This is part of the CCNA1 Introduction to Networks course. This page will be updated with texts in the future… for now, please refer to my lecture on my YouTube channel.
Category Archives: Computer Science
Computer Science (CS) and Information Technology (IT) related items will be posted under this category. Topics include, but not limited to, system administration, hardware/software troubleshooting, coding/programming (PHP, HTML, Java, Python, etc) and more.
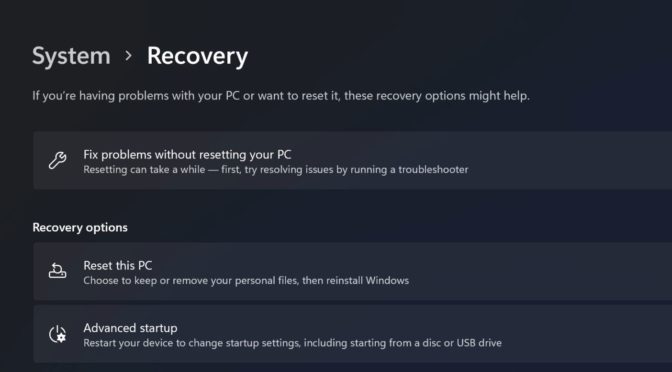
How to wipe your data on Windows 10 and 11
If you are selling your used PC (laptop/desktop) or you are returning your device to your organization, company or school, it is important to wipe and clear your personal data from the device to protect your privacy and security. The Windows 10 and Windows 11 Operating Systems (OS) have the built-in capabilities to help you do it. Continue reading How to wipe your data on Windows 10 and 11
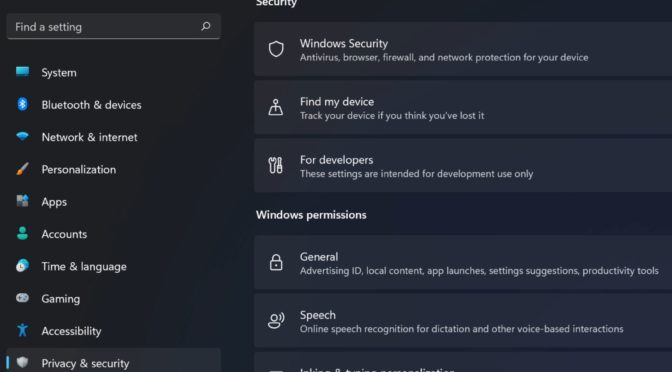
How to Disable Microsoft Telemetry in Windows 11, 10 & Server 2019
This article also applies to Microsoft Windows 10 and Windows Server 2019.
Microsoft collects data from their users through a program called telemetry system. They collect data on Windows Operating System, Microsoft programs and third-party programs. It also collects data on some user behaviour. They use this information to improve products and help diagnose issues as well as to recommend apps and features to the end user. Microsoft is not hiding anything from their end users but it requires the users to take action on their part to change limit or block telemetry system once the initial setup process is done.
Disabling or limiting telemetry on your system should not have any adverse impact on your user experience. There are multiple ways to update your preferences on the telemetry system after the initial setup. If you would like to see a detailed demonstration of the following items, please watch my YouTube video.
Continue reading How to Disable Microsoft Telemetry in Windows 11, 10 & Server 2019
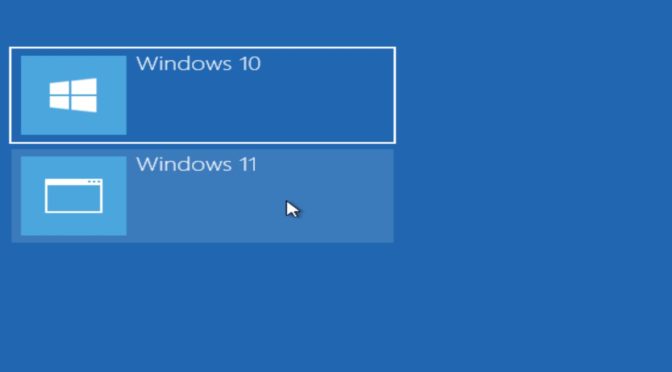
How to configure dual boot with Microsoft Windows
As Windows 11 is being rolled out, some advanced users may want to run both Windows 10 and Windows 11 on the same computer before completely moving on to Windows 11. In this tutorial, we will configure dual boot with Windows 10 and Windows 11 Operating Systems (OS). Here is how you can configure a dual boot system using a Personal Computer (PC) that already has been upgraded to Windows 11.
Important!
You can also follow these steps to install:
-Windows 7, 8, or 11 on a Windows 10 installed computer
-Windows 7 or 8 on a Windows 11 installed computer
-Windows 7, 10, or 11 on a Windows 8 installed computer
The installation instructions should work on all desktop versions of Windows (Home, Professional, Enterprise)
The instructional video on how to install dual boot with Windows 10 on a Windows 11 computer can be found on YouTube. Continue reading How to configure dual boot with Microsoft Windows
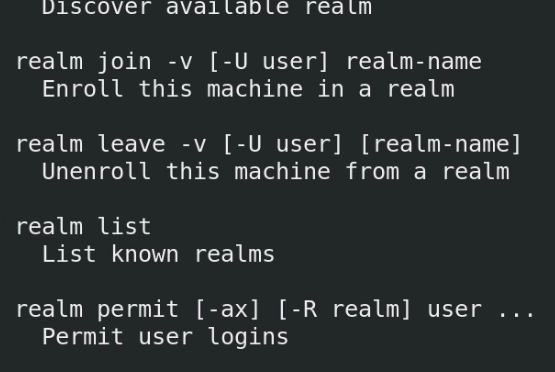
How to join Linux to a Windows AD-DS Domain
Linux (Unix-like) servers are very popular choice in the tech world. A majority of web and file servers are hosted on Unix and Unix-like operating systems. At the same time Microsoft Windows Servers are utilized by all major organization for its easy-to-use features such as Active Directory Domain Services, also simply known as, domains. If you have a mixed environment with both Linux and Windows servers or Linux desktops (end devices) and Windows servers, you need to be able to Windows domain join Linux machines. This is a step-by-step guide on how to domain join a CentOS, which is similar to RHEL (Red Hat Enterprise Linux) to an existing Windows Domain.
Continue reading How to join Linux to a Windows AD-DS Domain