection failed. The technician is logged into the primary switch in the customer’s network, which is also the company’s connection to the WAN. Which of the following tools should the technician use to determine the last available network hop? (ID-NTIA-247)
A. traceroute
B. pathping
C. Nmap
D. netstat
176. At which of the following layers of the OSI model does compression occur? (ID-NTIA-273)
A. Transport
B. Presentation
C. Session
D. Data link
177. Which of the following allows a central point to simultaneously address other points without addressing all of them? (ID-NTIA-486)
A. Subnetting
B. Broadcast
C. Unicast
D. Multicast
178. Based on networks 10.8.16.0/22 and 10.8.31.0/21, which of the following is the BEST summarized CIDR notation? (ID-NTIA-337)
A. 10.8.0.0/20
B. 10.8.0.0/19
C. 10.8.0.0/16
D. 10.0.0.0/24
Question 178 Explanation: Classless Inter-Domain Routing (CIDR)
179. A network printer error report indicates that it may have an expired IP address. A failure with which of the following will cause this issue? (ID-NTIA-232)
A. ICMP
B. DHCP
C. DNS
D. LADP
E. HTTP
Question 179 Explanation:Dynamic Host Configuration Protocol (DHCP)
180. You are an IT consultant for a small business where maintaining physical security is difficult. Implementing which of the following standards would best help to prevent unauthorized connections to the wired network? (ID-NTIA-214)
A. 802.1q
B. 802.1X
C. 802.3at
D. 802.3af
E. 802.11ac
181. A technician is configuring a printer for a client. The technician connects the printer to the network, but is unsure how to determine its switchport. Which of the following should the technician do FIRST to locate the switchport? (ID-NTIA-126)
A. Perform a DNS lookup on the server.
B. Reference the ARP table in the router.
C. Set up an SSH session to the desktop.
D. Configure port security on the switch.
182. Which of the following explains why splitting a large switched Ethernet LAN into two LANs by adding a router can help to alleviate traffic congestion and improve performance? Choose all correct answers. (ID-NTIA-326)
A. Adding a router diverts traffic to an alternate path through the network.
B. Adding a router prevents computers on one LAN from communicating with computers on another LAN.
C. Adding a router reduces the amount of unicast traffic on each of the two LANs.
D. Adding a router reduces the amount of broadcast traffic on each of the two LANs.
183. This device enables administrators of enterprise wireless networks to manage multiple access points from a central location. (ID-NTIA-12)
A. Network firewall
B. Demarcation point
C. Demarcation point
D. Wireless controller
E. Wireless endpoint
184. A second router was installed on a network to be used as a backup for the primary router that works as a gateway. The infrastructure team does not want to change the IP address of the gateway on the devices. Which of the following network components should be used in this scenario? (ID-NTIA-450)
A. Reserved IP
B. Loopback IP
C. Public IP
D. Virtual IP
185. Which of the following Windows commands enables you to delete the entire ARP cache? (ID-NTIA-83)
A. arp -s
B. arp -a
C. arp -c *
D. arp -d *
Question 185 Explanation:Note, arp -d command is for deleting cache entries, and by running it with the asterisk wildcard, the command deletes all of the entries in the cache.
186. A company runs Linux servers in its own datacenter and also on a popular public cloud service provider. The servers hosted by the cloud provider can only be accessed with proper authorization and are only accessed by the company’s datacenter. Which of the following BEST describes the type of cloud architecture being used? Choose all correct answers. (ID-NTIA-200)
A. IaaS
B. SaaS
C. PaaS
D. Private
E. Public
F. Hybrid
187. A network technician is configuring user access to a VPN concentrator and has been advised to use a protocol that supports encryption over UDP. Which of the following protocols has the technician most likely configured for client use? (ID-NTIA-410)
A. DNS
B. SNMP
C. TFTP
D. DTLS
Question 187 Explanation: Datagram Transport Layer Security (DTLS)
188. A network technician wants to remotely and securely access the desktop of a Linux workstation. The desktop is running remote control software without encryption. Which of the following should the technician use to secure the connection? (ID-NTIA-343)
A. SFTP
B. SSH in tunnel mode
C. EAP-PEAP
D. RDP set to console connection
189. You are the IT Manager at a 150 employee small business located in downtown Vancouver. The accounting department filed a ticket claiming that they lost access to the accounting network drive. You strongly suspect an update on the firewall firmware may have changed a configuration leading to loss of access. Which documentation most likely contains the firewall configurations and access control lists information? (ID-NTIA-51)
A. Asset management files
C. MSConfig file
C. Logical network diagram
D. Wiring schematic
E. Physical network diagram
190. In a small office environment, one computer is set up to provide Internet access to three other computers that are not interconnected. This is an example of which of the following topology types? (ID-NTIA-485)
A. Point-to-point
B. Hybrid
C. Point-to-multipoint
D. Peer-to-peer
191. Which of the following types of interference on a twisted pair network are designed to be prevented by the twists in the wire pairs inside the cable? (ID-NTIA-100)
A. Crosstalk
B. EMI
C. Signal attenuation
D. Latency
192. You were advised to replace a failed network switch in a datacenter. Which of the following would you use to determine the precise location of the device? (ID-NTIA-107)
A. Network map
B. Rack diagram
C. Building blueprints
D. Logical diagram
E. Wiring schematic
193. A company hires another firm to test the integrity of its information security controls. This is an example of: (ID-NTIA-257)
A. role separation.
B. risk assessment.
C. device hardening.
D. penetration testing.
194. Which of the following is a disadvantage of migrating data to a SaaS cloud service? (ID-NTIA-143)
A. Loss of full control over data resources
B. Increased malware exposure
C. Decreased performance of the internal network
D. Inconsistent data accessability
E. Incompatibility with the current network
195. A customer is reporting difficulty connecting some devices after replacing a wireless router with a new wireless 802.11 ac router. The SSID, encryption, and password are the same as the previous router. A technician goes on-site and notices the devices that are no longer connecting appear to be several years old. Which of the following is most likely the problem? (ID-NTIA-152)
A. There is a security type mismatch.
B. There is a frequency mismatch
C. There is insufficient antenna power
D. The channel has changed
E. The password needs to be re-entered
196. Installing an electrical generator to a datacenter is an example of which of the following fault tolerance concepts? (ID-NTIA-54)
A. Uninterruptible Power Supply (UPS)
B. Power redundancy
C. Power looping
D. Dual power supplies
E. Redundant circuits
Question 196 Explanation:You may have thought Uninterruptible Power Supply (UPS). A UPS is a device that uses battery power, not a generator and it is not meant to supply power for a long period of time. A well-planned data center should have, power generators, UPS devices and power conditioning units.
197. MAC filtering is an access control method used by which of the following types of hardware devices? (ID-NTIA-25)
A. Biometric systems
B. Domain controller
C. Wireless access point
D. RADIUS server
E. Smartcards
198. After a server outage, a technician discovers that a physically damaged fiber cable appears to be the problem. After replacing the cable, the server will still not connect to the network. Upon inspecting the cable at the server end, the technician discovers light can be seen through one of the two fiber strands. Which of the following should the technician do first to reconnect the server to the network? (ID-NTIA-344)
A. Replace the server’s single-mode fiber cable with multimode fiber
B. Reverse the fiber strands of the cable and reconnect them to the server
C. Move the fiber cable to a different port on the switch where both strands function
D. Use a TDR to test both strands of a new replacement cable prior to connecting it to the server
199. A home user is unable to get to the Internet from a workstation that is connected to a wireless network. When reviewing the results of the ipconfig command, the user wants to verify the default gateway is correct. Which of the following devices should be the gateway? (ID-NTIA-398)
A. Layer 2 switch
B. Cable modem
C. SOHO router
D. DNS server
200. Employees want the ability to use personal devices on the guest network while working out at the company gym. In order to meet the request, which of the following policies requires employee adherence? (ID-NTIA-373)
A. NDA
B. MOU
C. AUP
D. SLA
Question 200 Explanation:Acceptable Use Policy (AUP)
201. Which of the following best describes geofencing? (ID-NTIA-113)
A. Somewhere you are
B. Something you know
C. Something you have
D. Something you do
202. Which of the following STP states indicates an inactivated port due to a loop? (ID-NTIA-502)
A. Learning
B. Forwarding
C. Disabled
D. Blocking
203. Which of the following is the SHORTEST way to write 2001:0000:0d58:0000:0000:0095:7565:0001 in proper IPv6 shorthand? (ID-NTIA-331)
A. 2001:0:d58::95:7565:1
B. 2001::d58::95:7565:1
C. 2001:0:0d58::95:7565:1
D. 2001:0:d58:0:0:95:7565:1
204. In a service provider network, a company has an existing IP address scheme. Company A’s network currently uses the following scheme: (ID-NTIA-333)
Subnet 1: 192.168.1.0/26
Subnet 2: 192.168.1.65/26
Company B uses the following scheme:
Subnet 1: 192.168.1.50/28
The network administrator cannot force the customer to update its IP scheme. Considering this, which of the following is the BEST way for the company to connect these networks?
A. PAT
B. VLAN
C. DMZ
D. NAT
205. A technician is utilizing SNMPv3 to monitor network statistics. Which of the following actions would occur immediately of a server’s utilization spikes above the prescribed value? (ID-NTIA-407)
A. A response message is sent from the agent to the manager
B. The SET function pushes an alert to the MIB database
C. The object identifier is modified and reported during the next monitoring cycle
D. A trap message is sent via UDP to the monitoring workstation
206. A wireless access point that was working in a large warehouse last week is now offline. The technician observes there is no power to the device. The technician verifies PoE is working on the switchport, and then confirms the wireless access point is still not powering up. Which of the following is the MOST likely issue? (ID-NTIA-294)
A. Attenuation
B. Damaged cable
C. Incorrect pin-out
D. Switch configuration
207. Sanuja, a user, is having issues when trying to access certain web pages. Upon navigating to a web page, it seems like it connects, but then presents the following message: (ID-NTIA-245)
“The Security certificate presented by this website was not trusted by trusted certificate authority.”
Sanuja has cleared his cache and cookies, rebooted his machine, and attempted to browse to the website from a coworker’s desktop, but it still presented with this error. Which of the following is the MOST likely cause of this error?
A. The website is missing an HTTPS certificate.
B. The SSL certificate has expired.
C. The web server is missing an intermediate certificate.
D. TLS is not enabled in the browser.
208. Which of the following should be configured to allow for IP-to-name resolutions? (ID-NTIA-396)
A. PTR
B. A
C. MX
D. NS
E. CNAME
209. Which of the following could be used to stop unknown threats? (ID-NTIA-471)
A. DMZ
B. Signature-based IPS
C. WPA2
D. Behavior-based IPS
E. Honeypots
210. A technician wants to prevent an unauthorized host from connecting to the network via Ethernet. Which of the following is a Layer 2 access control the technician should implement? (ID-NTIA-148)
A. Access control lists
B. Captive portal
C. WPA2
D. Port security
211. An employee wishes to use a personal cell phone for work-related purposes, including storage of sensitive company data, during long business trips. Which of the following is needed to protect BOTH the employee and the company? (ID-NTIA-145)
A. An AUP covering how a personal phone may be used for work matters
B. A consent to monitoring policy covering company audits of the personal phone
C. An NDA ensuring work data stored on the personal phone remains confidential
D. Real-time remote monitoring of the phone’s activity and usage
212. A network technician works in a large environment with several thousand users. Due to the needs of the organization, the network manager has asked the technician to design a solution that accommodates the data needs of all the users, while keeping all data on-site. Which of the following solutions should the technician implement? (ID-NTIA-254)
A. IaaS
B. SaaS
D. NAS
D. SAN
213. To keep the costs down, a small business allows its employees to use their own personal laptop computers to access their network infrastructure. This type of polity is typically known as __________. (ID-NTIA-140)
A. IRP
B. NDA
C. BYOD
D. SLA
Question 213 Explanation:Bring Your Own Device (BYOD)
214. Which of the following is a correct term describing the function of a switch? (ID-NTIA-34)
A. Ethernet hub
B. Multiport bridge
C. Layer 2 router
D. Layer 3 repeater
215. Which of the following BEST describes how a layer 2 switch functions? (ID-NTIA-510)
A. Switches packets between different subnets based on MAC addresses
B. Switches packets within the same subnet based on MAC addresses
C. Switches packets between same subnets based on IP addresses
D. Switches packets between different subnets based on IP addresses
216. Two buildings used to be connected by a wireless bridge, but they are upgrading to fiber. Which of the following new devices would be required at the demarcation points? (ID-NTIA-212)
A. Media converter
B. Wireless access point
C. Network switch
D. Firewall
E. Router
217. In a standard Cisco network diagram, what component does the following symbol represent? (ID-NTIA-02)
A. A hub
B. A switch
C. A router
D. A gateway
218. Which of the following WAN technologies utilizes the concept of virtual circuits and point-multipoint connections? (ID-NTIA-365)
A. Frame relay
B. PRI
C. ISDN
D. Broadband cable
E. MPLS
219. You have been called in to inspect a network configuration. You are given only one network diagram, shown in the following figure (click to enlarge). Using the diagram, what recommendation might you make? (ID-NTIA-377)
A. None, the network looks good.
B. Cable 1 does not need to be plenum rated.
C. Cable 2 should be an STP cable.
D. Cable 3 should be an STP cable.
Question 219 Explanation:In this diagram, Cable i is plenum rated and should be fine. Cable 3 is a path cable and does not need to be STP rated. However, Cable 2 goes through walls and ceilings. Therefore, it should be recommended to have a better grade of cable than regular UTP. STP provides greater resistance to EMI.
