Last year I published an article on home electrical wiring basics. When I looked back at that document, I realized that I have missed several aspects of electrical wiring. This article will complement the previous by expanding the subject matter. Continue reading Updating Electrical Components
Tag Archives: technology
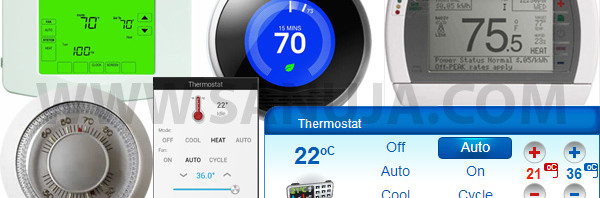
Choosing a thermostat
In most parts of the developed world, we live in houses that are at least ten years old (or often older). Hence homeowners spent their money on home improvements. One of the easiest ways to renovate your house is to replace the old units with new ones. Today I am going to discuss a simple item found in every Canadian household; the thermostat. Continue reading Choosing a thermostat
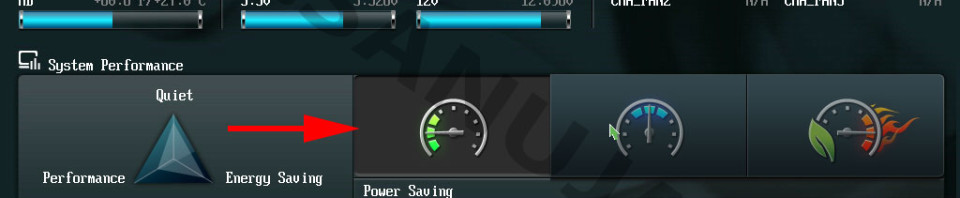
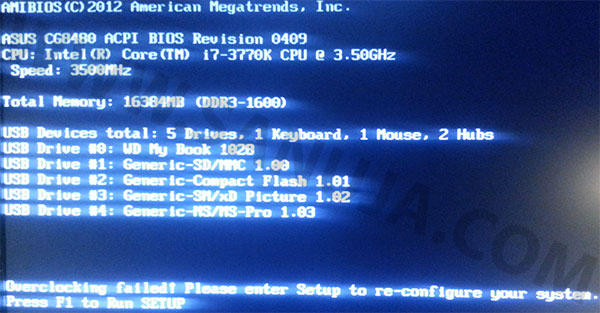
How to fix overclocking failed error
This is a well documented boot failure issue on most Asus, MSI and few other motherboards. When the issue arise, the message, “Overclocking Failed! Please enter setup to re-configure your system.” will be displayed on start up before the system goes into boot sequence. So, how can you fix this?
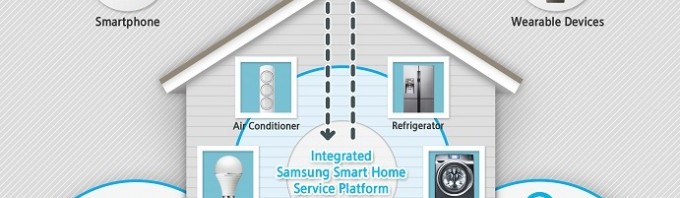
Cloud computing: a blessing and a curse
Right after the DOT-COM bubble began to shrink, a new concept of computing called cloud computing gave hope to a dying breed. It boosted the profits of entirely Internet based companies like Dropbox Inc. and opened the market for new Internet based companies. The next big step for this technology is the “smart home” which also referred to as “connected home”.
How to build a basic antenna
We use wireless devices to send and receive information without worrying about physical obstacles. In the old days, most consumer-grade wireless devices such as mobile phones, routers and RC controllers came with large antennas. Today some manufactures decided to go with internal or built-in antennas. This is not always beneficial to the consumer. For example, if you have a weak signal in an area, it would be difficult to change the position of the antenna because; you do not know where is it in the casing and you may not be able to place the device in a position. The solution is to add a external antenna.