220. A firewall administrator is implementing a rule that directs HTTP traffic to an internal server listening on a non-standard socket. Which of the following types of rules is the administrator implementing? (ID-NTIA-177)
A. NAT
B. ARP
C. PAT
D. SNAT
E. STP
Question 220 Explanation:Port Address Translation (PAT)
221. Which of the following terms describes the process by which a client user or computer requests that it be issued a certificate, either manually or automatically? (ID-NTIA-95)
A. Authentication
B. Enrollment
C. Encryption
D. Authorization
E. Certification
222. Which of the following should be performed to verify that unnecessary services are disabled on all switches in an environment? (ID-NTIA-518)
A. Baseline review
B. Log scanning
C. Port scanning
D. Packet capturing
223. Which of the following defines when Dhillon, an attacker, attempts to monitor wireless traffic in order to perform malicious activities? (ID-NTIA-150)
A. Wardriving
B. Packet sniffing
C. SQL injection
D. XSS
E. Directory traversal
224. Which of the following attack methods is associated with unprotected Wi-Fi network systems? (ID-NTIA-92)
A. Wardriving
B. Evil twin
C. Social engineering
D. Logic bomb
Question 224 Explanation:Wardriving is an attack method that consists of driving around a neighborhood with a computer scanning for unprotected wireless networks.
225. Which of the following is the physical location where the customer-premise equipment comes together with the ISP or third-party telecommunications equipment? (ID-NTIA-287)
A. Server room
B. Intermediate distribution frame
C. Equipment closet
D. Demarcation point
226. Which of the following protocols does the ping program never use to carry its messages? (ID-NTIA-98)
A. TCP
B. UDP
C. IP
D. Ethernet
E. ICMP
227. A network administrator is configuring the 172.16.40.0/22 network for a new building. Which of the following is the number of hosts that will be supported on this network? (ID-NTIA-274)
A. 1022
B. 512
C. 2046
D. 510
E. 2048
F. 1024
228. A company has just installed a new cloud VoIP solution, however, users occasionally report poor call quality or dead air being present. Which of the following describes the next troubleshooting step the technician should take? (ID-NTIA-394)
A. The technician should check the internal diagnostics on all the phones to look for a common thread
B. The technician should use a packet tracer to see if the traffic is getting out of the network
C. The technician should reset all the phones and deprovision information from the provider
D. The technician should run ping tests on the Internet line to monitor for packet loss and latency
229. A network technician needs to separate a web server listening on port 80 from the internal LAN and secure the server from the public Internet. The web server should be accessible to the public Internet over port 80 but not the private LAN. Currently, the network is segmented with a network-based firewall using the following IP addressing scheme on each interface: (ID-NTIA-350)
Which of the following ones should the technician use to place the webserver and which of the following firewall rules should the technician configure?
A. Place the web server in the DMZ with an inbound rule from eth0 interface to eth1 to accept traffic over port 80 designated to the webserver
B. Place the web server in the DMZ with an inbound rule from eth1 interface to eth0 to accept traffic over port 80 designated to the webserver
C. Place the web server in the private zone with an inbound rule from eth2 interface to eth1 to accept traffic over port 80 designated to the webserver
D. Place the web server in the public zone with an inbound rule from eth0 interface to accept traffic over port 80 designated to the webserver
230. A disgruntled employee decides to leak critical information about a company’s new product. The employee places keyloggers on the department’s computers, allowing the information to be sent out to the Internet. Which of the following attacks is occurring? (ID-NTIA-521)
A. Man-in-the-middle
B. Social engineering
C. Insider threat
D. Logic bomb
231. Which of the following Transmission Control Protocol (TCP) control bits is set to 1 to initiate the termination of a session? (ID-NTIA-04)
A. FIN
B. PSH
C. SYN
D. URG
E. END
232. A small company is requesting a quote to refresh its wireless network. The company currently runs 60 autonomous APs and has plans to increase wireless density by 50% in the near future. The requirements state that the chosen solution should significantly decrease the management overhead of the current wireless network. Which of the following should the vendors recommend in response to the quote request? (ID-NTIA-243)
A. The use of lightweight APs with a load balancer
B. The use of autonomous APs with a load balancer
C. The use of lightweight APs with a wireless controller
D. The use of autonomous APs with a wireless controller
233. Which of the following protocol standards defines a layered implementation that does not correspond to the layers of the Open Systems Interconnection (OSI) model? (ID-NTIA-317)
A. PPP
B. RDMA
C. iSCSI
D. Fibre Channel
234. Which of the following allow for higher fault tolerance, availability, and performance across multiple systems? Choose all the correct answers. (ID-NTIA-280)
A. TCP offloading
B. Load balancer
C. Round robin
D. Clustering
D. Jumbo frames
235. An administrator has received a recommendation against deploying WEP as a wireless encryption protection scheme. Which of the following is MOST likely the reason? (ID-NTIA-527)
A. WEP uses plain text
B. WEP uses RC4 which is easily accessible and not secure
C. WEP is not well supported
D. WEP’s IV is too small
236. A technician wants to configure a SOHO network to use a specific public DNS server. Which of the following network components should the technician configure to point all clients on a network to a new DNS server? (ID-NTIA-313)
A. Proxy server
B. Switch
C. Load balancer
D. Router
237. Which of the following type of technique is used to block access to websites and web-based advertisements by providing a false result of a requested domain name? (ID-NTIA-202)
A. DDoS
B. IDS firewall
C. DNS sinkhole
D. MITM
238. A company has procured a new office building and started the process of assigning employees to work at that location. The company has also purchased equipment for the new location. There are 5033 laptops, 6000 monitors, and 857 printers. Which of the following steps is the technician most likely to complete first? (ID-NTIA-310)
A. Create a port location diagram
B. Create an inventory database
C. Create a network baseline
D. Create a rack diagram
239. Your company is moving to a new building. After the site survey, you decided to install 25 wireless access points (AP) in drop ceilings across four floors. Which of the following would be the most efficient method for powering 25 APs? (ID-NTIA-187)
A. Ethernet-over-power adapter
B. Powerline extender
C. Ethernet power controller
D. Power-over-Ethernet switch
E. Power distribution unit
240. A network admin can ping remote host by its IP address, but not by FQDN. Which of the following is the most probable source of the problem? (ID-NTIA-233)
A. NetBIOS
B. HTTP
C. DHCP
D. DNS
E. ICMP
241. The IEEE 802.11g standard is backwards compatible with which of the following? (ID-NTIA-236)
A. 802.11n
B. 802.11a
C. 802.11b
D. 802.11ac
242. A network administrator wants to reduce the amount of time each user takes to log in to different systems in the network. Which of the following would reduce the time spent authenticating? (ID-NTIA-278)
A. MFA
B. Kerberos
C. Certificate
D. RADIUS
E. SSO
F. NAC
Question 242 Explanation:Single sign-on (SSO)
243. Which of the following values could a web client use as an ephemeral port number when communicating with a web server? (ID-NTIA-26)
A. 23
B. 50134
C. 995
D. 1024
E. 1999
F. 80
Question 243 Explanation:The allowed ephemeral port number values range from 49152 to 65535.
244. A department is reporting network issues. Users can ping each other and the switch, but not the default gateway. When looking at a wiring diagram and a physical blueprint, a technician notices the 1000BaseLX SFP connects to a distribution switch via a cable that runs behind a large industrial refrigerator. The technician also notices both switches have been worked on recently. Which of the following is most likely the issue? (ID-NTIA-269)
A. Open/short
B. EMI
C. Attenuation
D. TX/RX reverse
245. A technician is planning a remote-access strategy to manage routers and switches on a dedicated management network. The management network is segregated from the production network and uses site-to-site VPN connections. Some of the equipment does not support encryption. Which of the following should the technician choose that all the equipment would support? (ID-NTIA-173)
A. IPSec
B. SSH
C. Telnet
D. SSL
246. In a public key infrastructure (PKI), which half of a cryptographic key pair is never transmitted over the network? (ID-NTIA-16)
A. The public key
B. The secure key
C. The ticket granting key
D. The session key
E. The private key
247. Which of the following must be installed on an employee’s computer if the remote access VPN implements an SSL VPN with PKI authentication? (ID-NTIA-483)
A. Soft spoken
B. Shared secret
C. Private certificate
D. HTTPS server
248. A junior network technician receives a help desk ticket from an end-user who is having trouble accessing a web application that was working the previous day. After talking with the end-user and gathering information about the issue, which of the following would be the most likely course of action for the technician to perform next? (ID-NTIA-378)
A. Document the findings and outcomes
B. Do nothing
C. Establish a theory of probable cause
D. Implement the solution
E. Escalate the ticket to a senior technician
249. A technician is investigating the cause of a network outage. Which of the following documents should be checked to rule out configuration issues? (ID-NTIA-520)
A. Change management records
B. Inventory management
C. Logical diagrams
D. Network log files
250. A zero-day vulnerability is discovered that affects a specific network device. This vulnerability only affects services on port 21. This network device is restricted to use only secure protocols and services. Which of the following explains why this device is secure? (ID-NTIA-290)
A. Because FTP is not a secure service
B. Because a secure firewall will protect the device
C. Because secure protocols would reject malicious packets
D. Because SCP is not a secure service
251. A network administrator is redesigning network security after an attack. During the attack, an attacker used open cubicle locations to attach devices to the network. The administrator wants to be able to monitor future attacks in a safe environment and determine the method of attack. Which of the following should the administrator do to best meet this requirement? (ID-NTIA-428)
A. Install a BPDU guard on switchports and enable STP
B. Install antivirus software and set an ACL on the servers
C. Create a VLAN for the unused ports and create a honeyspot on the VLAN
D. Create a DMZ for public servers and secure a segment for the internal network
252. A network engineer for a manufacturing company is implementing a wireless network that provides reliable coverage throughout the facility. There are several large, electric, motorized machines installed on the shop floor for automating the manufacturing process. These machines are known to be significant sources of RF interference. Which of the following frequencies should the wireless network use to minimize this interference? (ID-NTIA-311)
A. 5GHz
B. 56MHz
C. 900MHz
D. 2.4 GHz
253. Which of the following is a proprietary routing protocol? (ID-NTIA-514)
A. OSPF
B. BGP
C. EIGRP
D. RIP
Question 253 Explanation:Enhanced Interior Gateway Routing Protocol (EIGRP) is a proprietary protocol developed by Cisco Systems.
254. Which of the Open Systems Interconnection (OSI) model layers is responsible for syntax translation and compression or encryption? (ID-NTIA-24)
A. Physical
B. Data link
C. Application
D. Presentation
E. Network
F. Session
G. Transport
255. A company is experiencing exponential growth and has hired many new employees. New users are reporting they cannot log into their systems, even though they are on the same network. The technician can see physical connectivity to the network switch along with their MAC addresses. Which of the following should the technician check next? (ID-NTIA-304)
A. DHCP scope availability
B. Server-based firewall configuration issue
C. Patch cable type
D. VLAN routing
256. Homer Simpson, a technician, suspects a duplicate IP address assignment on the network. Which of the following resources can be used to verify this problem? (ID-NTIA-455)
A. Syslog
B. Network map
C. Placement map
D. Environmental monitor
257. A network technician is reviewing switch ACLs to determine if they are causing communication issues with one PC. The PCs IP address is 192.168.12.66. Which of the following is the network range found in the ACL that could have affected this PC? (ID-NTIA-381)
A. 192.168.12.97 to 255.255.255.240
B. 192.168.12.97 to 255.255.255.224
C. 192.168.12.97 to 255.255.255.248
D. 192.168.12.97 to 255.255.255.192
258. Which of the following technologies should be used in high-throughput network to reduce network overhead? (ID-NTIA-299)
A. Port aggregation
B. Jumbo frames
C. iSCSI
D. QoS tags
259. No link lights on a switch’s SFP are functioning, so the network technician re-terminates the end. After testing the cable, the tester is showing a db loss of-9. Which of the following types of cable is most likely being tested? (ID-NTIA-528)
A. CAT5e
B. CAT3
C. CAT6a
D. Fiber
260. A network administrator would like to collect information from several networking devices using SNMP. Which of the following SNMP options should a network administrator use to ensure the data transferred is confidential? (ID-NTIA-351)
A. MD5
B. authpriv
C. SHA
D. Authentication passphrase
261. A technician is observing brownout issues at a smaller office. At least once a week, the edge switch power cycles. Which of the following should the technician do to resolve the issue? (ID-NTIA-419)
A. Install a UPS
B. Install a new electrical circuit
C. Replace the switch uplink cable
D. Install a power conditioner
E. Install a new switch
Question 261 Explanation:A power conditioner is also an option. However, installing a UPS is the better choice.
262. NTP is used for which of the following function? (ID-NTIA-240)
A. Retrieving contents of an Internet page from a web server
B. Allocation of IP addresses
C. Monitoring of network-attached devices
D. Synchronization of clocks over a computer network
Question 262 Explanation:Network Time Protocol (NTP)
263. A network administrator has deployed a secure wireless network that authenticates using Active Directory network credentials so individual users are uniquely identified when connected to the WLAN. Which of the following wireless technologies has the administrator configured? (ID-NTIA-181)
A. CCMP-AES
B. WEP
C. PSK
D. EAP-PEAP
264. Which of the following topologies offers the highest level of redundancy? (ID-NTIA-445)
A. Hub and spoke
B. Partial mesh
C. Ring
D. Full mesh
E. Bus
Question 264 Explanation:The full-mesh topology might be complex and expensive to implement, but it does provide excellent levels of redundancy. Should one or more links fail, it is often possible to reroute traffic around the failures.
265. Before upgrading the firmware on several routers, a technician must verify the firmware file received is the same one the vendor provided. Which of the following should the technician use? (ID-NTIA-296)
A. Digital signatures
B. 3DES encryption
C. Digital signatures
D. SSL certificate
266. When enabling jumbo frames on a network device, which of the following parameters is being adjusted? (ID-NTIA-339)
A. MTU
B. Duplex
C. Speed
D. TTL
267. A network technician performs a wireless site survey at a company building and identifies that the cafeteria is not covered by a wireless signal. The cafeteria is located in a medium-size, square-shaped room. Which of the following types of WAP antenna should the technician install in the center of the cafeteria to provide the BEST coverage? (ID-NTIA-417)
A. Parabolic
B. Unidirectional
C. Omnidirectional
D. Yagi
268. A typical nexus termination point for incoming telephone and wide area network (WAN) services is known as __________. (ID-NTIA-103)
A. IDF
B. PBX
C. RDP
D. MDF
E. MTBF
Question 268 Explanation:Main Distribution Frame (MDF)
269. An administrator would like to search for network vulnerabilities on servers, routers, and embedded appliances. Which of the following tools would most likely accomplish this? (ID-NTIA-494)
A. Ping
B. Baseline analyzer
C. Protocol analyzer
D. Nessus
270. Which of the following types of cable, when installed, sometimes employed a device called a vampire tap? (ID-NTIA-11)
A. Shielded twisted pair
B. Multimode fiber optic
C. Coaxial
D. Single-mode fiber optic
E. Unshielded twisted pair
271. A technician notices that network access is becoming increasingly slow. All of the activity lights, on the only network layer 2 switch, are blinking at steadily increasing rates. Which of the following is the most likely cause of the increased traffic? (ID-NTIA-456)
A. STP blocking
B. IP addresses
C. Switching loop
D. MTU mismatch
272. A technician has been asked to diagnose problems with DHCP addressing on a VLAN. The DHCP server responds to pings from the technician’s machine. Which of the following should the technician use to help diagnose the problem? (ID-NTIA-281)
A. netstat
B. nslookup
C. Packet sniffer
D. Spectrum analyzer
273. Sanuja installed six Windows computers in his home network connected to a switch and a cable modem/router that provides access to the Internet. One of the computers is able to connect to other computers and internal NAS but cannot connect to the Internet. Which of the following parameters on the malfunctioning computer will Sanuja most likely have to change to resolve this problem? (ID-NTIA-171)
A. Subnet mask
B. IP address
C. MAC address
D. Default gateway
Question 273 Explanation:Subnet mask should be correct since the computer can communicate with the NAS and the other computers in the LAN.
274. A home security company has installed a wireless device at a residence that allows the company to view security status of the home online. The resident reports the 802.11ac home wireless intermittently loses connectivity for about 15 minutes twice a day. Which of the following is the most likely cause? (ID-NTIA-213)
A. An IoT device is causing a DoS attack on the wireless network
B. The utility company throttles power during peak hours
C. There is additional data being transferred over the wireless network
D. There is interference with the smart reader
275. What is the name of the tool shown in the following figure? (ID-NTIA-319)
Image Credits: https://www.homedepot.com/p/ Ideal-Punchdown-Tool- with-110-and-66- Blades-35-485/ 203761571
A. Butt set
B. Tone generator and locator
C. Punchdown tool
D. Crimper
276. Which of the following is networking stand-alone hardware that will permit any WiFi-compliant device to connect to a wired network? (ID-NTIA-437)
A. Wireless access point
B. Wireless bridge
C. Wireless hub
D. Wireless firewall
277. A network technician notices that switches of the same model have different commands and security features while administering them. Which of the following hardening techniques should the technician perform on a regular schedule to ensure all switches have the same features and security functionality? (ID-NTIA-182)
A. Disable unused switchports
B. Change the default credentials
C. Apply patches and updates
D. Verify the firmware file hash
278. A client on a TCP/IP network is attempting to establish a session with a server. Which of the following correctly lists the order of Transmission Control Protocol (TCP) session establishment messages? (ID-NTIA-06)
A. SYN, SYN/ACK, ACK
B. SYN, SYN, ACK, ACK
C. SYN/ACK, SYN/ACK
D. SYN, ACK, SYN, ACK
Question 278 Explanation:Remember the three-way handshake.
279. Allowing data to be centrally stored and accessed by multiple devices on an isolated subnet is best understood as ________. (ID-NTIA-195)
A. iSCSI
B. SAN
C. FTP
D. FCoE
E. NAS
280. A technician is configuring a new email server and needs to modify DNS records. Which of the following records should the technician update to ensure email functions as expected? (ID-NTIA-262)
A. MX
B. AAAA
C. CNAME
D. SRV
281. Sanuja wants to set an IP address to a specific MAC address on a host machine. Which of the following commands should he use? (ID-NTIA-205
A. nslookup
B. dig
C. arp
D. ipconfig
282. Which utility is shown in the following figure (portions of which have been obscured for this question)? (ID-NTIA-375)
A. netstat
B. nbtstat
C. nslookup
D. pathping
283. A network administrator wants to ensure sensitive data is not exfiltrated from the system electronically. Which of the following should be implemented? (ID-NTIA-341)
A. AUP
B. DLP
C. NDA
D. SLA
284. Which of the following commands can Sanuja use to display the number of bytes that a Windows workstation has transmitted? (ID-NTIA-99)
A. ipconfig
B. netstat
C. traceroute
D. iptables
E. tcpdump
285. A network technician needs to distribute an updated OS for all network switches at company locations throughout the world. The technician wants to ensure file integrity since several locations do not have high-quality connectivity to the Internet. Which of the following methods should be used to distribute the images while ensuring integrity? (ID-NTIA-249)
A. Use an FTP server and provide the file hash.
B. Use a modem and dial-up connection.
C. Use an HTTP server to share the file.
D. Use a TFTP server and UDP protocol.
286. A network technician downloaded new firmware for a mission-critical firewall. Which of the following should the network technician do before installing the firmware? (ID-NTIA-138)
A. Verify file hash
B. Verify file version
C. Verify file date
D. Verify file size
E. Verify file type
Question 286 Explanation:File hash verifies to ensure the downloaded file is correct and complete. Companies like CISCO, IBM, HP, and Microsoft provides hash information on almost every downloadable update files.
287. Which of the following WAN technologies utilizes an optical SONET carrier and has a maximum bandwidth of 155.54Mbps? (ID-NTIA-498)
A. OC3
B. E3
C. DS3
D. T3
288. Which of the following wireless security protocols uses CCMP for encryption? (ID-NTIA-81)
A. 802.1X
B. WPA2
C. WEP
D. WPA
289. Which of the following is the correct port number for NTP? (ID-NTIA-220)
A. Port 25
B. Port 69
C. Port 123
D. Port 161
290. Which of the following is used to provide hot standby capabilities using paired routers? (ID-NTIA-512)
A. FTP
B. CARP
C. L2TP
D. PPTP
E. ISAKMP
Question 290 Explanation:Common Address Redundancy Protocol (CARP)
291. Which of the following must be implemented to share metrics between routing protocols within the same router? (ID-NTIA-224)
A. Route redistribution
B. Dynamic routes
C. DHCP
D. Routing table
E. Routing loop
292. Which of the following protocols are included in a Fibre Channel packet? (ID-NTIA-316)
A. Ethernet
B. None of the answers are correct.
C. TCP
D. IP
E. UDP
Question 292 Explanation:The Fibre Channel standard defines a unique, five-layer protocol stack that does not correspond to the OSI model layers.
293. Which of the following security threats relies primarily on user deception and misinformation? (ID-NTIA-459)
A. Man-in-the-middle attacks
B. DoS attacks
C. Rogue access points
D. Phishing
294. A network technician has deployed a new 802.11ac network and discovers some of the legacy POS equipment only supports WPA and 802.11a. Which of the following is the most secure method of connecting all devices while avoiding a performance impact to modern wireless devices? (ID-NTIA-283)
A. Connect the legacy devices with a PSK while the modern devices should use the more secure EAP.
B. Configure the APs to use LEAP authentication to support WPA rather than WPA2 for full compatibility.
C. Create two SSIDs, one to support CCMP-AES encryption and one with TKIP-RC4 encryption.
D. Configure modern devices under the 5GHz band while dedicating the 2.4GHz band to legacy devices.
295. A user calls the help desk for assistance with setting up a new SOHO router. The user has three employees who all have laptops that need to connect to the wireless network. The users need to have firewall rules allowing access to an internal server, but cannot be configured with static IP addresses. Which of the following BEST describes what the technician should implement? (ID-NTIA-399)
A. Additional lease time for the laptop computers
B. IP helper relay system for configuration hops
C. DHCP reservation for the laptops MACs
D. CNAME record in the users dynamic DNS accounts
296. An employee, who using a laptop connected to the wireless network, is able to connect to the Internet but not to internal company resources. A systems administrator reviews the following information from the laptop: (ID-NTIA-300)
IP: 192.168.1.100
Mask: 255.255.255.0
Router: 192.168.1.1
The administrator was expecting to see a network address within 10.100.0.0/23, which is consistent with the company’s wireless network. The network administrator verifies the company’s wireless network is configured and working properly. Which of the following is the MOST likely cause of this issue?
A. Wrong SSID
B. Channel overlap
C. Interference
D. Security type mismatch
297. A typical cell tower will have microwave and cellular antennas. Which of the following network topologies do these represent? Choose all the correct answers. (ID-NTIA-159)<
A. Mesh
B. Bus
C. Peer-peer
D. Point-to-multipoint
E. Ring
F. Point-to-point
298. How many bits are allocated to the host identifier in an IPv4 address on the 10.72.0.0/17 network? (ID-NTIA-72)
A. 15
B. 17
C. 8
D. 16
Question 298 Explanation:An IP address has 32 bits. In this example, if 17 bits are allocated to the network identifier, 15 bits are left for the host identifier.
299. A VPN concentrator is an advanced type of which of the following devices? (ID-NTIA-88)
A. Gateway
B. Switch
C. Bridge
D. Router
300. Log files show the admin user has logged into a public-facing device on several occasions in the evening. None of the technicians admit to doing any after-hours work, and the password has been changed several times but failed to prevent the logins. Which of the following should be the NEXT step to attempt to harden the device? (ID-NTIA-285)
A. Upgrade the firmware.
B. Disable unused ports.
C. Reset the two-factor token.
D. Disable virtual ports.
301. Which of the following is an invalid MAC address? (ID-NTIA-487)
A. 44:98:3E:F8:33:23
B. AA:CE:58:FD:90:08
C. 94:9E:FE:EE:8C:DF
D. 56:AD:BX:89:55:54
302. Which of the following is an object held within an MIB? (ID-NTIA-276)
A. OUI
B. SNMP agent
C. OTDR
D. OID
E. SNMP trap
F. SNMP host
Question 302 Explanation:Object Identifier
303. A network technician receives reports indicating some users are unable to gain access to any network resources. During troubleshooting, the technician discovers the workstations have an IP address of 169.254.x.x. Which of the following is the most likely cause? (ID-NTIA-302)
A. Expired IP address
B. Rogue DHCP server
C. Misconfigured VLSM
D. Exhausted dynamic scope
Question 303 Explanation:The 169.254.x.x is part of Automatic Private IP Addressing (APIPA).
304. A technician is sent to a remote office to set up a device to connect to the Internet. The company standards document requires stateful inspection. Which of the following should the technician install? (ID-NTIA-403)
A. Bridge
B. Multiplayer switch
C. Firewall
D. Router
305. Two computers are connected to a multilayer switch, and both can access the corporate file server. The computers cannot talk to one another. Which of the following is most likely the cause? (ID-NTIA-400)
A. Bad port
B. Duplex/speed mismatch
C. Crosstalk
D. ACL misconfiguration
306. A systems administrator has recently purchased and installed a large electronic signage screen for the company’s parking garage. The screen’s management software was installed on a server with public IP address to allow remote management. The systems administrator is now troubleshooting an issue with the screen displaying unknown, random, and inappropriate messages. Which of the following is most effective in resolving this issue? (ID-NTIA-349)
A. Replacing the management software’s self-signed certificate with a valid certificate
B. Changing the management software’s default credentials
C. Changing the management software’s default port
D. Disabling unnecessary services from the server and management software
307. Review the following figure. Note that each store-and-forward switch (SANUJA_01, SANUJA_02, and SANUJA_03) has three connected node ports and one port for switch-to-switch connections. All node ports and links are configured for half-duplex communication. The switch-to-switch links are configured for full-duplex communication. Which of the following statements about the switched network is true? (ID-NTIA-327)
A. There is one collision domain for this network.
B. There are 3 collision domains, one for each switch-to-switch connection.
C. There are 9 collision domains, one for each half-duplex connection.
D. There are 12 collision domains, one for each switch connection.
Question 307 Explanation:All half-duplex port connections on a store-and-forward switch represent a different collision domain. Full-duplex connections aren’t subject to collisions, so they do not define separate collision domains.
308. Which of the following technologies is typically associated with virtual PBX services? (ID-NTIA-89)
A. Round-robin DNS
B. Voice over IP
C. Quality of service
D. CARP
309. A technician is investigating an issue related to a single host that is unable to access the Internet. The technician records the following information: Host IP 169.254.1.10. The network IP address range on the DHCP server is 10.10.5.2-10.10.5.250 with a default gateway 10.10.5.1 and a DNS of 8.8.8.8. Which of the following should the technician perform to troubleshoot the issue? (ID-NTIA-279)
A. Perform a traceroute command to identify the router that is not functioning.
B. Verify the host has physical connectivity and is on the correct VLAN.
C. Configure the DNS address in the DHCP scope to a 10.10.5.0/24 address.
D. Change the IP scope on the DHCP server to a public IP address range.
310. Due to a missing network device, 802.11n clients currently have no way to connect to the network. Which of the following devices should be implemented to let the clients connect? (ID-NTIA-409)
A. Range extender
B. Router
C. Access point
D. VoIP endpoint
311. The main server for your organization is located in Montreal, Quebec, Canada. You have an office in Calgary, Alberta, Canada. Which of the following virtual private network (VPN) connection should you use to connect the main server to the branch office in Calgary? (ID-NTIA-116)
A. Site-to-site
B. Branch-to-server
C. Host-to-host
D. Extranet
E. Host-to-site
312. A network technician needs to install an additional access point to the company’s wireless network. The network has two 802.11b access points. Which of the following channels should be used to allow the access point’s coverage areas to overlap? (ID-NTIA-466)
A. 2, 5, 10
B. 4, 8, 16
C. 1, 6, 11
D. 3, 13, 23
313.A web application is unable to authenticate customers so they can access their bills. The server administrator has tested the LDAP query but is not receiving results. Which of the following is the NEXT step the server administrator should take to correct the problem? (ID-NTIA-436)
A. Check port 636 to see if it is being blocked
B. Change service port 636 to port 389
C. Verify the browser is using port 443
D. Restart the web server
314. After installing a Linux web server, as a prudent IT Analyst, which of the following utilities should you use to check open ports that attackers might be able to penetrate? (ID-NTIA-47)
A. dig
B. nmap
C. tcpdump
D. iptables
315. If a workstation has the IP address 192.168.1.55/24, which of the following is the most likely IP address of the router that is connected to the workstation? (ID-NTIA-142)
A. 255 255 255.0
B. 192.168.1.1
C. 255 255 255.0
D. 192.168.0.55
E. 192.168.1.0
316. Which of the following is used to classify network data for the purpose of providing QoS? (ID-NTIA-223)
A. STP
B. DSCP
C. VLANs
D. SIP
Question 316 Explanation:Differentiated Services Code Point (DSCP)
317. Which of the following protocols is responsible for inserting the tags into frames that enable switches to forward them to the appropriate VLAN? (ID-NTIA-318)
A. IEEE 802.1q
B. IEEE 802.3x
C. IEEE 802.1X
D. IEEE 802.11ac
318. Which of the following is based entirely on using ICMP packets? (ID-NTIA-469)
A. Social engineering
B. Smurf attack
C. MITM
D. Buffer overflow attack
E. NMAP
319. In the following diagram, what is the type of optical fiber connector illustrated by I? (ID-NTIA-448)
A. MT-RJ
B. SC
C. ST
D. LC
320. Which of the following devices operates only at the physical layer of the Open Systems Interconnection (OSI) model? (ID-NTIA-64)
A. Switch
B. Bridge
C. Router
D. Hub
321. Which of the following is the range of IPv4 addresses that Automatic Private IP Addressing (APIPA) assigns to DHCP clients that cannot access a DHCP server? (ID-NTIA-69)
A. 169.254.0.0 to 169.254.255.255
B. 10.0.0.0 to 10.0.255.255
C. 192.168.0.0 to 192.168.0.255
D. 224.0.0.0 to 224.0.255.255
322. Which of the following datacenter security methodologies is most likely to remain usable during a company-wide network outage? (ID-NTIA-372)
A. Biometric scanners
B. Video surveillance
C. Motion detectors
D. Door locks
323. A company wants the public to be able to connect to the wireless network with minimal security, but not be able to connect to the private internal network. Which of the following firewall rules would BEST accomplish this? (ID-NTIA-464)
A. Content filtering on the wireless access point
B. Packet filtering on the wireless access point
C. Block traffic from the wireless access point
D. Allow traffic from the wireless access point
324. A user reports network resources can no longer be accessed. The PC reports a link but will only accept static IP addresses. The technician pings other devices on the subnet, but the PC displays the message Destination unreachable. Which of the following are most likely the causes of this issue? Choose all suitable answers. (ID-NTIA-389)
A. Crosstalk
B. VLAN mismatch
C. Damaged cables
D. Bent pins
D. Duplex mismatch
F. TX/RX reverse
325. Which of the following types of wiring faults cannot be detected by a wiremap tester? (ID-NTIA-19)
A. Transposed wires
B. Short circuits
C. Split pairs
D. Open circuits
Question 325 Explanation:It cannot detect split pairs because, in this fault situation, the pins are properly connected.
326. Which of the following DNS record types is an alias? (ID-NTIA-406)
A. PTR
B. MX
C. NS
D. SRV
E. CNAME
327. A company has hundreds of nodes on a single subnet and has decided to implement VLANs. Which of the following BEST describes the benefit of this approach? (ID-NTIA-218)
A. It provides multiple broadcast domains within a single collision domain
B. It provides a faster port to all servers
C. It provides multiple collision domains on one switchport
D. It segments broadcast domains in the network infrastructure
328. An administrator is receiving reports from an executive that the executive’s wireless access point loses the signal frequently, even though the WAP is on the executive’s desk. The office contains four other 802.11n access points. Which of the following would most likely correct interference problems in the executive’s office? (ID-NTIA-467)
A. Turn off as many lights in the executive’s office as possible to reduce interference
B. Change the channel on the access point to channel 11
C. Turn off SSID broadcasting for the executive’s access point
D. Replace the 802.11n access point in the office with an 802.11a access point
329. A network engineer is trying to determine where to place a firewall based on the flow of traffic. Which of the following types of documentation would assist the engineer in doing this? (ID-NTIA-293)
A. Change management
B. Rack diagram
C. Network diagram
D. Network configuration
330. Which of the following types of keys is included in a digital certificate? (ID-NTIA-18)
A. Privileged
B. Public
C. Preshared
D. Secured
E. Private
331. Which of the following protocols is used to transport outgoing mail across networks? (ID-NTIA-190)
A. IMAP
B. POP
C. LDAP
D. SMTP
332. NetBIOS protocol uses the port _____ general and port _____ for secure traffic. The answer is in the respective order. (ID-NTIA-139)
A. 80 , 443
B. 5060 , 3389
C. 161 , 162
D. 143 , 993
E. 5060 , 5061
Question 332 Explanation:Read the Common port numbers table at the bottom of this page.
333. All of the following items are fault tolerance mechanisms except ______________. (ID-NTIA-114)
A. RAID 1
B. SNMP
C. UPS
D. Clustering
Question 333 Explanation:Simple Network Monitoring Protocol (SNMP)
334. A vendor is installing an Ethernet network in a new hospital wing. The cabling is primarily run above the celling grid near air conditioning ducts and sprinkler pipes. Which of the following cable types is required for this installation? (ID-NTIA-255)
A. Single-mode
B. Plenum
C. Cat 7
D. PVC
335. A network administrator wants to narrow the scope of a subnet to two usable IP addresses within a class C network. Which of the following is the correct CIDR notation? (ID-NTIA-478)
A. 172.16.20.0/30
B. 10.10.50.0/30
C. 192.1.0.124/30
D. 192.168.0.192/24
D. 192.170.10.0/24
336. A technician logs onto a system using Telnet because SSH is unavailable. SSH is enabled on the target device, and access is allowed from all subnets. The technician discovers a critical step was missed. Which of the following would allow SSH to function properly? (ID-NTIA-340)
A. Update firmware
B. Generate new keys
C. Change default credentials
D. Perform file hashing
337. In the following diagram, what is the type of optical fiber connector illustrated by III? (ID-NTIA-449)
A. SC
B. MT-RJ
C. ST
D. LC
338. A vulnerability that would allow an unauthenticated, remote attacker to originate a DoS attack was found in a DHCP client implementation of a switch. Which of the following would best resolve the issue? (ID-NTIA-286)
A. Upgrade to the latest firmware
B. Review and modify the firewall rules
C. Generate new SSH keys
D. Verify the default passwords have been changed
339. Which of the following is a type of Out of Band Access; also known as out-of-band management? (ID-NTIA-216)
A. Using a secure SSH connection over the WAN link to connect to a server.
B. Implementing a modem on the AUX port to access a network device.
C. Telnet into the router over a secure VPN.
D. Accessing a DSL router via the console port.
340. A type of protocol used in network management systems for monitoring network-attached devices is called _________. (ID-NTIA-229)
A. SMB
B. SSL
C. RDP
D. SNMP
E. NTP
Question 340 Explanation:Simple Network Management Protocol (SNMP)
341. This function can be interfered with by a DNS poisoning attack. (ID-NTIA-96)
A. Name resolution
B. Password protection
C. IP address resolution
D. Network switching
342. A network technician is working on a new switch implementation to expand the network. Which of the following is the best option to ensure the implementation goes according to business requirements? (ID-NTIA-523)
A. NDA
B. SOP
C. AUP
D. SLA
Question 342 Explanation:Standard Operating Procedure (SOP)
343. A network technician configures a firewall’s ACL to allow outgoing traffic for several popular services such as email and web browsing. However, after the firewall’s deployment, users are still unable to retrieve their emails. Which of the following would BEST resolve this issue? (ID-NTIA-178)
A. Set the firewall to operate in transparent mode
B. Allow the firewall to accept inbound traffic to ports 21, 53, 69, and 123
C. Allow the firewall to accept inbound traffic to ports 80,110,143, and 443
D. Allow the firewall to accept inbound traffic to ports 25, 67,179, and 3389
344. The web server hosting sanuja.com has a secure web application called Senawa. You have set up the server with Senawa assigned to the port number 123456 for remote web access. In order for you to access Senawa from a remote office, which of the following URLs should you use? (ID-NTIA-127)
A. http://sanuja.com/123456
B. http://sanuja.com:123456
C. https://sanuja.com:123456
D. None of the answers are correct because you cannot assign random port numbers.
E. https://sanuja.com/123456
345. A network administrator wishes to ensure there are no unnecessary open communication paths into a server. Using a port scanner, the administrator finds that ports are reported as closed. Which of the following best explains this response? (ID-NTIA-366)
A. The ports are associated with deprecated services
B. The ports do not belong to a live system
C. The ports belong to an active system and are denying requests
D. The ports replied with a SYN/ACK response
346. A network technician needs to install a new access switch. After installing the new switch, the technician begins to move connections from the old switch to the new switch. The old switch used a GBIC with SC connectors, and the new switch uses an SFP with LC connectors. After connecting the SC connector to the SC- to-LC adapter and plugging it into the switch, the link does not come up as expected. Which of the following should a network technician perform next? (ID-NTIA-430
A. Replace SFP with a new one
B. Replace multimode with single-mode cable
C. Fall back to the old switch
D. Transpose the fiber pairs
347. What layer of the Open Systems Interconnection (OSI) model is responsible for translating and formatting information? (ID-NTIA-35)
A. Transport
B. Session
C. Presentation
D. Application
E. Network
F. Data link
G. Physical
348. A network administrator is adding a new WAN circuit from the ISP to a new building. In which of the following locations would the network administrator find the utility entry point? (ID-NTIA-260)
A. Demarc
B. IDF
C. Data tier
D. DMZ
349. The _____________ specifies the amount of time needed to restore a server from the most recent backup if it should fail. (ID-NTIA-109)
A. BCP
B. RTO
C. MIB
D. RAID
E. RPO
Question 349 Explanation:Recovery Time Objective (RTO)
350. An administrator is trying to retrieve management information from the network devices on their LAN. Which of the following monitoring resources provides the ability to collect this information encrypted over the network? (ID-NTIA-497)
A. IPSec
B. CDP
C. VTP
D. SNMPv3
Question 350 Explanation:Simple Network Management Protocol (SNMP)
351. Which utility is the easiest to use for identifying a malfunctioning router on a network? (ID-NTIA-45)
A. ifconfig
B. traceroute
C. netstat
D. ping
352. A network technician recently installed a new server on a network. The technician must ensure the server does not have any unnecessary services running. The IP address of the server is 204.211.38.50. Which of the following commands would allow the technician to make this determination? (ID-NTIA-433)
A. route
B. pathping
C. nmap
D. nslookup
353. An analyst is developing a proof of concept of a wireless-based attack as part of a penetration test against an organization’s network. As part of the attack, the analyst launches a fake access point matching the SSID of the organization’s guest access network. When a user connects to the fake access point, the analyst allows the traffic to flow through the access point to the legitimate site while the data traversing the network is logged for latest analysis and exploitation. Which of the following attacks has the analyst successfully performed in this scenario? (ID-NTIA-360)
A. VLAN hopping
B. Bluesnarfing
C. MAC spoofing
D. Session hijacking
E. Man-in-the-middle
354. Which of the following routing metrics is used to determine the path of a network that utilizes RIPv2 to route traffic? (ID-NTIA-130)
A. Speed
B. Ping time
C. Hop count
D. Distance
D. Bandwidth
355. Users have been experiencing connection timeout issues when using a web-based program. The network technician determines the problem happened due to a TTL setting that was set too low on the firewall. Which of the following BEST enabled the network technician to reach this conclusion? (ID-NTIA-387)
A. Reviewing a vulnerability scan
B. Reviewing a baseline report
C. Reviewing application logs
D. Reviewing SLA requirements
356. A gaming company released a new game that is downloadable on April 20, 2020. On the day of the launch, the majority of customers could not reach the company’s website. A message appears on their web browser stating the website is unavailable due to unusually high traffic. This technical issue is very similar to which of the following? (ID-NTIA-356)
A. Spoofing attack
B. MITM attack
C. DDoS attack
D. Wardriving
E. Session hijacking
Question 356 Explanation:What is described in the question is very similar to DDoS. A distributed denial-of-service (DDoS) attack is a malicious attempt to disrupt normal traffic of a targeted server typically by sending multiple requests for resources from the server. On the launch day, the customers trying to access the website at the same time created an identical situation to a DDoS attack.
357. A SAN serves out storage to a company’s virtual environment and provides low-level disk access. The company wants to use its existing IP network and equipment to access the virtual disks. Which of the following network connection types would BEST accomplish this task? (ID-NTIA-180)
A. Fibre Channel
B. InfiniBand
C. CIFS
D. iSCSI
358. A technician has installed a Linux server in the tax office. The server can access most of the resources on the network, but it cannot connect to another server that has a share for backup. The technician learns that the target server is on a different subnet. Which of the following tools should the technician use to ensure the Linux server can reach the backup location? (ID-NTIA-146)
A. ifconfig
B. dig
C. traceroute
D. route
E. netstat
359. Which of the following security methord is most likley effective against an insdier threat? (ID-NTIA-60)
A. Video surveillance
B. Biometrics
C. Motion detection
D. Smartcards
Question 359 Explanation:Other than video surveillance, all other options can be defeated by an insider. An insider threat is when someone already authorized to access organizations’ network infrastructure performs a nefarious act.
360. The _____________ protocol provides connection-oriented service with guaranteed delivery at the transport layer of the OSI model. (ID-NTIA-68)
A. UDP
B. HTTP
C. TCP
C. IP
Question 360 Explanation:Transmission Control Protocol (TCP)
361. Which of the answers listed below refers to an ipconfig command parameter used for displaying the full TCP/IP configuration information for all adapters? (ID-NTIA-330)
A. -i address
B. eth_addr
C. -a
D. /all
362. Which of the following types of Secure Sockets Layer (SSL) virtual private network (VPN) connections provides the most comprehensive access to the remote network? (ID-NTIA-58)
A. SSL client
B. SSL tunnel
C. SSL portal
D. SSL gateway
363. Which of the following concepts would BEST describe when a company chooses to use a third-party vendor to host and administer a critical application? (ID-NTIA-440)
A. CASB
B. IaaS
C. PaaS
D. SaaS
Question 363 Explanation:Some argue for IaaS.
364. Which of the following are characteristics of jumbo frames? Choose all correct answers. (ID-NTIA-421)
A. MTU size greater than 1500
B. Commonly used on SAN
C. Commonly used on IaaS
D. MTU size greater than 10000
E. MTU size greater than 12000
365. In a standard Cisco network diagram, what component does the following symbol represent? (ID-NTIA-07)
A. A gateway
B. A switch
C. A hub
D. A router
366. Which of the following parameters enables you to specify the number of messages the ping tool transmits? (ID-NTIA-29)
A. -i
B. -t
C. -a
D. -n
367. A network administrator is going to be performing a major upgrade to the network. Which of the following should the administrator use in case of a failure? (ID-NTIA-442)
A. Business continuity plan
B. Rollback plan
C. Vulnerability report
D. Baseline report
Question 367 Explanation:It is NOT a business continuity plan because the best choice to have here is a rollback plan.
368. Which of the following best describes an exploit? (ID-NTIA-137)
A. A router with default credentials
B. An SNMPv1 private community
C. An open mail relay server
D. A privilege escalation script
369. A network technician is creating a new subnet for 488 host machines. The technician is told to use a class B address scheme when making the subnet and is instructed to leave as much room as possible for additional subnets of the same size. Which of the following subnets would fulfill these requirements? (ID-NTIA-354)
A. 192.168.25.0/24
B. 172.18.0.0/23
C. 10.5.4.0/22
D. 10.233.2.0/23
E. 172.16.0.0/22
370. A user checks an IP address using an external website. The address is different than the one the user sees when opening a command prompt and typing in ipconfig/all. The user does not understand why the two tools show different IP addresses. This is BEST explained by the interworking of ___________. (ID-NTIA-217)
A. public/private networks
B. packet flow
C. network devices
D. traffic-routing protocols
371. You were advised to set up a new storage area network for a business, but you must use the existing infrastructure. Which of the following storage standards should you use? (ID-NTIA-135)
A. InfinitiBand
B. Fibre Channel
C. iSCSI
D. NAS
Question 371 Explanation:Why not iSCSI? Because iSCSI is not a storage standard. ISCSI is a transport layer protocol and NAS is a storage standard.
372. A technician is trying to configure a previously owned WAP. The technician successfully logs into the administrative console and attempts to input the IP address on the WAP. However, the WAP is not accepting the command. Which of the following is causing the problem? (ID-NTIA-492
A. The WAP transmitter light is dim
B. The WAP antenna is damaged
C. The LWAPP image is installed on the WAP
D. The terminal emulation software is misconfigured
373. When a user swipes a smartcard through a reader to log on to a Windows RDP session, which of the following actions is the user performing? (ID-NTIA-85)
A. Authentication
B. Authorization
C. Accounting
D. Auditing
374. Select all statements that apply to Telnet. (ID-NTIA-228)
A. It cannot be used on modern Windows computers.
B. Encrypts network connection.
C. It does not provide authentication.
D. Provides username & password authentication.
E ransmits data in an unencrypted form.
F. Enables remote login and command execution.
375. A technician wants to have the ability to transfer files from home to the company’s network on a regular basis. Which of the following is a remote access protocol the technician can utilize to bypass interactive user authentication by using a list of known host public keys? (ID-NTIA-201)
A. FTP
B. SCP
C. Telnet
D. TFTP
376. Multiple users in a small organization with 50 employees complained that they cannot access certain applications installed on an in-house server. What type of problem is this? (ID-NTIA-46)
A. A network-wide problem
B. A wide area newtwork problem
C. A system-wide problem
D. A shared resource problem
E. A user application problem
Question 376 Explanation:You may argue that this can be also classified as a user application problem because the users are complaining about not having access to applications. However, the it is not the best answer because if multiple users complain they cannot access an application that is installed on a central server, it is most likely an issue with the server, thus it is a network-wide problem.
377. What is the length of an IPv6 address? (ID-NTIA-482)
A. 64 bits
B. 256 bits
C. 32 bits
D. 128 bits
378. You were advised to fix a network issue at Foothills Hospital in Calgary. Which of the following documentation most likely contains the complete route of every cable run from the wall plate to the patch panel? (ID-NTIA-48)
A. Asset management files
B. Wiring schematic
C. Logical network diagram
D. Physical network diagram
E. Circuit diagrams
379. A new technician is connecting an access switch to a distribution switch uplink in a datacenter using fiber cables. Which of the following are transceivers the technician should use to perform this job? Select all correct answers. (ID-NTIA-380)
A. GBIC
B. LC
C. SC
D. SFTP
E. DB-9
F. RJ45
380. Which of the following cable types exclusively is used for Thin Ethernet network segments? (ID-NTIA-32)
A. RG-8
B. RJ-11
C. RJ-45
D. RG-58
381. You want to make phone calls using the Intenet via a standard analog phone. Which device enables you to use the Internet instead of the Public Switched Telephone Network (PSTN)? (ID-NTIA-133)
A. VoIP gateway
B. UTM appliance
C. VPN concentrator
D. Proxy server
382. Which of the following technologies allows more than two transceivers with an access point? (ID-NTIA-462)
A. 802.1x
B. FIFO
C. WPA
D. MIMO
E. IPsec
Question 382 Explanation:multiple-input and multiple-output (MIMO)
383. Which of the following would require troubleshooting if a network connectivity problem originates from mismatched transceiver types? (ID-NTIA-237)
A. SFP
B. MDI-X
C. SPF
D. ASIC
E. GBIC
384. A network administrator needs to install a border device on the network that will help ensure FTP commands are not being sent in traffic communicating on port 25. What device will allow for deep packet inspection? (ID-NTIA-149)
A. Web proxy
B. Layer 3 switch
C. Layer 7 firewall
D. NAT
E. Protocol analyzer
385. Which of the following DNS record would you use if sanuja.com is exculsively hosted on a server that only has an IPv6? (ID-NTIA-123)
A. NS
B. TXT
C. MX
D. A
E. AAAA
Question 385 Explanation:Note AAAA record takes IPv6 host information.
386. Users report that the network is slow. Upon investigation, the technician notices all users are on one large subnet. Which of the following devices should be used to break up broadcast domains? (ID-NTIA-272)
A. Signal repeater
B. Layer 3 switch
C. Domain server
D. Bridge
E. Layer 2 switch
387. Users are reporting that all of a sudden some of the files stored on the remote file server share are becoming corrupted and cannot be opened. A technician is dispatched to the server room to troubleshoot. The technician verifies that no changes to the network infrastructure occurred recently. Which of the following tools is most likely to reveal why files are becoming corrupted? (ID-NTIA-499)
A. OTDR
B. Punch down tool
C. Environmental monitor
D. Cable tester
388. A typical modern VOIP phone is equipped with which type of connector? (ID-NTIA-10)
A. RJ45
B. MTRJ
C. F-type
D. RJ11
E. ST
389. When you accessed this website, https://sanuja.com is most likely using which port number on its the webserver? (ID-NTIA-263)
A. Port 80
B. Port 22
C. Port 110
D. Port 443
E. Port 110
Question 389 Explanation:HTTPS = Port 443
390. Review the following figure. How many collision domains and broadcast domains are there in the network diagram? (ID-NTIA-328)
A. There are nine collision domains and three broadcast domains.
B. There are seven collision domains and three broadcast domains.
C. There are three collision domains and one broadcast domain.
D. There are three collision domains and three broadcast domains.
E. There is one collision domain and one broadcast domain.
391. Which of the following connector types are associated with fiberoptic cables? Choose more than one answer. (ID-NTIA-57)
A. ST
B. RJ11
C. LC
D. RJ45
E. F-type
F. MTRJ
Question 391 Explanation:Types: straight tip (ST), local connector (LC), and mechanical transfer–registered jack (MTRJ).
392. A network technician is considering opening ports on the firewall for an upcoming VoIP PBX implementation. Which of the following protocols is the technician most likely to consider? Choose three answers. (ID-NTIA-335)
A. RTP
B. NTP
C. H.323
D. SIP
E. RDP
F. SMB
G PSec
H. ICMP
393. An administrator is redesigning a company’s network and wants to reduce the amount of hardware needed. Currently, all VLAN routing goes out a single switch interface to a router. Which of the following would reduce the number of devices in this configuration? (ID-NTIA-250)
A. Switch
B. Multilayer switch
C. Bridge
D. Next-generation firewall
394. Management at a company wants to increase the bandwidth available to users after receiving several complaints. A technician reports to management that 50% of the company bandwidth is being utilized by wireless devices outside the company’s property. Given budget constraints, which of the following solutions should the technician propose to management? (ID-NTIA-189)
A. Enable WPA and change the SSID
B. Have the ISP double the bandwidth
C. Move from WPA2 to WEP
D. Configure geofencing
395. A network administrator is installing a campus network of two routers, 24 switches, 76 APs, and 492 VoIP phone sets. Which of the following additional devices should the administrator install to help manage this network? (ID-NTIA-385)
A. Content filter
B. RADIUS server
C. Wireless controller
D. VoIP PBX
396. A network technician needs to monitor the traffic going to a mission-critical server in the datacenter. Which of the following is the best method to perform this? (ID-NTIA-186)
A. Periodically view the server logs
B. Use SQL injectors
C. Install an inline tap
D. Use port mirroring
E. Configure port aggregation
397. Which of the following protocols does the Ping utility use to exchange messages with another system? (ID-NTIA-03)
A. TCP
B. IGMP
C. ICMP
D. UDP
Question 397 Explanation:Ping operates by sending Internet Control Message Protocol (ICMP) echo request packets to the target host and waiting for an ICMP echo reply.
398. A technician is replacing a switch at a branch office and discovers the existing backbone cable does not fit in the new switch. The fiber patch panel has circular connections. The new switch has a transceiver that accepts a smaller square adapter of two strands. Which of the following patch cables would the technician need to complete the installation? (ID-NTIA-160)
A. ST to ST
B. LC to SC
C. SC to SC
D. LC to ST
E. SC to ST
399. A Toronto hockey facility requested a guest wireless access system. Owners want to issue their guests vouchers with WiFi access codes that include expirations (time limits). Which of the following is the best choice to meet this requirement? (ID-NTIA-121)
A. Captive portal
B. NAC
C. MAC filtering
D. WAP
E. Port security
400. Which user has requested the performance monitoring in the following figure (click on figure to enlarge)? (ID-NTIA-321)
A. root
B. gdm
C. sanuja
D. top
E. systemd
401. A network technician needs to configure a device with an embedded OS so it can be connected to a wireless handheld scanner. Which of the following technologies should be configured on the OS to create the wireless connection? (ID-NTIA-393)
A. Ad hoc
B. Ring
C. Partial mesh
D. Bus
402. Joe, an employee at a large regional bank, wants to receive company email on his personal smartphone and tablet. To authenticate on the mail server, he must first install a custom security application on those mobile devices. Which of the following policies would best enforce this requirement? (ID-NTIA-434)
A. Incident response policy
B. DLP policy
C. BYOD policy
D. Remote access policy
403. A content filter is set to analyze XML and JSON that users access from the Internet. At which of the following OSI (Open Systems Interconnection) layers is this analysis taking place? (ID-NTIA-441)
A. Layer 3
B. Layer 6
C. Layer 2
D. Layer 4
E. Layer 5
F. Layer 7
G. Layer 1
404. In which of the following ways does a DDoS attack differ from a spoofing attack? (ID-NTIA-355)
A. DDoS attacks are launched from multiple hosts
B. Spoofing attacks require physical presence
C. DDoS attacks target multiple networks
D. Spoofing attacks originate from a single host
405. Which encryption standard is used by CCMP? (ID-NTIA-110)
A. TKIP
B. RC4
C. AES
D. Kerberos
E. 802.1X
Question 405 Explanation:Advanced Encryption Standard (AES)
406. In the following diagram, what is the type of optical fiber connector illustrated by IV? (ID-NTIA-447)
A. SC
B. ST
C. MT-RJ
D. LC
407. Which of the following devices often provides diagnostic testing capabilities at the demarcation point of a leased line wide area network (WAN) service? (ID-NTIA-167)
A. Smart jack
B edia converter
C. SIP trunk
D. SONET
E AA server
408. A company decides to deploy customer-facing, touch-screen kiosks. The kiosks appear to have several open source service ports that could potentially become compromised. Which of the following is the MOST effective way to protect the kiosks? (ID-NTIA-131)
A. Create a new network segment with ACLs, limiting kiosks’ traffic with the internal network.
B. Create a secondary NAT and connect the kiosks on it hence limit kiosks’ ability to access the main network.
C. Enable switchport security on the ports to which the kiosks are connected to prevent network-level attacks.
D. Install honeypots on the network to detect and analyze potential kiosk attacks before they occur.
E. Install an IDS to monitor all traffic to and from the kiosks.
409. Which of the following command lines will produce the output shown in the figure? Click image to enlarge. (ID-NTIA-84)
A. ping 192.168.1.1 -t
B. ping 192.168.1.1 -l 2048 -t
C. ping 192.168.1.1 -l 2048 -n 6
D. ping 192.168.1.1 -n 2048
E. ping 192.168.1.1 -l 2048 -t 6
Question 409 Explanation:Size of the message: -l parameter = 2048 bytes
Number of messages: -n parameter = 6
410. A network administrator wants to increase the confidentiality of the system by hardening the authentication process. Currently, the users log in using usernames and passwords to access the system. Which of the following will increase the authentication factor to three? (ID-NTIA-361)
A. Enforcing a stronger password policy and using a hand geometry scan
B. Using a smart card and RSA token
C. Adding a fingerprint reader to each workstation and providing a RSA authentication token
D. Adding a fingerprint reader and retina scanner
411. Which of the following network topologies allows only communication to take place from one node at a time by passing a token around the network? (ID-NTIA-488)
A. Bus
B. Mesh
C. Ring
D. Star
412. A network technician is installing a new network switch in the MDF. The technician is using fiber to connect the switch back to the core. Which of the following transceiver types should the technician use? (ID-NTIA-453)
A. F-type
B. GBIC
C. BNC
D. MT-RJ
Question 412 Explanation:gigabit interface converter (GBIC)
413. Which of the following is a network device that is responsible for separating collision domains? (ID-NTIA-535)
A. Router
B. Modem
C. Hub
D. Switch
414. An administrator is troubleshooting a user’s intermittent wireless connectivity issue. Other users across the hallway can connect and use the wireless network properly. Upon inspection of the connection details, the administrator finds the following: (ID-NTIA-435)
SSID: SANUJA-WiFi
Signal: 5%
SNR: 2
Which of the following is most likely the cause of the poor wireless connection?
A. Latency
B. Incorrect antenna type
C. Channel overlap
D. Overcapacity
415. In Kerberos protocol, where is the Authenticating Service and Ticket Granting Service are held? (ID-NTIA-112)
A. RDP
B. Client terminal
C. KDC
D. Application server
Question 415 Explanation:Key Distribution Center (KDC)
416. The Chief Executive Officer’s (CEO’s) tablet cannot connect to the wireless network from the corner office. A network technician verified the tablet can connect to the wireless network in other areas of the building. The distance between the office and the 802.11ac WAP is 150ft (46m), and there are a few cubicles in between. Which of the following is the MOST likely cause of the tablet not connecting? (ID-NTIA-524)
A. Attenuation
B. Reflection
C. Absorption
D. Distance
E. Refraction
417. Which of the following technologies is used to attach multiple guest operating systems to a single physical network port? (ID-NTIA-307)
A. Virtual switch
B. FCoE
C. Fibre Channel
D. VPC
E. vSAN
418. Which of the following is the number of broadcast domain(s) that are created when using an unmanaged 12-port switch? (ID-NTIA-222)
A. 0
B. 6
C. 12
D. 2
E. 1
419. Lauren, a user, reports that her desktop phone is not working on one cable. However, that cable provides connectivity to her laptop. A technician determines PoE is not provided to the end device. Which of the following is most likely the cause? (ID-NTIA-271)
A. Open/short on the cable
B. Jitter
C. Transceiver mismatch
D. Crosstalk
420. Which of the following well-known ports do you use to configure outgoing mail on a POP3 email client? (ID-NTIA-01)
A. 110
B. 25
C. 80
D. 989
E. 143
421. Which of the following solutions will detect and disable a rogue access point? (ID-NTIA-460)
A. IDS
B. Port scan
C. IPS
D. Packet sniffer
Question 421 Explanation:Intrusion Prevention System (IPS); note it specially state detect and desable. IDS only detects and alerts but will not be able to disable.
422. A technician is responsible for configuring a new firewall. The hardware team has already installed, powered, and connected the system. Which of the following types of documentation should the technician utilize to complete the task? (ID-NTIA-404)
A. Network performance baseline
B. Logical and physical diagrams
C. Rack diagram
D. IDF/MDF documentation
423. Which of the following is not a load balancing mechanism? (ID-NTIA-30)
A. Server clustering
B. RAID 1
C. NIC teaming
D. Muti-ISP connections
E. DNS round robin
Question 423 Explanation:Redundant Array of Independent Disks (RAID) level 1 is a fault tolerance mechanism but does not provide load balancing.
424. An ISP technician gets a call from a business that just changed equipment but can no longer connect to the Internet. The technician checks the ARP table on the ISP switch, and there is no corresponding MAC address present. Instead, the entry is “Incomplete”. Which of the following could cause this condition? (ID-NTIA-348)
A. TX/RX reverse
B. Duplicate IP address
C. Duplex/Speed mismatch
D. VLAN mismatch
425. ____________ describes a system that prevents computers from logging on to a network unless they have the latest updates and antimalware software installed. (ID-NTIA-40)
A. RADIUS
B. LDAP
C. TKIP-RC4
D. NAC
Question 425 Explanation:Network Access Control (NAC)
426. Which of the following physical security controls is most likely to be susceptible to a false positive? (ID-NTIA-368)
A. Proximity reader
B. Identification card
C. Video camera
D. Biometric device
427. An office network consists of one two-port router connected to a 12-port switch. A four-port hub is also connected to the switch. On this particular network, which of the following is the number of collision domains that exist? (ID-NTIA-342)
A. 14
B. 12
C. 3<
D. 13
E. 15
428. A recently constructed building makes use of glass and natural light. Users in the building are reporting poor cellular connectivity and speeds. Which of the following is most likely the cause? (ID-NTIA-522)
A. Channel overlap
B. Absorption
C. Reflection
D. Frequency mismatch
429. You are on the website sanuja.com. Sanuja also owns sanuja.net and would also like to reach sanuja.com via alias sanuja.net. What type of DNS record should you create? (ID-NTIA-122)
A. PTR
B. A
C. CNAME
D. MX
E. MD
Question 429 Explanation:CNAME is a Canonical Name Record or Alias Record. A type of resource record in the Domain Name System (DNS), that specifies that one domain name is an alias of another canonical domain name.
430. A network technician receives a switch that is configured to support VLANs on its ports. At which of the following layers is this switch operating? (ID-NTIA-191)
A. Layer 2
B. Layer 3
C. Layer 1
D. Layer 4
431. Identification badges, key fobs, and mantraps all fall into which of the following categories of security devices? (ID-NTIA-17)
A. Asset tracking
B. Port security
C. Physical security
D. Data security
432. A content filter is set to analyze XML and JSON that users access from the Internet. At which of the following OSI layers is this analysis taking place? (ID-NTIA-132)
A. Layer 5
B. Layer 7
C. Layer 1
D. Layer 4
E. Layer 2
F. Layer 3
G. Layer 6
Question 432 Explanation:Layer 6 is the presentation layer.
433. Which of the following policies prohibits a network administrator from using spare servers in the datacenter to mine bitcoins? (ID-NTIA-383)
A. BYOD
B. MOU
C. AUP
D. NDA
434. A technician is reviewing network device logs in an attempt to trace an attack that occurred on the network. Which of the following protocols would affect whether or not the technician can properly trace the attack through the network using the logs? (ID-NTIA-531)
A. HTTP
B. SMTP
C. NTP
D. RDP
435. Sanuja has a separate guest network at his home with the SSID SanujaGuest. When a visitor connects to SanujaGuest, a web page is presented to the user asking for login credentials. What type of WiFi security is most likley being used? (ID-NTIA-364)
A. EAP-TLS
B. MAC filtering
C. Captive portal
D. WPA2
E. SSL certificate
436. A network administrator is testing connectivity at a new corporate site. The site has a wireless guest as well as a wired employee network. After verifying connectivity, the administrator checks link speeds by using a speed testing website. The speed testing website shows lower download and upload speeds for the wired network than the wireless network. Which of the following is the most likely explanation? (ID-NTIA-172)
A. The testing server for the wired network was farther away
B. There is less local congestion on the wireless network
C. The firewall is configured to throttle traffic to specific websites
D. The wireless access points were misconfigured
Question 436 Explanation:This question is extracted out of a real Network+ exam. The answer is contested by some experts.
437. Typically group membership is used in this security procedure. (ID-NTIA-111)
A. Accounting
B. Auditing
C. TGS
D. Authorization
E. Authentication
438. Which of the following physical LAN topologies requires the most cabling? (ID-NTIA-444)
A. WLAN
B. Star
C. Bus
D. Ring
439. After several changes to the network, a technician needs to ensure a client is checking for new hostname and IP pairings. Which of the following commands should the technician use to force new lookups? (ID-NTIA-210)
A. ipconfig /release
B. ipconfig /renew
C. ipconfig /flushdns
D. ipconfig /all
440. Which of the following security protocols can authenticate users without transmitting their passwords over the network? (ID-NTIA-31)
A. 802.1X
B. Radius
C. LDAP
D. TKIP
E. Kerberos
441. A computer lab on a campus network was recently reconfigured using recycled network cables. One of the 24 computers in the lab is unable to connect to the network after the upgrade. A network technician successfully uses the cable in question to connect directly to another computer. Which of the following is most likely the issue with the cable? (ID-NTIA-345)
A. The cable has bent pins
B. The cable is rollover cable
C. The cable is damaged
D. The cable is a Cat 5 cable
E. The cable is a crossover cable
442. Which of the following best describes the differences between VLAN hopping and session hijacking? (ID-NTIA-176)
A. VLAN hopping is a brute force attack executed to gain additional access. Session hijacking involves physically disrupting a network connection.
B. VLAN hopping involves overriding a user network connection to execute malicious commands. Session hijacking involves compromising a host to elevate privileges.
C. VLAN hopping is the act of exploiting poor VLAN tagging. Session hijacking is a web-based attack aimed at privilege escalation.
D. VLAN hopping involves the unauthorized transition from one VLAN to another to gain additional access. Session hijacking involves overriding a user’s web connection to execute commands.
443. Based on the Open Systems Interconnection (OSI) model, which of the following statement on broadcast and collision domains is true? (ID-NTIA-102)
A. Collision domains occur in layer 1 while broadcast domains occur in layer 2.
B. Broadcast domains occur in layer 1 while collision domains occur in layer 2.
C. Both broadcast and collision domains occur at layer 2.
D. It is impossible to have a collision domain in a wireless network infrastructure.
E. It is impossible to have a collision domain in a wired (LAN) network infrastructure.
444. In a standard Cisco network diagram, what component does the following symbol represent? (ID-NTIA-08)
A. Authentication server
B. VPN gateway
C. Secure server
D. HTTPS server
E. Encryption key
445. You work for a large organization and your company occupies several floors of a downtown office building. You were told one of the network printers is malfunctioning. Which documentation most likely contains the tracking information about the printer such as the physical location (floor number, room, etc)? (ID-NTIA-49)
A. Circuit diagrams
B. Physical network diagramC. Wiring schematic
D. Logical network diagram
E. Asset management files
446. Which of the following is the purpose of a VLAN? (ID-NTIA-513)
A. Allows another connection to the router
B. Decreases bandwidth on a network
C. Segments broadcast traffic
D. Increases port speed
447. In Windows Active Directory Domain Services (AD DS), which protocol is used for authentication of internal clients? (ID-NTIA-15)
A. Kerberos
B. RADIUS
C. EAP-TLS
D. WPA2
448. A secured government building that scans the faces of incoming people and compares them to a database of authorized entrants is using which of the following types of technology? (ID-NTIA-94)
A. Pattern recognition
B. Tamper detection
C. Biometrics
D. Face geometry
E. Geofencing
449. Manuja, a new employee within a department, cannot print to any of the printers in the department or access any of the resources that others can. However, he can access the Internet. The network engineer has confirmed that Manuja’s account has been set up the same as the others. There are no access lists restricting Manuja’s access. Which of the following could be the issue for this lack of access? (ID-NTIA-129)
A. VLAN mismatch
B. Spanning tree blocked ports
C. DHCP server issue
D. Duplex/speed mismatch
E. DNS server issue
450. A technician needs to order cable that meets 10GBaseT and fire safety requirements for an installation between a drop ceiling and a standard ceiling. Which of the following should the technician order to ensure compliance with the requirements? (ID-NTIA-432)
A. PVC Cat 7
B. PVC Cat 5
C. Plenum Cat 5e
D. Plenum Cat 6a
451. Your company has spare network equipment to be used in an emergency. In order to minimize downtime, which of the following actions should your IT department take? (ID-NTIA-163)
A. Store all spare equipment in a sepearete office building for extra protection.
B. Instead of replacing current units during failures, use parts from the spare units to fix the current unit.
C. Keep purchasing new spare equipment.
D. Do nothing and keep the spare nearby for an emergency.
E pdate the firmware and drivers on spare network equipment regularly.
Question 451 Explanation:Some companies have the bright idea of having spare units, but fail to update firmware and OS. When the spares are needed, technicians have to update the firmware before installing the replacement. In some cases, such as Windows Servers, which never have been updated may result in driver failure and may take several hours/days to get the system back in running. Always update your spares!
452. A network technician is building a network for a small office. The office currently has cable TV and now requires access to the Internet without adding any cabling other than what is already in place. Which of the following solutions should the technician install to meet these requirements? (ID-NTIA-362)
A. DSL modem
B. Wireless router
C. DOCSIS modem
D. Demarc
E. Access point
453. Which of the following provides two-factor authentication? (ID-NTIA-420)
A. Username + password
B. Fingerprint + retina scan
C. Key fob + ID card
D. Smart card + PIN
454. Which of the following command-line utilities is capable of performing the same basic function as traceroute or tracert? (ID-NTIA-44)
A. netstat
B. route
C. pathping
D. ping
455. Which of the following tools would be of help in troubleshooting wireless signal loss and low wireless network signal coverage? (ID-NTIA-235)
A. Logical network diagram
B. Network mapper
C. Protocol analyzer
D. WAP power level controls
456. A network technician receives a call from a branch office about a problem with its wireless connectivity. The user states the office is hosting a large meeting that includes some online training with local businesses. The guest users have all brought devices to connect to the guest network at the branch office. All users are connected to a single WAP and are reporting that connections keep dropping and network spends are unusable. Which of the following is the most likely cause of this issue? (ID-NTIA-424)
A. Overcapacity
B. DHCP exhaustion
C. Interference
D. Channel overlapping
Question 456 Explanation:DHCP exhaustion and overcapacity can be the right answer but overcapacity is the most likely reason.
457. A network technician is troubleshooting an issue routing TCP packets to an email server. At which of the following OSI layers is the issue occurring? (ID-NTIA-256)
A. Layer 7 – Application
B. Layer 6 – Presentation
C. Layer 3 – Network
D. Layer 4 – Transport
E. Layer 1 – Physical
458. The IT manager at a small firm is in the process of renegotiating an SLA with the organization’s ISP. As part of the agreement, the organization will agree to a dynamic bandwidth plan to provide 300 Mbps of bandwidth. However, if the ISP determines that a host on the organization’s internal network produces malicious traffic, the ISP reserves the right to reduce available bandwidth to 5 Mbps. Which of the following policies is being agreed to in the SLA? (ID-NTIA-174)
A. Throttling
B. Blocking
C. Session hijacking
D. Bandwidth quotas
E. Data usage limits
459.What is the width of a standard equipment rack in a datacenter? (ID-NTIA-52)
A. 16 inches
B. 19 inches
C. 12 inches
D. 24 inches
460. Which of the following is the best way to detect and discourage insider the threat on a large scale infrastructure such as government IT networks? (ID-NTIA-61)
A. Physical inspection of each site/workstation.
B. Perform frequent IT audits.
C. Configure advance intrusion detection and firewall rules on the main datacenter.
D. Perform frequent security and vulnerability updates.
E. Install and maintain advanced enterprise firewall applications.
Question 460 Explanation:Insider the threat is when someone who is already authorized to use organizations’ network infrastructure abuse the system. The best option in large scale operations such as government agencies is to perform frequent audits.
461.Which of the following VPN protocols establishes a secure session that can be initiated using a browser? (ID-NTIA-363)
A. SSL VPN
B. IPSec
C. PPTP
D. PTP
462. An employee reports an error when visiting a website using SSL, and a message is displayed warning of an invalid certificate. Which of the following could be occurring? (ID-NTIA-320)
A. DDoS
B. Phishing
C. OCSP stapling
D. Evil twin
E. MITM
463. A network engineer wants to segment the network into multiple broadcast domains. Which of the following devices would allow for communication between the segments? (ID-NTIA-219)
A. Layer 2 switch
B. Bridge
C. Load balancer
D. Layer 3 switch
464. An attacker has flooded the hardware tables of a switch to forward traffic to the attacker’s IP address rather than the default router. The traffic received is copied in real-time, and then forwarded to the default router transparently from the end-user perspective. Which of the following attacks are occurring in this scenario? Select all correct answers. (ID-NTIA-451)
A. ARP poisoning
B. Evil twin
C. Ransomware
D. DNS poisoning
E. Man-in-the-middle
F. Reflective
465. Which of the following is characterized by an attacker attempting to map out an organization’s staff hierarchy in order to send targeted emails? (ID-NTIA-472)
A. Privilege escalation
B. Whaling
C. Spear phishing
D. Impersonation
466. Which of the following syslog message severity levels indicates that the message is just informational? (ID-NTIA-97)
A. 7
B. 4
C. 2
D. 0
E. 6
467. A Windows workstation failed to obtain an IP address from the DHCP server. Which of the following IP address most likely assigned to this workstations’ port? (ID-NTIA-71)
A. 192.168.0.1
B. 192.168.1.1
C. 175.255.255.255
D. 169.254.54.5
E. 175.168.0.255
Question 467 Explanation:It within the APIPA range which is 169.254.0.1 through 169.254.255.254.
468. A technician is troubleshooting network connectivity issues with a remote host. Which of the following tools would BEST inform the technician of nodes between the client and the remote host? (ID-NTIA-422)
A. nslookup
B. netstat
C. ping
D. route
E. tracert
F. tcpdump
G. pathping
469. Which of the following types of attacks is characterized by encrypting data and locking out a user from access to certain data within a workstation? (ID-NTIA-184)
A. Spoofing
B. Ransomware
C. Phishing
D. Session hijacking
E. DDoS
470. A network technician is installing a new wireless network in a small office. Due to environmental concerns, the customer wants the network to run exclusively on the 5GHz frequency. Which of the following wireless technologies should the technician install to best meet this requirement? Choose all correct answers. (ID-NTIA-439)
A. Z-Wave
B. 802.11g
C. 802.11n
D. 802.11ac
E. 802.11b
471. An organization recently installed a firewall on the network. Employees must have access to their work computer from their home computer. In which of the following ways should the firewall be configured? (ID-NTIA-515)
A. Allow TCP port 3389 inbound
B. Allow TCP port 3389 outbound
C. Allow UDP port 3389 outbound
D. Allow UDP port 3389 inbound
472. ____________ is the configuration that disables the NAT feature on the modem and allows a router to function as a DHCP server without an IP Address conflict. (ID-NTIA-175)
A. Double NAT
B. DOCSIS
C. ADSL
D. Jumbo frame
E. Bridge mode
473. A network room that is equipped with a fingerprint scanner that authenticates the user at the entrance is using which of the following types of technology? (ID-NTIA-14)
A. Pattern recognition
B. Biometrics
C. Tamper detection
D. Single sign-on (SSO)
E. Hand geometry
474. Which of the following best describes SNMP? (ID-NTIA-115)
A. Remote connection
B. Fault tolerance
C. Distributed server system
D. Site-to-site VPN
E. Network management
Question 474 Explanation:Simple Network Management Protocol (SNMP)
475. Windows remote access users with smartcards can be authenticated via which of the following protocols? (ID-NTIA-39)
A. MS-CHAPv2
B. CHAP
C. EAP
D. WEP
E. PAP
Question 475 Explanation:Extensible Authentication Protocol (EAP)
476. Which of the following devices are most often responsible for 802.1q tagging? Choose all correct answers. (ID-NTIA-438)
A. Router
B. IPS
C. Switch
D. Hub
E. IDS
F. Network tap
477. All users on a specific network segment report losing access to the wired network. During troubleshooting, the network administrator observes link lights on the workstations. When physically reviewing each switch, the network administrator changes the switch view settings to Activity and sees that all port lights remain solid green. Which of the following is most likely causing this issue? (ID-NTIA-501)
A. Power failure
B. STP convergence
C. Broadcast storm
D. Excessive bandwidth usage
478. Which of the following syslog message severity levels indicates that a system is unusable? (ID-NTIA-80)
A. 1
B. 4
C. 3
D. 2
E. 0
Question 478 Explanation:Code 0 is the most severe.
479. You are tasked with creating a network that will accomplish the following requirements for company A. (ID-NTIA-508)
Requirements:
– The remote Sales Team must be able to connect to the corporate network.
– Each department must have ONLY two PCs and a server.
– Each department must be segmented from each other.
– The following VLANs have been designed:
— VLAN 2 Finance
— VLAN 12 Sales
— VLAN 22 Human Resources (HR)
– Routing for VLAN 12 is implemented on the router. Routing for VLAN 2 and VLAN 22 is on the switch.
According to the following network diagram for Company A, where should the router be palced? Click on the image to enlarge.
A. C6
B. 5
C. C8
D. C7
E. C10
480. Which of the following is not a protocol operating at the network layer of the Open Systems Interconnection (OSI) model? (ID-NTIA-63)
A. IMAP
B. IGMP
C. IP
D. ICMP
481. Disk striping with distributed parity is used in which RIAD level? (ID-NTIA-105)
A. RAID 1
B. RAID 10
C. RAID 0
D. RAID 5
482. A network technician sets up a new schedule on the backup server. Management has informed the technician that a full backup does not need to be completed every day. The technician sets up weekly full backups. Which of the following should the technician configure for the remaining days to MINIMIZE the daily backup size? (ID-NTIA-207)
A. Differential
B. Snapshots
C. Incremental
D. Replica
483. The NetBIOS is part of which layer in the Open Systems Interconnection (OSI) model? (ID-NTIA-74)
A. Data Link
B. Physical
C. Presentation
D. Transport
E pplication
F. Network
G. Session
484. A technician is working on a new machine that has been procured for testing and development. The machine will run a hypervisor and host several operating systems of various types so the development team can test the company’s applications in a variety of environments. The technician wants the virtual machines to be available to communicate with each other without leaving the hypervisor. Which of the following is the best solution to the problem? (ID-NTIA-525)
A. The technician should add a route in each virtual machine to the default gateway.
B. The technician should connect the machine to its own separate switch.
C. The technician should configure a virtual switch.
D. The technician should set up individual routes between the machines.
485. What cloud service provides hardware (such as servers) and preconfigured operating systems (OS) by enableing you to select the OS you want to install? (ID-NTIA-119)
A. SaaS
B. Hosted
C. PaaS
D. VPN
E. IaaS
Question 485 Explanation:Platform-as-a-service (PaaS) is a type of cloud computing offering in which a service provider delivers a platform to clients, enabling them to develop, run, and manage business applications without the need to build and maintain the infrastructure such software development processes typically require.
486. Clients are connected to a switch on the gigabit Ethernet interface; the ISP is connected to the Serial 0 interface. When the router configuration is complete and client devices are reconfigured, all clients report that they are unable to connect to the Internet. Which of the following is the MOST likely reason? Answer the question based on the following IP address information. (ID-NTIA-332)
Gigabit Ethernet 1 Interface: 10.10.0.1/24
Serial 0 Interface: 10.10.0.253/30
A. The router was configured with an incorrect IP address
A. The router was configured with an incorrect loopback address
C. The router was configured with an incorrect subnet mask
D. The router was configured with an incorrect default gateway
487. Users have been experiencing slow network response times, and management has asked the network technician to provide evidence of network improvement. After optimizing the network, which of the following would be required? (ID-NTIA-346)
A. Change management
B. Physical diagram
C. IDF/MDF documentation
D. Performance baseline
488. Which of the following protocols do most man-in-the-middle attack (MITM) attacks utilize? (ID-NTIA-179)
A. SIP
B. FTP
C. ARP
D. SCP
489. Which of the following is BEST for providing real-time equipment theft alerts to the security staff? (ID-NTIA-532)
A. Smart card reader
B. Motion detection
C. Asset tracking tags
D. Biometric locks
490. A standard network rack is typically ruled vertically using which of the following measurements? (ID-NTIA-21)
A. Units
B. Millimeters
C. Number of screw holes
D. Inches
E. Centimeters
Question 490 Explanation:Rack diagrams use vertical measurement called units, each of which is 1.75 inches.
491. Which of the following wireless security protocols was substantially weakened by its initialization vector? (ID-NTIA-170)
A. WEP
B. WPA
C. WPA2
D. PEAP
Question 491 Explanation:Wired Equivalent Privacy (WEP)
492. When speaking with a client, an employee realizes a proposed solution may contain a specific cryptographic technology that is prohibited for non-domestic use. Which of the following documents or regulations should be consulted for confirmation? (ID-NTIA-306)
A. Data loss prevention
B. International export controls
C. Remote access policies
D. Incident response policy
E. Licensing restrictions
493. Which of the following is created on a 48-port switch with five active VLANs? (ID-NTIA-309)
A. 240 usable IP addresses
B. 240 private networks
C. 5 collision domains, 48 segments
D. 48 networks, 5 segments
E. 48 collision domains, 5 broadcast domains
494. In which IPv4 class is the address 127.0.0.1 found? (ID-NTIA-70)
A. Class A
B. Class C
C. Class D
D. None of the classes
E lass B
Question 494 Explanation:Address 127.0.0.1 is the designated IPv4 local loopback address, and as such, it is reserved.
495. Management has requested that services be available within 72 hours of a disaster. Budget is a major concern. A contract is signed with a company that has plenty of space, and the technician will have the option of putting infrastructure equipment in place. Which of the following best describes this business continuity strategy? (ID-NTIA-413)
A. Full backup
B. Warm site
C. Incremental backup
D. Differential backup
D. Cold site
F. Hot site
496. A network engineer is designing a new IDF in an old building. The engineer determines the equipment will fit in a two-post rack, and there is power available for this equipment. Which of the following would be the FIRST issue to remediate? (ID-NTIA-151)
A. Airflow and cooling
B. UPS capability
C. Circuit labeling
D. Power redundancy
497. A user wants to send information and ensure that it was not modified during transmission. Which of the following should be implemented? (ID-NTIA-516)
A. CHAP
B. MS-CHAP
C. Digital signatures
D. MAC filtering
498. What is the correct crimp out sequence of a cross-over pin out T568B RJ45 jack? (ID-NTIA-506)
A. White/Orange, Orange, White/Brown, Blue, White/Blue, Green, White/Green, Brown
B. White/Orange, Orange, White/Green, Blue, White/Blue, Green, White/Brown, Brown
C. White/Blue, Orange, White/Green, Blue, White/Orange, Green, White/Brown, Brown
D. White/Green, Green, White/Orange, Blue, White/Blue, Orange, White/Brown. Brown
D. White/Green, Green, White/Blue, Blue, White/Orange, Orange, White/Brown. Brown
Question 498 Explanation:You should also know the 568A: White/Green, Green, White/Orange, Blue, White/Blue, Orange, White/Brown. Brown. The 568B is more commonly used.
499. When configuring a new switch in a packet-switched network, which of the following helps protect against network loops? (ID-NTIA-395)
A. Flood guard
B. DHCP snooping
C. Spanning tree
D. BPDU guard
500. A user reports difficulties connecting a PC to a wired network. The PC connects to an IP phone, which is working correctly. A network technician can verify that other devices successfully connect to the phone. At which of the following layers of the OSI model is the problem MOST likely located? (ID-NTIA-367)
A. Application
B. Network
C. Transport
D. Physical
501. Which of the following is used to define the duration during which a client can use an IP address? (ID-NTIA-244)
A. DHCP timer
B. IP helper
C. MAC reservation
D. Pool
E. Lease time
502. While logged into a financial application, a user gets errors when trying to write to the database. The network administrator is not familiar with the application and how it communicates with the database. Which of the following documentation types should the network administrator use to troubleshoot the data flow? (ID-NTIA-477)
A. Logical diagram
B. Change management log
C. Network baseline
D. Physical diagram
503. A technician is sent to a remote office to set up a device to connect to the Internet. The company standards document requires stateful inspection. Which of the following should the technician install? (ID-NTIA-519)
A. Managed switch
B. Router
C. Bridge
D. IDS
D. Firewall
504. Which of the following occurs when antenna gain is increased on an access point? (ID-NTIA-463)
A. Cell size increases
B. Throughput decreases
C. Attenuation increases
D. Connection speeds decrease
505. A network administrator wants to monitor traffic by deploying MIBs. Which of the follow network monitoring resources would be used? (ID-NTIA-454)
A. Packet sniffer
B. DCCP
C. SNMP
D. SCTP
Question 505 Explanation:Simple Network Management Protocol (SNMP)
506. Tenants access multiple wireless networks in a building. Users report intermittent connectivity. Which of the following is the most likely cause of the problem? (ID-NTIA-511)
A. The SSIDs are incompatible and should be renamed.
B. The users have incompatible wireless network cards and should upgrade.
C. The channels are overlapping with other wireless networks and should be changed.
D. The default idle period for logoff is too short and should be changed to a longer limit.
507. A server with Microsft Windows Server Datacentre edition is set up as a Domain Controller and primary gateway between all computers and devices within the LAN infrastructure. Which of the following networking devices offers the ability to increase both performance and security? (ID-NTIA-136)
A. Wireless controller
B. Enterprise firewall
C. IDS
D. Load balancer
E. Proxy server
508. A network technician is assisting a user who has relocated to a newly constructed office space. The user has no network connectivity. A cable tester was used on the port and is reporting that the pairs are open. Which of the following should be used to remedy this problem? (ID-NTIA-298)
A. Punchdown tool
B. Loopback adapter
C. Multimeter
D. Tone generator
509. Which of the following protocols is related to the term open relay? (ID-NTIA-414)
A. NTP
B. POP3
C. LDAP
D. IMAP
E. SMTP
510. Which of the following telecommunications components is all but obsolete and is found only in old, analog telephone installations? (ID-NTIA-50)
A. CMTS
B. 110 block
C. Patch panel
D. Fiber distribution panel
E. 66 block
511. A technician is sent to troubleshoot a faulty network connection. The technician tests the cable, and data passes through successfully. No changes were made in the environment, however, when a network device is connected to the switch using the cable, the switchport will not light up. Which of the following should the technician attempt next? (ID-NTIA-324)
A. Change the switch
B. Modify the speed and duplex
C. Plug in to another port
D. Replace the NIC
512. Which of the following attack types involves the modification of a legitimate software product? (ID-NTIA-91)
A. Wardriving
B. Evil twin
C. Social engineering
D. Logic bomb
513. A large company uses an AAA server to manage network device access. The engineers can use their domain credentials to access all other servers. Currently, the network engineers cannot access the AAA server using domain credentials, but they can access it using a local account. Which of the following should the engineers update? (ID-NTIA-267)
A. Server IP address
B. ACAS+ server time
C. Host-based firewall settings
D. DNS SRV record
514. If you are a System Administrator for a critical high availability IT infrastructure, which of the following types of patches you would least likely to install unless there is a specific reason to do so? (ID-NTIA-79)
A. Feature change
B. Operating system update
C. Driver update
D. Vulnerability patch
E OIS firmware patch
Question 514 Explanation:If the system is working as it should, updating drivers may lead to instability. Unless there is a bug in the drivers, most IT professionals will postpone for forgo driver updates. Feature updates typically do not lead to instabilities. Other listed updates above are critical to keeping all systems running smoothly.
515. A company wishes to allow employees with company-owned mobile devices to connect automatically to the corporate wireless network upon entering the facility. Which of the following would best accomplish this objective? (ID-NTIA-312)
A. Pre-shared key
B. MAC filtering
C. Open wireless
D. Geofencing
516. Which of the following ports is used by HTTPS by default? (ID-NTIA-05)
A. 25
B. 110
C. 443
D. 990
E. 80
517. Which of the following is the prefix for a link-local IPv6 address? (ID-NTIA-458)
A. FEEF:/12
B. 2FFE::/16
C. FE80::/10
D. FF00::/8
518. A network technician is installing a new wireless network for a client. The client has experienced issues with other building tenants connecting to the wireless network and utilizing the bandwidth. The client wants to prevent this from happening by using certificate-based authentication. Which of the following technologies should the network administrator implement? (ID-NTIA-386)
A. EAP-TLS
B. AES-CCMP
C. WPA-PSK
D. WEP-TKIP
519. Which of the following addresses is a class B private address? (ID-NTIA-504)
A. 162.17.43.22
B. 132.216.14.184
C. 152.119.25.213
D. 172.23.226.34
520. Which of the answers listed below refer to iptables? Choose all correct answers. (ID-NTIA-329
A. Packet capturing utility
B. MS Windows command-line tool
C. Packet tracing utility
D. Packet filtering utility
E. Linux command-line tool
521. Which of the following answers refers to a system containing mappings of domain names to various types of data, such as numerical IP addresses? (ID-NTIA-225)
A. SQL
B. DHCP
C. DNS
D. TCP/IP
522. What is the function of the tool shown in the following figure? (ID-NTIA-78)
Image Credit: https://www.tequipment.net/ FlukeNetworks52801009.html
A. By touching the end of the tool to a copper cable, you can detect and measure the electrical current flowing through it.
B hen you place the tool at one end of a wire, it generates a tone that can be detected at the other end.
C. To attach a bulk cable end to an RJ45 connector, you use the tool to squeeze the connector closed, forcing the wire ends to contact the connector’s pins.
D. By connecting the clips to pins in a punchdown block, you can access telephone circuits in order to test them or place telephone calls.
Question 522 Explanation:This is known as lineman’s handset or more commonly known as a butt-set.
523. Which layer of the Open Systems Interconnection (OSI) model is responsible for transmitting signals over the network medium? (ID-NTIA-23)
A. Presentation
B. Transport
C. Data link
D. Physical
E. Application
F. Network
Session
524. What is the fastest way for validating a digital certificate? (ID-NTIA-230)
A. OCSP
B. Key escrow
C. CSR
D. CRL
Question 524 Explanation:Online Certificate Status Protocol (OCSP)
525. Which of the following should be performed to verify that unnecessary services are disabled on all switches in an environment? (ID-NTIA-402)
A. Baseline review
B. Port scanning
C. Packet capturing
D. Log scanning
526. Answer the following question based on the network diagram below. Assuming all Workstations receives their internal IP from the DHCP server within the router, which of the following is the most likely IP address of Workstation 5? Click on the image if it is hard to read. (ID-NTIA-36)
A. 192.168.0.55
B. 192.168.0.1
C. 10.1.1.255
D. 10.1.0.255
E. 192.168.1.109
527. Which of the following security mechanisms dynamically assigns a Layer 2 address and restricts traffic only to that Layer 2 address? (ID-NTIA-162)
A. ACL
B. Sticky MAC
C. NAT
D. NAC
E. 802.1x
528. Which of the following commands enables you to view the ARP table stored in memory? (ID-NTIA-82)
A. arp -s
B. arp -t
C. arp -d
D. arp -c
E. arp -a
529. Which of the following communication media can carry many voice, data, and video channels simultaneously over multiple frequencies? (ID-NTIA-357)
A. Baseband
B. Analog modem
C. Broadband
D. CSMA
530. Which of the following commands displays all environment and shell variables? (ID-NTIA-415)
A. env
B. lsshell
C. ls
D. getargs
E. lsenv
531. According to the troubleshooting methodology, which of the following steps will help a technician gather information about a network problem? Choose all correct answers. (ID-NTIA-390)
A. Establish a theory of probable cause
B. Duplicate the problem
C. Implement preventive measures
D. Question users
E. Test solutionsF. Document findings
532. Which of the following 10 Gigabit Ethernet specifications calls for the use of copper cable? (ID-NTIA-42)
A. 10GBase-ER
B. 10GBase-LR
C. 10GBase-LX4
D. 10GBase-CX4
E. 10GBase-SR
533. Which of the following ports should a network technician open on a firewall to back up the configuration and operating system files of a router to a remote server using the fastest method possible? (ID-NTIA-426)
A. UDP port 53
B. TCP port 25
C. UDP port 69
D. UDP port 22
E. TCP port 22
534. A company has just refreshed the hardware in its datacenter with new 10G Ethernet switches. A technician wishes to set up a new storage area network but must use existing infrastructure. Which of the following storage standards should the technician use? (ID-NTIA-429)
A. Fibre Channel
B. InfiniBand
C. iSCSI
D. NAS
Question 534 Explanation:Some argue for iSCSI. Note the question refers to ‘storage standards’ not packets carriers
535. A company’s web-based application has a database that is set up for high availability in case of a failure. Which of the following is necessary to achieve this type of setup? (ID-NTIA-199)
A. A virtual IP pointing to the active DB
B. A private IP pointing to the web front end
C. A static IP pointing to the passive DB
D. A private IP pointing to the web proxy